Fortinet Related Exams
NSE6_FML-6.4 Exam







Refer to the exhibit.
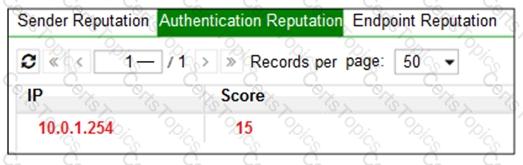
Which configuration change must you make to block an offending IP address temporarily?
Refer to the exhibit.
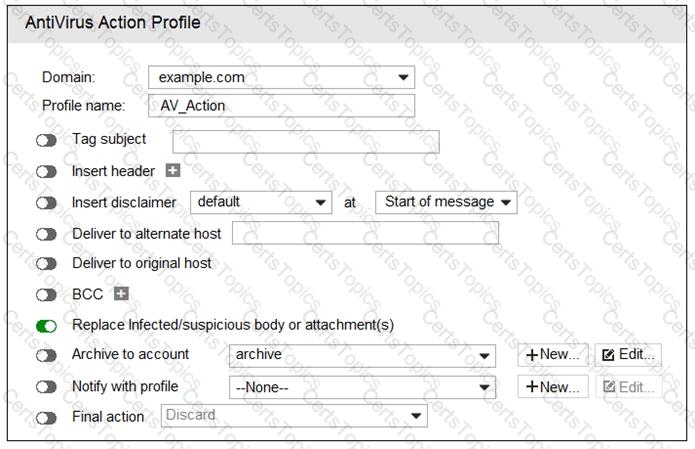
What are two expected outcomes if FortiMail applies this antivirus action profile to an email? (Choose two.)
Refer to the exhibit.
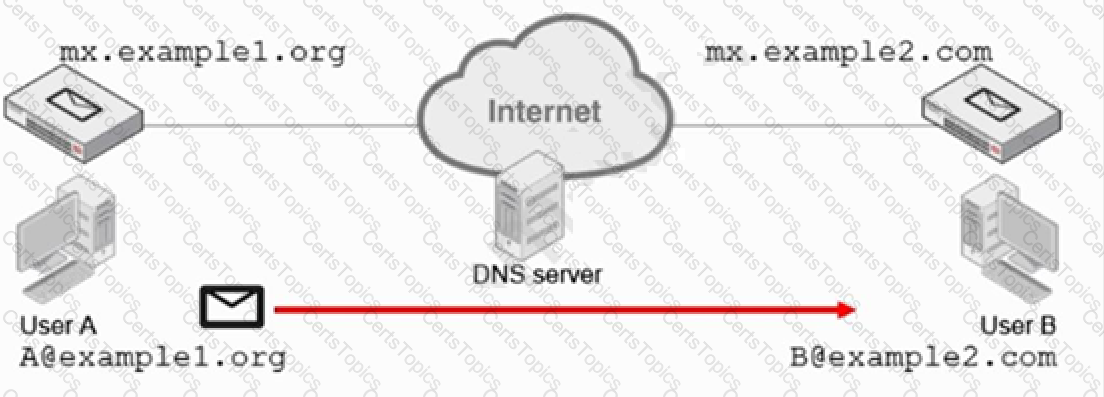
Which two statements about email messages sent from User A to User B are correct? (Choose two.)