After completing a threat hunt that uncovered previously undetected credential abuse, the SOC wants to ensure long-term improvement in detection and response capabilities. Which action BEST represents the final and most critical phase of the threat hunting lifecycle?
A threat hunter wants to detect credential dumping attempts that bypass traditional malware detection. Which telemetry source is MOST effective for this purpose?
The security team detects an alert regarding a potentially malicious file namedFinancial_Data_526280622.pdfdownloaded by a user. Upon reviewing SIEM logs and Cisco Secure Endpoint, the team confirms that the file was obtained from an untrusted website. The hash analysis of the file returns an unknown status. Which action must be done next?
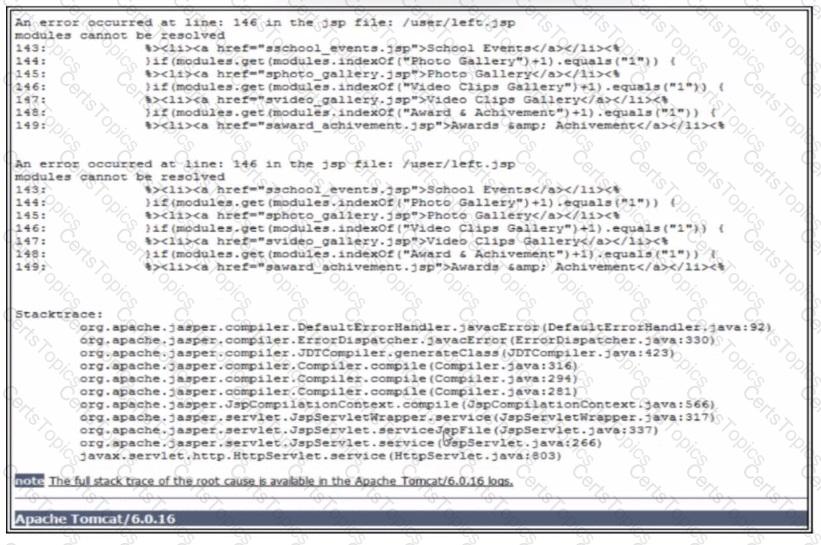
Refer to the exhibit. A penetration test performed against a web application generates the error message. Which two pieces of information are exposed? (Choose two.) Q Internal paths of the web server
A security operations team is transitioning from alert-driven investigations to a mature threat hunting program. The team wants to focus on detecting adversaries who intentionally evade signature-based tools and traditional SIEM alerts by using legitimate credentials and native system utilities. Which hunting focus best supports this objective?
Refer to the exhibit.

A company went through several rounds of restructuring and the previous security team has been let go A new engineer joins and rediscovers all the tools thatthe previous team left behind.One of the tools Is a Bash script related to monitoring AWS accounts for threats What is the purpose of the script?
A threat hunter usesCisco Secure Network Analytics (Stealthwatch)to identify potential command-and-control traffic. Which characteristic MOST strongly indicates beaconing behavior?
According to the MITRE ATT&CK framework, how is the password spraying technique classified?
A mature SOC notices that several incidents over the past year involved attackers abusing legitimate administrative tools rather than deploying custom malware. Leadership asks the threat hunting team to improve detection coverage in a way that increases attacker cost rather than relying on easily replaceable indicators. Which detection strategy best aligns with this objective?
Refer to the exhibit.
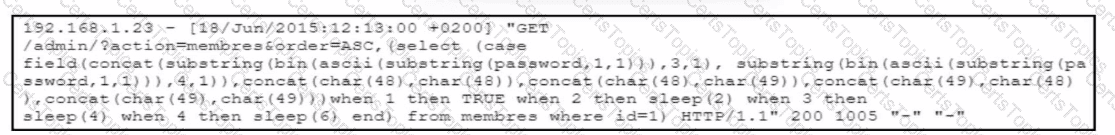
The cybersecurity team at a company detects an ongoing attack directed at the web server that hosts the company website. The team analyzes the logs of the web application firewall and discovers several HTTP requests encoded in Base64. The team decodes the payloads and retrieves the HTTP requests. What did the attackers use to exploit the server?
A SOC repeatedly discovers similar attacker behaviors during separate hunts, indicating recurring detection gaps. What process change MOST effectively prevents rediscovery of the same threats?
During multiple intrusions, analysts observe that attackers consistently perform internal reconnaissance before privilege escalation, avoid noisy exploitation, and limit actions to business hours of the victim’s region. Why is this observation important for attribution?
During a structured hunt, analysts using Cisco SIEM tools complete hypothesis testing and confirm malicious activity. What is the NEXT step in the Cisco threat hunting lifecycle?
A security team wants to create a plan to protect companies from lateral movement attacks. The team already implemented detection alerts for pass-the-hash and pass-the-ticket techniques. Which two components must be monitored to hunt for lateral movement attacks on endpoints? (Choose two.)
A SOC using Cisco security technologies wants to measure the success of its threat hunting program over time. Which metric BEST reflects increased threat hunting maturity?
Refer to the exhibit.
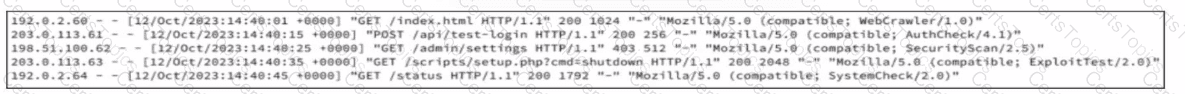
A company recently was breached and decided to improve their security posture going forward. A security assessment was ordered, specifically intended to test weak points exploited during the breach. A security analyst reviews server logs to identify activities related to the aforementioned security assessment. Which entry suggests a delivery method associated with authorized assessment?
A security architect is designing a threat model for a multi-tier cloud application that includes public APIs, backend microservices, and an identity provider. The goal is to identify how an attacker could chain multiple weaknesses together to achieve account takeover and data exfiltration. Which threat modeling technique is MOST appropriate?