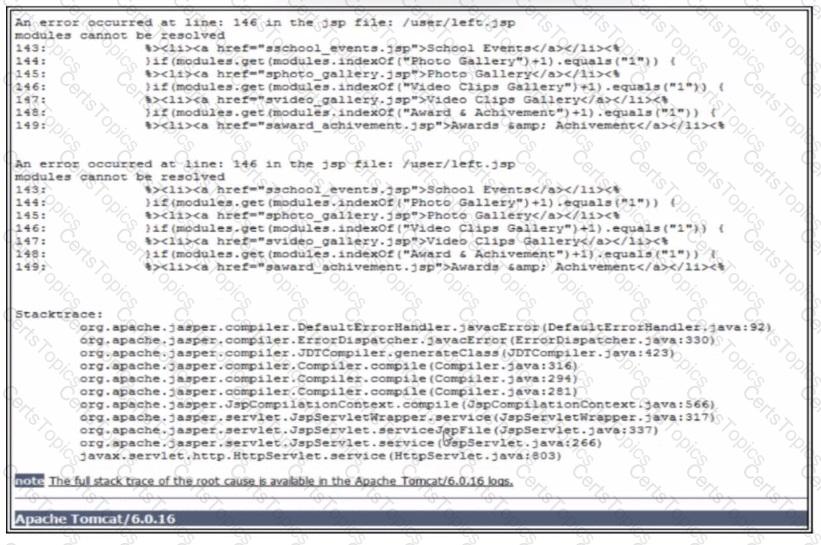
Refer to the exhibit. A penetration test performed against a web application generates the error message. Which two pieces of information are exposed? (Choose two.) Q Internal paths of the web server
A security operations team is transitioning from alert-driven investigations to a mature threat hunting program. The team wants to focus on detecting adversaries who intentionally evade signature-based tools and traditional SIEM alerts by using legitimate credentials and native system utilities. Which hunting focus best supports this objective?
Refer to the exhibit.

A company went through several rounds of restructuring and the previous security team has been let go A new engineer joins and rediscovers all the tools thatthe previous team left behind.One of the tools Is a Bash script related to monitoring AWS accounts for threats What is the purpose of the script?
A threat hunter usesCisco Secure Network Analytics (Stealthwatch)to identify potential command-and-control traffic. Which characteristic MOST strongly indicates beaconing behavior?