What should you do to meet the user profile requirements?
Which settings should you configure to meet the performance requirements?
Which two actions should you perform to meet the security requirements for Defender for Endpoint? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
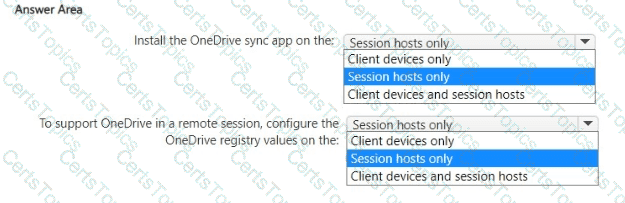
What should you do to meet the application requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.