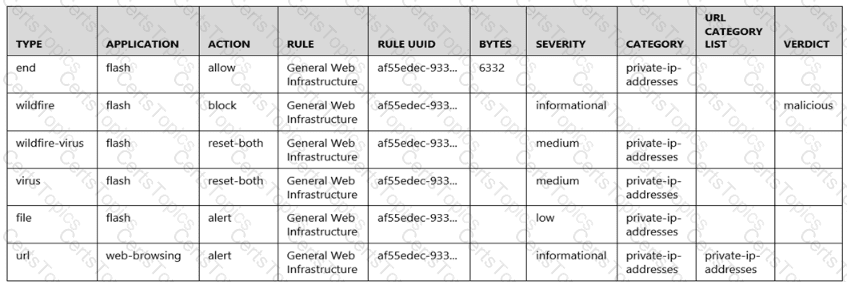
Given the following snippet of a WildFire submission log, did the end user successfully download a file?
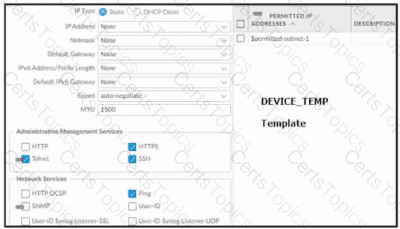
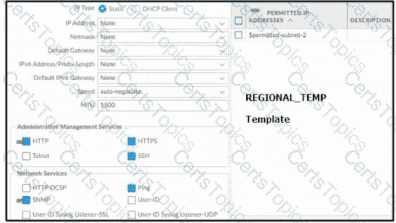
An engineer configures a new template stack for a firewall that needs to be deployed. The template stack should consist of four templates arranged according to the diagram

Which template values will be configured on the firewall If each template has an SSL/TLS Service profile configured named Management?
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
How should an administrator enable the Advance Routing Engine on a Palo Alto Networks firewall?
An administrator has been tasked with configuring decryption policies,
Which decryption best practice should they consider?
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow. Upon opening the newly created packet capture, the administrator still sees traffic for the previous filter.
What can the administrator do to limit the captured traffic to the newly configured filter?
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user.
What configuration change is necessary to implement this troubleshooting solution for the user?
View the screenshots
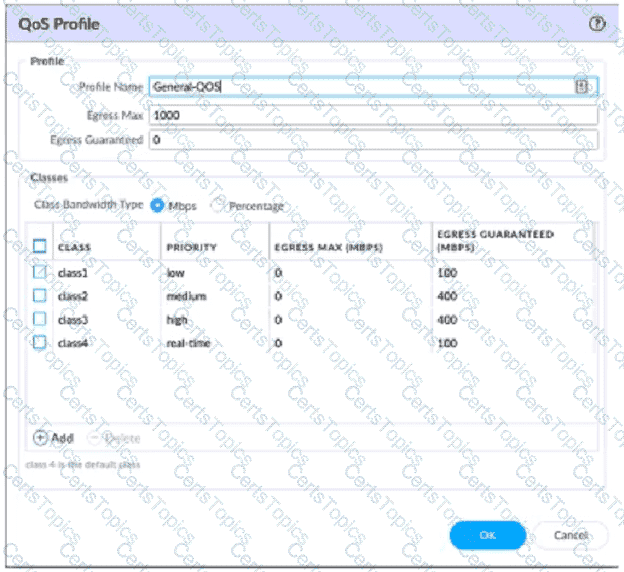
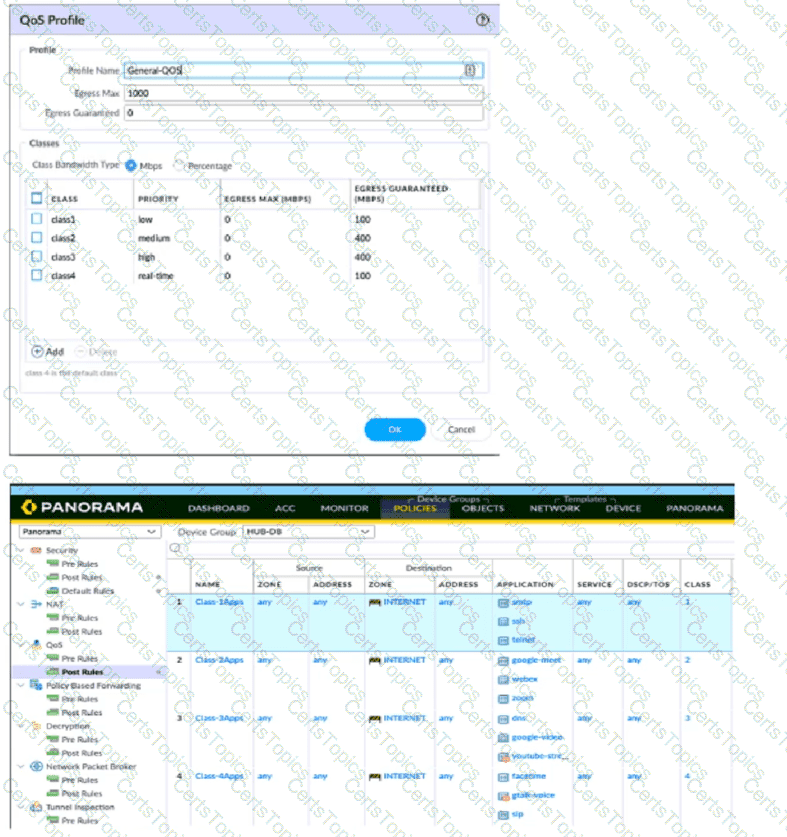
A QoS profile and policy rules are configured as shown. Based on this information which two statements are correct?
A firewall administrator has been tasked with ensuring that all Panorama configuration is committed and pushed to the devices at the end of the day at a certain time. How can they achieve this?
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
What can be used as an Action when creating a Policy-Based Forwarding (PBF) policy?
A company wants to use GlobalProtect as its remote access VPN solution.
Which GlobalProtect features require a Gateway license?
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two.)
Which link is responsible for synchronizing sessions between high availability (HA) peers?
When configuring explicit proxy on a firewall, which interface should be selected under the Listening interface option?
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD.
Which three dynamic routing protocols support BFD? (Choose three.)
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?
A network security engineer needs to ensure that virtual systems can communicate with one another within a Palo Alto Networks firewall. Separate virtual routers (VRs) are created for each virtual system.
In addition to confirming security policies, which three configuration details should the engineer focus on to ensure communication between virtual systems? (Choose three.)
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory.
What must be configured in order to select users and groups for those rules from Panorama?
A firewall administrator has been tasked with ensuring that all firewalls forward System logs to Panorama. In which section is this configured?
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet.
Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
To ensure that a Security policy has the highest priority, how should an administrator configure a Security policy in the device group hierarchy?
What is the purpose of the firewall decryption broker?
An administrator plans to install the Windows-Based User-ID Agent.
What type of Active Directory (AD) service account should the administrator use?
An administrator has been asked to configure active/active HA for a pair of Palo Alto Networks NGFWs. The firewall use Layer 3 interfaces to send traffic to a single gateway IP for the pair.
Which configuration will enable this HA scenario?
As a best practice, logging at session start should be used in which case?
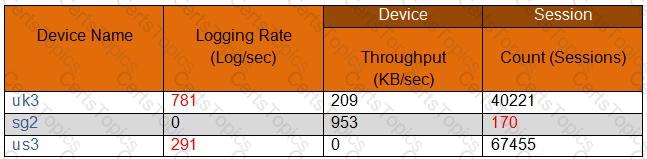
All firewall at a company are currently forwarding logs to Palo Alto Networks log collectors. The company also wants to deploy a sylog server and forward all firewall logs to the syslog server and to the log collectors. There is known logging peak time during the day, and the security team has asked the firewall engineer to determined how many logs per second the current Palo Alto Networking log processing at that particular time. Which method is the most time-efficient to complete this task?
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
For company compliance purposes, three new contractors will be working with different device-groups in their hierarchy to deploy policies and objects.
Which type of role-based access is most appropriate for this project?
Following a review of firewall logs for traffic generated by malicious activity, how can an administrator confirm that WildFire has identified a virus?
Which two scripting file types require direct upload to the Advanced WildFire portal/API for analysis? (Choose two.)
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
An administrator troubleshoots an issue that causes packet drops.
Which log type will help the engineer verify whether packet buffer protection was activated?
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
An administrator is informed that the engineer who previously managed all the VPNs has left the company. According to company policies the administrator must update all the IPSec VPNs with new pre-shared keys Where are the pre-shared keys located on the firewall?
Forwarding of which two log types is configured in Device > Log Settings? (Choose two.)
A security team has enabled real-time WildFire signature lookup on all its firewalls. Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
An administrator wants to use LDAP, TACACS+, and Kerberos as external authentication services for authenticating users. What should the administrator be aware of regarding the authentication sequence, based on the Authentication profile in the order Kerberos LDAP, and TACACS+?
An engineer needs to collect User-ID mappings from the company’s existing proxies. What two methods can be used to pull this data from third-party proxies? (Choose two)
Which is not a valid reason for receiving a decrypt-cert-validation error?
An engineer needs to configure a standardized template for all Panorama-managed firewalls. These settings will be configured on a template named "Global" and will be included in all template stacks.
Which three settings can be configured in this template? (Choose three.)
What are the two behavior differences between Highlight Unused Rules and the Rule Usage Hit counter when a firewall is rebooted? (Choose two.)
In which two scenarios is it necessary to use Proxy IDs when configuring site-to-site VPN tunnels? (Choose two.)
What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 10.1 version?
The UDP-4501 protocol-port is to between which two GlobalProtect components?
A firewall administrator is configuring an IPSec tunnel between a company's HQ and a remote location. On the HQ firewall, the interface used to terminate the IPSec tunnel has a static IP. At the remote location, the interface used to terminate the IPSec tunnel has a DHCP assigned IP address.
Which two actions are required for this scenario to work? (Choose two.)
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates.
What must occur to have Antivirus signatures update?
What happens when an A/P firewall pair synchronizes IPsec tunnel security associations (SAs)?
An engineer is configuring Packet Buffer Protection on ingress zones to protect from single-session DoS attacks.
Which sessions does Packet Buffer Protection apply to?
In the following image from Panorama, why are some values shown in red?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is currently processing traffic?
An administrator is building Security rules within a device group to block traffic to and from malicious locations.
How should those rules be configured to ensure that they are evaluated with a high priority?
A firewall engineer creates a NAT rule to translate IP address 1.1.1.10 to 192.168.1.10. The engineer also plans to enable DNS rewrite so that the firewall rewrites the IPv4 address in a DNS response based on the original destination IP address and translated destination IP address configured for the rule. The engineer wants the firewall to rewrite a DNS response of 1.1.1.10 to 192.168.1.10.
What should the engineer do to complete the configuration?
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
Which Panorama feature protects logs against data loss if a Panorama server fails?
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates.
Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
What type of NAT is required to configure transparent proxy?
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
A firewall engineer needs to update a company's Panorama-managed firewalls to the latest version of PAN-OS. Strict security requirements are blocking internet access to Panorama and to the firewalls. The PAN-OS images have previously been downloaded to a secure host on the network.
Which path should the engineer follow to deploy the PAN-OS images to the firewalls?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
In the New App Viewer under Policy Optimizer, what does the compare option for a specific rule allow an administrator to compare?
Which are valid ACC GlobalProtect Activity tab widgets? (Choose two.)
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an internal syslog server.
Where can the firewall engineer define the data to be added into each forwarded log?
Which two factors should be considered when sizing a decryption firewall deployment? (Choose two.)
Based on the images below, and with no configuration inside the Template Stack itself, what access will the device permit on its management port?

Which two profiles should be configured when sharing tags from threat logs with a User-ID agent? (Choose two.)
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Link and Path Monitoring is enabled with the Failure Condition set to "any." There is one link group configured containing member interfaces ethernet1/1 and ethernet1/2 with a Group Failure Condition set to "all."
Which HA state will the Active firewall go into if ethernet1/1 link goes down due to a failure?'
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group.
What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
An administrator needs to identify which NAT policy is being used for internet traffic.
From the Monitor tab of the firewall GUI, how can the administrator identify which NAT policy is in use for a traffic flow?
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama? The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
A firewall administrator manages sets of firewalls which have two unique idle timeout values. Datacenter firewalls needs to be set to 20 minutes and BranchOffice firewalls need to be set to 30 minutes. How can the administrator assign these settings through the use of template stacks?
After implementing a new NGFW, a firewall engineer sees a VoIP traffic issue going through the firewall After troubleshooting the engineer finds that the firewall performs NAT on the voice packets payload and opens dynamic pinholes for media ports
What can the engineer do to solve the VoIP traffic issue?
Which two methods can be configured to validate the revocation status of a certificate? (Choose two.)
A company is expanding its existing log storage and alerting solutions All company Palo Alto Networks firewalls currently forward logs to Panorama. Which two additional log forwarding methods will PAN-OS support? (Choose two)
How can a firewall engineer bypass App-ID and content inspection features on a Palo Alto Networks firewall when troubleshooting?
An engineer is bootstrapping a VM-Series Firewall Other than the /config folder, which three directories are mandatory as part of the bootstrap package directory structure? (Choose three.)
Which protocol is natively supported by GlobalProtect Clientless VPN?
A firewall engineer creates a new App-ID report under Monitor > Reports > Application Reports > New Applications to monitor new applications on the network and better assess any Security policy updates the engineer might want to make.
How does the firewall identify the New App-ID characteristic?
When using certificate authentication for firewall administration, which method is used for authorization?
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)
A firewall engineer has determined that, in an application developed by the company's internal team, sessions often remain idle for hours before the client and server exchange any data. The application is also currently identified as unknown-tcp by the firewalls. It is determined that because of a high level of trust, the application does not require to be scanned for threats, but it needs to be properly identified in Traffic logs for reporting purposes.
Which solution will take the least time to implement and will ensure the App-ID engine is used to identify the application?
Which method will dynamically register tags on the Palo Alto Networks NGFW?
How does Panorama prompt VMWare NSX to quarantine an infected VM?
A firewall engineer creates a destination static NAT rule to allow traffic from the internet to a webserver hosted behind the edge firewall. The pre-NAT IP address of the server is 153.6 12.10, and the post-NAT IP address is 192.168.10.10. Refer to the routing and interfaces information below.
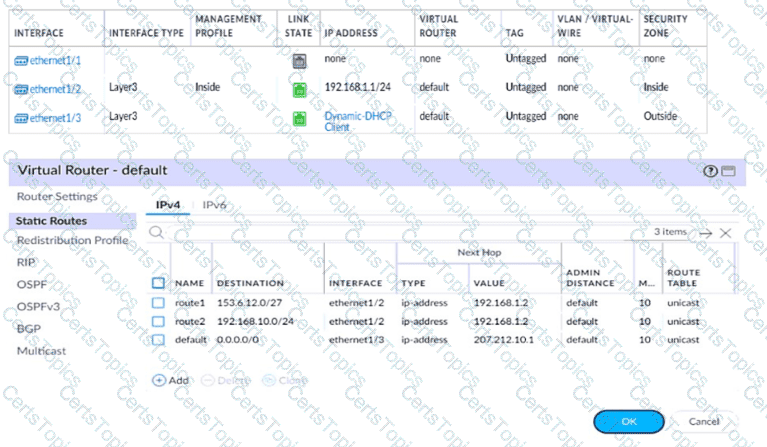
What should the NAT rule destination zone be set to?
An engineer troubleshoots a Panorama-managed firewall that is unable to reach the DNS servers configured via a global template. As a troubleshooting step, the engineer needs to configure a local DNS server in place of the template value.
Which two actions can be taken to ensure that only the specific firewall is affected during this process? (Choose two )
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is experiencing a failure of a monitored path?
A standalone firewall with local objects and policies needs to be migrated into Panorama. What procedure should you use so Panorama is fully managing the firewall?
What happens when the log forwarding built-in action with tagging is used?
What is the best definition of the Heartbeat Interval?
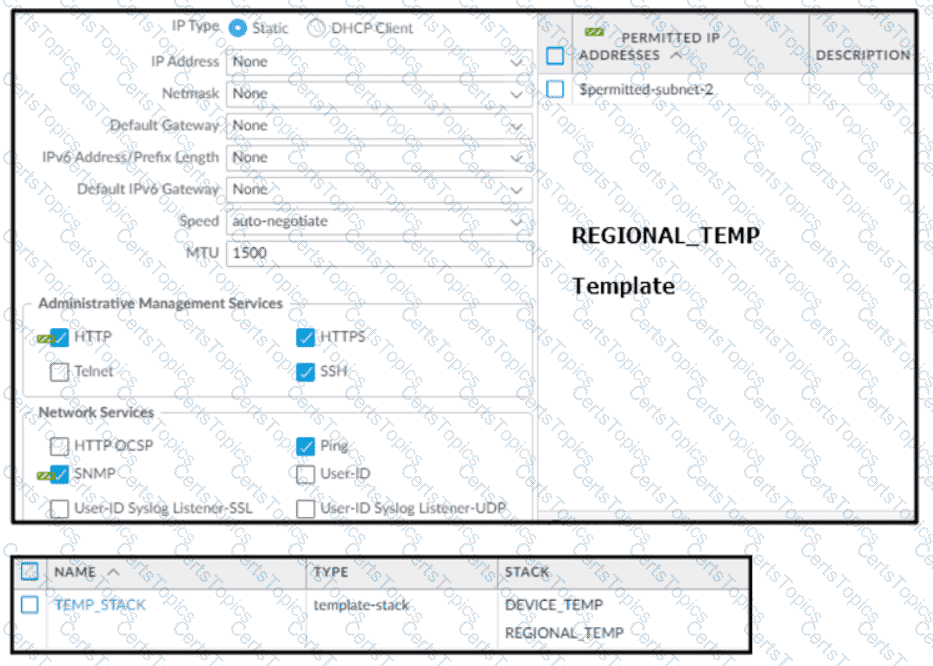
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
Which two items must be configured when implementing application override and allowing traffic through the firewall? (Choose two.)
Which translated port number should be used when configuring a NAT rule for transparent proxy?
An engineer configures a specific service route in an environment with multiple virtual systems instead of using the inherited global service route configuration.
What type of service route can be used for this configuration?
An administrator wants to configure the Palo Alto Networks Windows User-D agent to map IP addresses to u: ‘The company uses four Microsoft Active ‘servers and two Microsoft Exchange servers, which can provide logs for login events. All six servers have IP addresses assigned from the following subnet: 192.168.28.32/27. The Microsoft Active Directory in 192.168.28.22/128, and the Microsoft Exchange reside in 192,168.28 48/28. What the 0 the User
A firewall engineer at a company is researching the Device Telemetry feature of PAN-OS. Which two aspects of the feature require further action for the company to remain compliant with local laws regarding privacy and data storage? (Choose two.)
An administrator configures a site-to-site IPsec VPN tunnel between a PA-850 and an external customer on their policy-based VPN devices.
What should an administrator configure to route interesting traffic through the VPN tunnel?
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment
Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
A firewall administrator configures the HIP profiles on the edge firewall where GlobalProtect is enabled, and adds the profiles to security rules. The administrator wants to redistribute the HIP reports to the data center firewalls to apply the same access restrictions using HIP profiles. However, the administrator can only see the HIP match logs on the edge firewall but not on the data center firewall
What are two reasons why the administrator is not seeing HIP match logs on the data center firewall? (Choose two.)
The decision to upgrade PAN-OS has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when attempting the install.
When performing an upgrade on Panorama to PAN-OS. what is the potential cause of a failed install?
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
Which two profiles should be configured when sharing tags from threat logs with a remote User-ID agent? (Choose two.)
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
What must be taken into consideration when preparing a log forwarding design for all of a customer’s deployed Palo Alto Networks firewalls?
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this.
Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
An engineer is configuring a Protection profile to defend specific endpoints and resources against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
Panorama is being used to upgrade the PAN-OS version on a pair of firewalls in an active/passive high availability (HA) configuration. The Palo Alto Networks best practice upgrade steps have been completed in Panorama (Panorama upgraded, backups made, content updates, and disabling "Preemptive" pushed), and the firewalls are ready for upgrade. What is the next best step to minimize downtime and ensure a smooth transition?
Which action does a firewall take when a decryption profile allows unsupported modes and unsupported traffic with TLS 1.2 protocol traverses the firewall?
An administrator has configured OSPF with Advanced Routing enabled on a Palo Alto Networks firewall running PAN-OS 10.2. After OSPF was configured, the administrator noticed that OSPF routes were not being learned.
Which two actions could an administrator take to troubleshoot this issue? (Choose two.)
A remote administrator needs access to the firewall on an untrust interface. Which three options would you configure on an interface Management profile to secure management access? (Choose three)
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
Which server platforms can be monitored when a company is deploying User-ID through server monitoring in an environment with diverse directory services?