Which of the following best describes the key elements of a successful information security program?
A security manager is looking at a third-party vulnerability metric (SMITTEN) to improve upon the company's current method that relies on CVSSv3. Given the following:
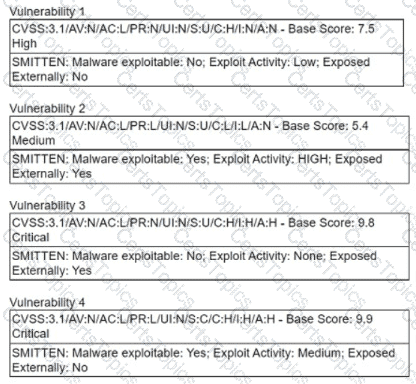
Which of the following vulnerabilities should be prioritized?
Which of the following best describes the key goal of the containment stage of an incident response process?
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to The site 's standard VPN logon page is
Which of the following is most likely true?