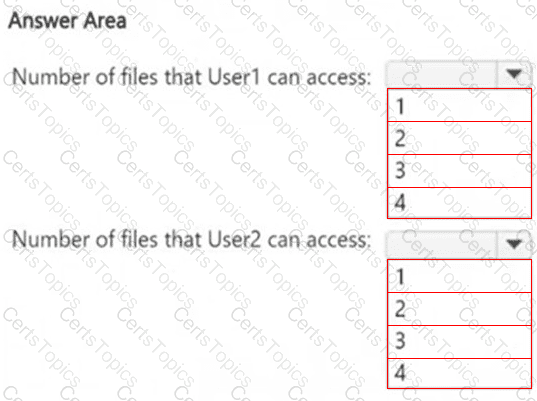
HOTSPOT
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
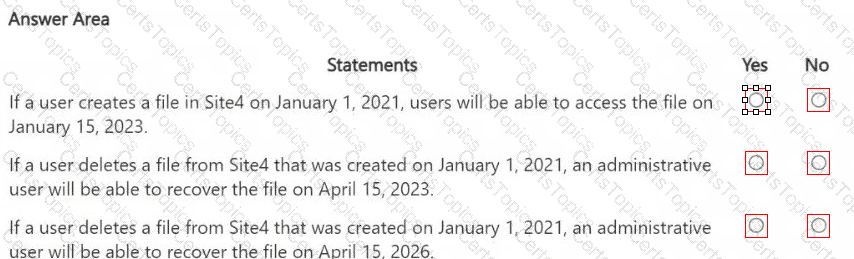
HOTSPOT
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
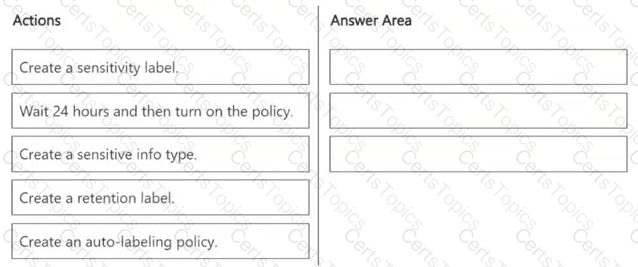
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
HOTSPOT
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the retention requirement for the users' Microsoft 365 data.
What is the minimum number of retention policies required to achieve the goal?
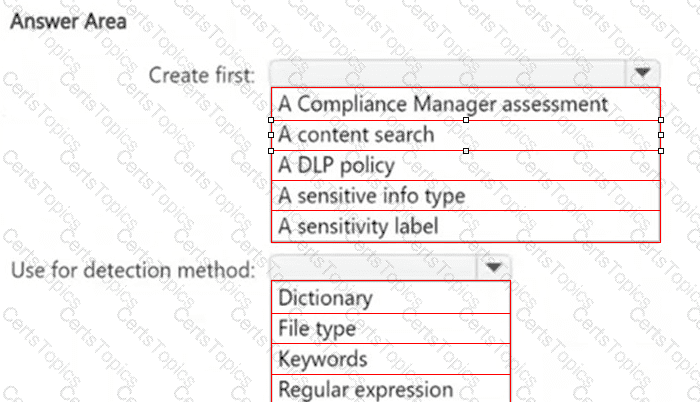
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?
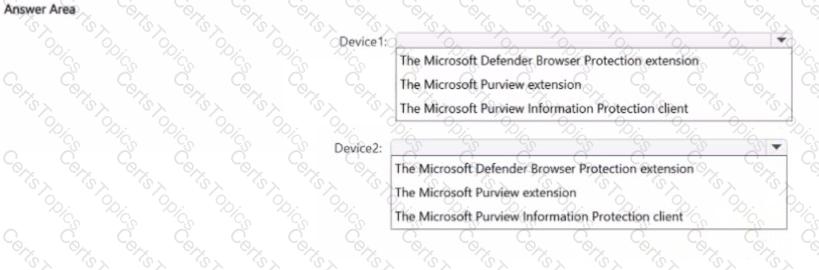
You have a Microsoft 36S ES subscription that contains two Windows devices named Devicel1and Device2 Device1 has the default browser set to Microsoft Edge. Devke2 has the default browser set to Google Chrome.
You need to ensure that Microsoft Purview insider risk management can collect signals when a user copies files to a USB device by using their default browser.
What should you deploy to each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 tenant.
You create a data loss prevention (DLP) policy.
You need to ensure that the policy protects documents in Microsoft Teams chat sessions.
Which location should you enable in the policy?
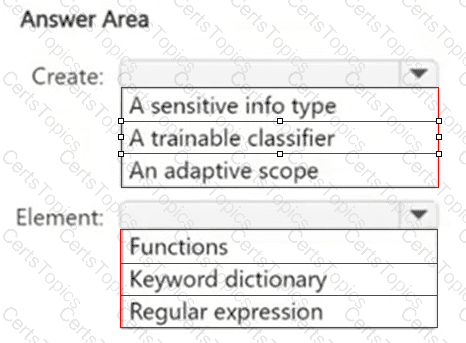
You have a Microsoft 365 E5 subscription.
You have a file named Customer.csv that contains a list of 1,000 customer names.
You plan to use Customer.csv to classify documents stored in a Microsoft SharePoint Online library.
What should you create in the Microsoft Purview portal, and which type of element should you select? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 tenant.
You have sensitivity labels as shown in the Sensitivity Labels exhibit. (Click the Sensitivity Labels tab.)

The Confidential/External sensitivity label is configured to encrypt files and emails when applied to content.
The sensitivity labels ate published as shown in the Published exhibit. (Click the Published tab.)
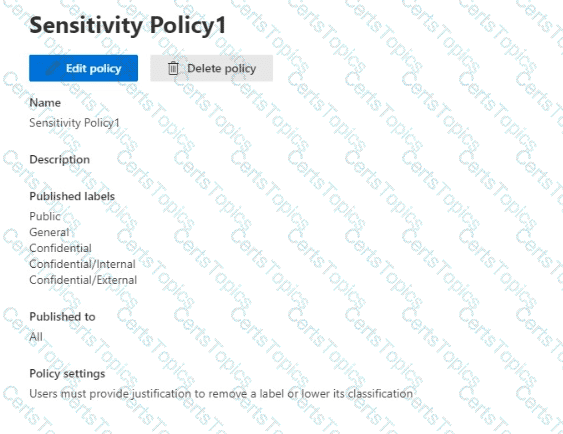
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management and contains three users named User1, User2, and User3.
All insider risk management policies have adaptive protection enabled and the default conditions for insider risk levels configured.
The users perform the following activities, which trigger insider risk policy alerts:
User1 performs at least one data exfiltration activity that results in a high severity risk score.
User2 performs at least three risky user activities within seven days, that each results in a high severity risk score.
User3 performs at least bwo data exfiltration activities within seven days, that each results in a high severity risk score.
Which insider risk level is assigned to each user? To answer, drag the appropriate levels to the correct users. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or seroll to view content.
NOTE: Each correct selection is worth one point.

You have a Microsoft 36S ES subscription.
From the Microsoft Purview Data Security Posture Management for Al portal, you review the recommendations for Al data security
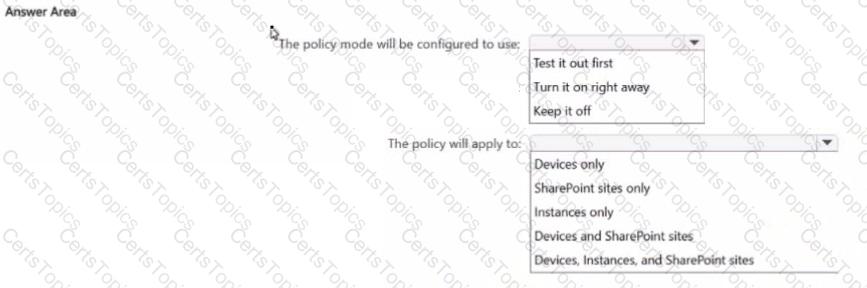
You plan to create a one-click policy to block elevated risk users from pasting or uploading sensitive data to Al websites
How will the policy be configured? To answer, select the appropriate options in the answer area
NOTE: Each correct selection is worth one point.
You have 4 Microsoft 565 E5 subscription that contains two Microsoft SharePoint Online sites named Site1 and Site2. You plan to configure a retention label named Labe1 and apply label1 to all the files in Site1 You need to ensure that two years after a file is created in Site1. the file moves automatically to Site2. How should you configure the Choose what happens after the retention period setting for Label1?
HOTSPOT
You have a Microsoft 365 E5 subscription.
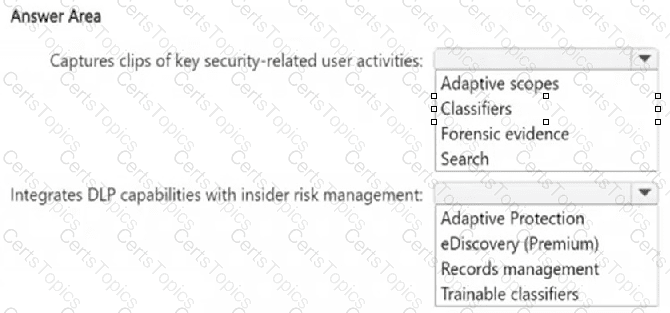
You need to implement a compliance solution that meets the following requirements:
● Captures clips of key security-related user activities, such as the exfiltration of sensitive company data.
● Integrates data loss prevention (DLP) capabilities with insider risk management.
What should you use for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 £5 subscription.
You are implementing insider risk management.
You need to create an insider risk management notice template and format the message body of the notice template.
How should you configure the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You plan to implement insider risk management for users that manage sensitive data associated with a project.
You need to create a protection policy for the users. The solution must meet the following requirements:
● Minimize the impact on users who are NOT part of the project.
● Minimize administrative effort.
What should you do first?
You have a Microsoft SharePoint Online site named Site1 that contains a document library. The library contains more than 1,000 documents. Some of the documents are job applicant resumes. All the documents are in the English language.
You plan to apply a sensitivity label automatically to any document identified as a resume. Only documents that contain work experience, education, and accomplishments must be labeled automatically.
You need to identify and categorize the resumes. The solution must minimize administrative effort.
What should you include in the solution?
You have a Microsoft 36515 subscription tha1 contains a Microsoft SharePoint Online site named Site1 Site1 contains three tiles named File1. File2 and File3.
You create the data loss prevention (DIP) policies shown in the following table.
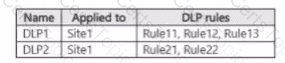
The DIP rule matches for each tile are shown in the following table.
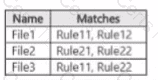
How many DIP policy matches events will be added to Activity explorer, and how many policy matches will be added to the DLP incidents report? To answer, select the appropriate options m the answer area.

You have a Microsoft 365 subscription.
You create a retention label named Label1 as shown in the following exhibit.
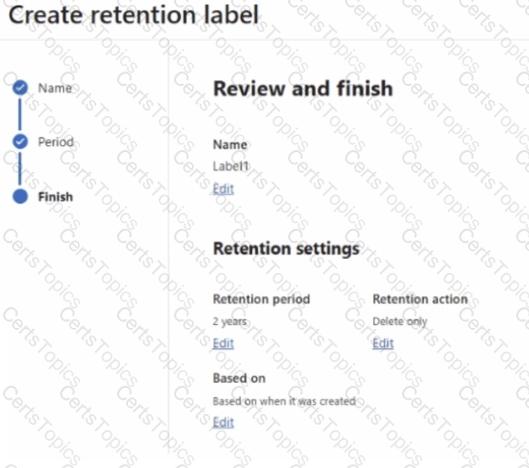
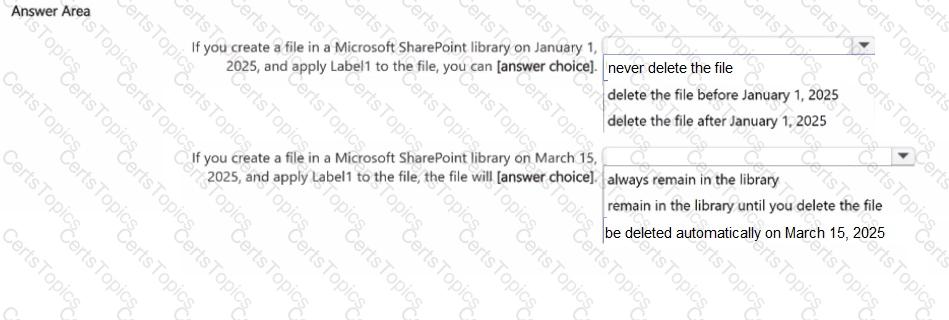
You publish Label! to SharePoint sites.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a trainable classifier named Trainable1.
You plan to create the items shown in the following table.
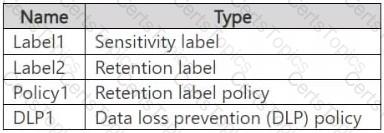
Which items can use Trainable 1?
You have a Microsoft 365 subscription.
You need to ensure that users can apply retention labels to individual documents in their Microsoft SharePoint libraries.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You plan to deploy Microsoft Purview Data Security Posture Management for Al (DSPM for Al) to protect company data that contains Personally Identifiable Information (Pll) from being shared with third-party generative Al tools.
You need to complete the prerequisites for the planned deployment.
Which two Microsoft Purview solutions should you use? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You create a sensitivity label named Label1 and publish Label1 to all users and groups.
You have the following files in a SharePoint site:
• File1.doc
• File2.docx
• File3.xlsx
• File4.txt
You need to identify which files can have Label1 applied.
Which files should you identify?
Your company has a Microsoft 365 tenant.
The company performs annual employee assessments. The assessment results are recorded in a document named AssessmentTemplate.docx that is created by using a Microsoft Word template. Copies of the employee assessments are sent to employees and their managers.
The assessment copies are stored in mailboxes, Microsoft SharePoint Online sites, and OneDrive folders. A copy of each assessment is also stored in a SharePoint Online folder named Assessments.
You need to create a data loss prevention (DLP) policy that prevents the employee assessments from being emailed to external users. You will use a document fingerprint to identify the assessment documents. The solution must minimize effort.
What should you include in the solution?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add a folder path to the file path exclusions.
Does this meet the goal?
You have a Microsoft 36S subscription.
In Microsoft Exchange Online, you configure the mail flow rule shown in the following exhibit.
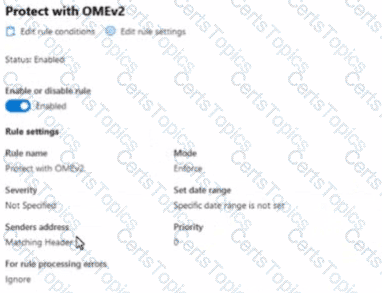
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains a device named Device1.
You need to enable Endpoint data loss prevention (Endpoint DLP) for Device1.
What should you do first in the Microsoft Purview portal?
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
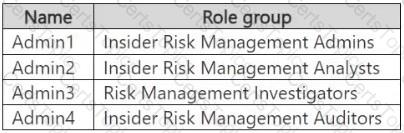
You plan to create a Microsoft Purview insider risk management case named Case1.
Which insider risk management object should you select first, and which users will be added as contributors for Case1 by default?
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
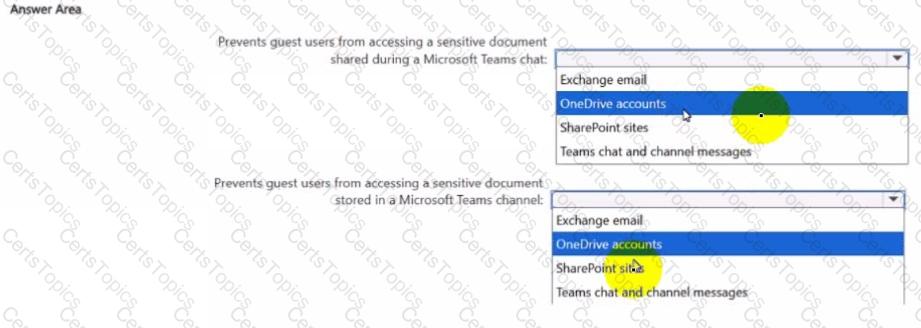
You create a data loss prevention (DIP) policy that meets the following requirements:
• Prevents guest users from accessing a sensitive document shared during a Microsoft Teams chat
• Prevents guest users from accessing a sensitive document stored in a Microsoft Team? channel
Which location should you select for each requirement? To answer, select the appropriate options in the answer area NOTE: Each correct selection is worth one point.
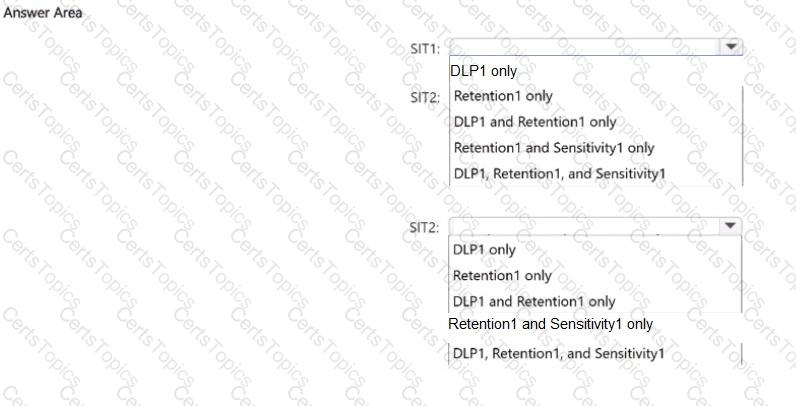
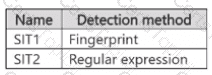
You have a Microsoft 365 E5 subscription that contains the sensitive information types (SITs) shown in the following table.
You plan to create the policies shown in the following table and assign them to a Microsoft SharePoint Online site.
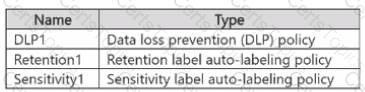
Which policies can use SIT1. and which policies can use SIT2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.