You have a Microsoft 365 E5 subscription.
You have a file named Customer.csv that contains a list of 1,000 customer names.
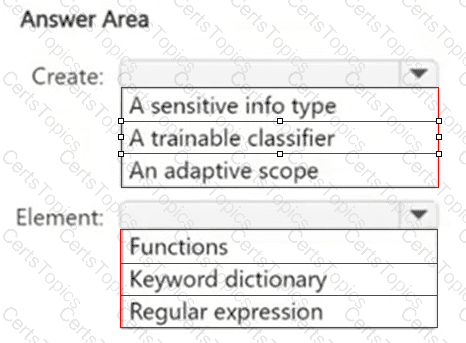
You plan to use Customer.csv to classify documents stored in a Microsoft SharePoint Online library.
What should you create in the Microsoft Purview portal, and which type of element should you select? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 tenant.
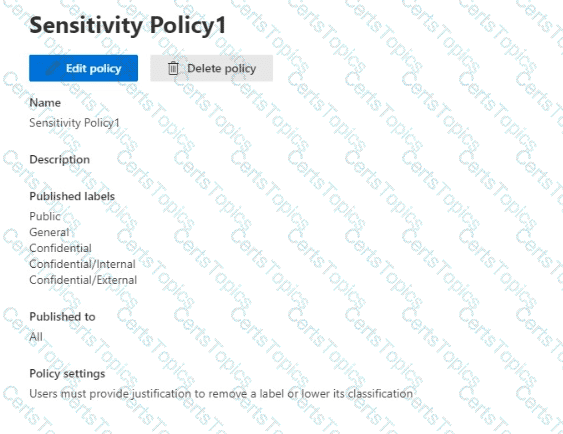
You have sensitivity labels as shown in the Sensitivity Labels exhibit. (Click the Sensitivity Labels tab.)

The Confidential/External sensitivity label is configured to encrypt files and emails when applied to content.
The sensitivity labels ate published as shown in the Published exhibit. (Click the Published tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management and contains three users named User1, User2, and User3.
All insider risk management policies have adaptive protection enabled and the default conditions for insider risk levels configured.
The users perform the following activities, which trigger insider risk policy alerts:
User1 performs at least one data exfiltration activity that results in a high severity risk score.
User2 performs at least three risky user activities within seven days, that each results in a high severity risk score.
User3 performs at least bwo data exfiltration activities within seven days, that each results in a high severity risk score.
Which insider risk level is assigned to each user? To answer, drag the appropriate levels to the correct users. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or seroll to view content.
NOTE: Each correct selection is worth one point.

You have a Microsoft 36S ES subscription.
From the Microsoft Purview Data Security Posture Management for Al portal, you review the recommendations for Al data security
You plan to create a one-click policy to block elevated risk users from pasting or uploading sensitive data to Al websites
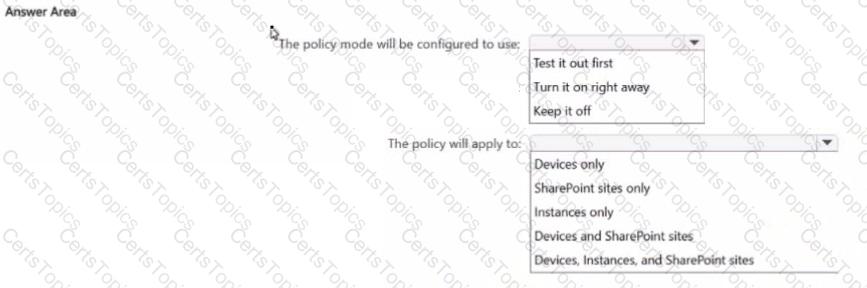
How will the policy be configured? To answer, select the appropriate options in the answer area
NOTE: Each correct selection is worth one point.