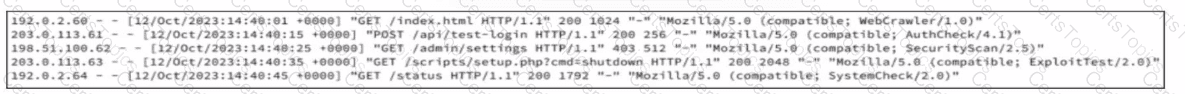
The correct answer isAttack trees. Attack trees are uniquely suited for modelingmulti-step adversary behavior, which is essential when analyzing complex attack chains such as account takeover followed by data exfiltration.
Attack trees begin with ahigh-level attacker goal(for example, “Exfiltrate customer data”) and then break that goal into multiple branches representing different paths an attacker could take. These paths can include credential compromise, API abuse, privilege escalation, lateral movement, and persistence. This structure mirrors how real adversaries think and operate.
Option A (STRIDE) is useful for identifying broad threat categories—such as spoofing, tampering, or information disclosure—but it does not naturally capturesequential attack paths. Option B (CVSS) focuses on vulnerability severity scoring, not adversary behavior. Option D (DREAD) assesses risk impact but does not visualize how attacks unfold across systems.
For threat hunters and defenders, attack trees provide ashared mental modelbetween architects, SOC teams, and red teams. They directly inform detection engineering by highlightingcritical choke pointswhere attacker behavior must occur, such as token abuse, API enumeration, or anomalous role assumption in cloud environments.
In modern cloud security, where breaches often involvemultiple low-severity issues chained together, attack trees offer far greater strategic value than component-by-component analysis. They also align closely withMITRE ATT&CK mapping, enabling defenders to translate threat models into actionable hunts.
Thus, optionCis the most appropriate and professionally validated answer.