Refer to the exhibits, which show the configuration of an SD-WAN rule and the corresponding rule status and routing table.
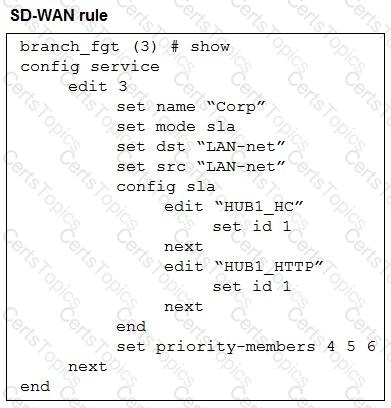

The administrator wants to understand the expected behavior for traffic matching the SD-WAN rule.
Based on the exhibits, what can the administrator expect for traffic matching the SD-WAN rule?
Refer to the exhibits.
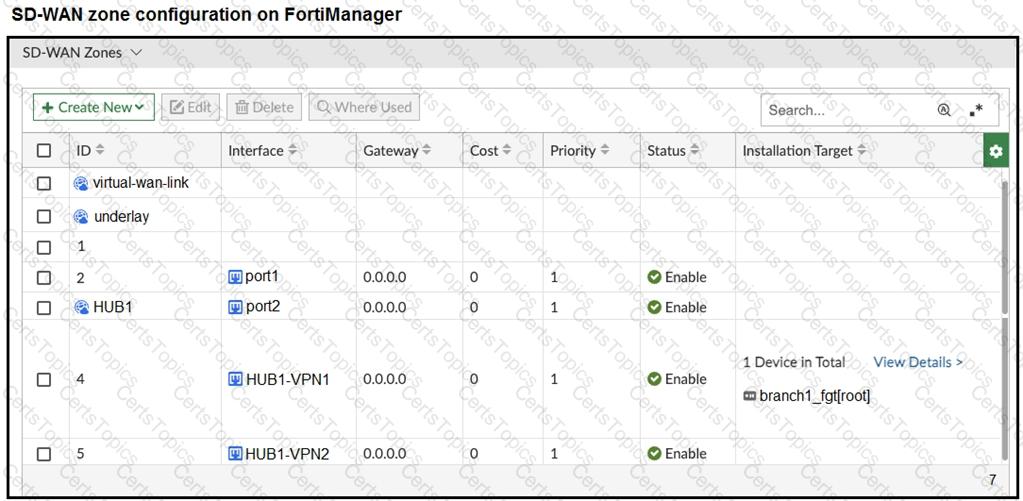
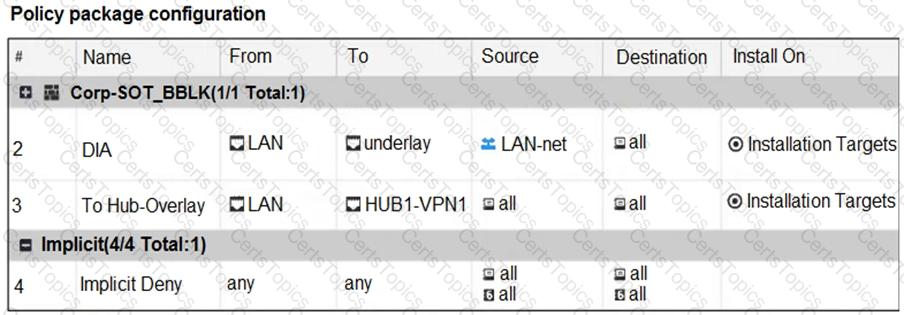
The exhibits show the SD-WAN zone configuration of an SD-WAN template prepared on FortiManager and the policy package configuration.
When the administrator tries to install the configuration changes, FortiManager fails to commit.
What should the administrator do to fix the issue?
(Refer to the exhibits.
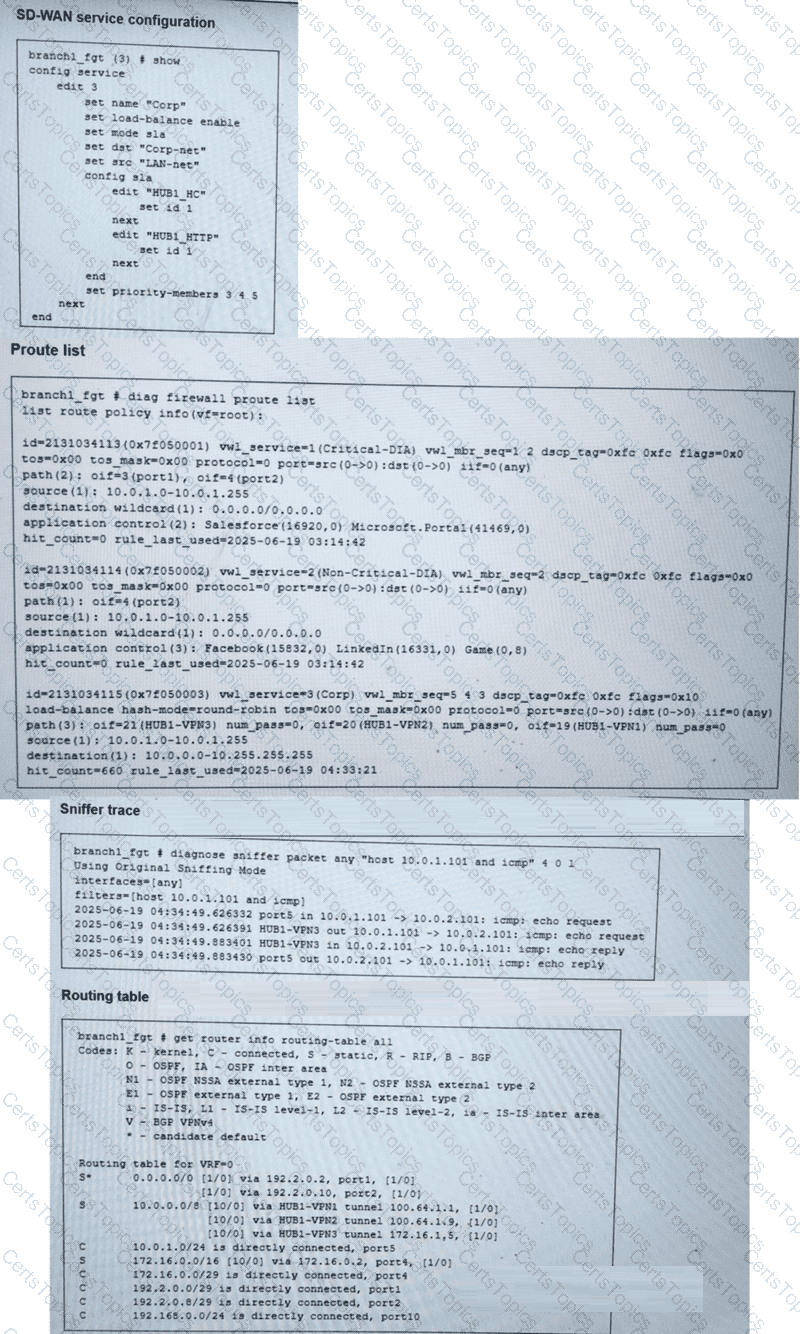
You collected the output shown in the exhibits and want to know which interface HTTP traffic will flow through from the user device 10.0.1.101 to the corporate web server 10.0.0.126. All SD-WAN links are stable.
Which interface will FortiGate use to steer the traffic? Choose one answer.)
The administrator uses the FortiManager SD-WAN overlay template to prepare an SD-WAN deployment. Using information provided through the SD-WAN overlay template wizard, FortiManager creates templates ready to install on the spoke and hub devices.
What are the three templates created by the SD-WAN overlay template for a spoke device? (Choose three.)
(You want FortiGate to use SD-WAN rules to steer ping local-out traffic.
Which two constraints should you consider? Choose two answers.)
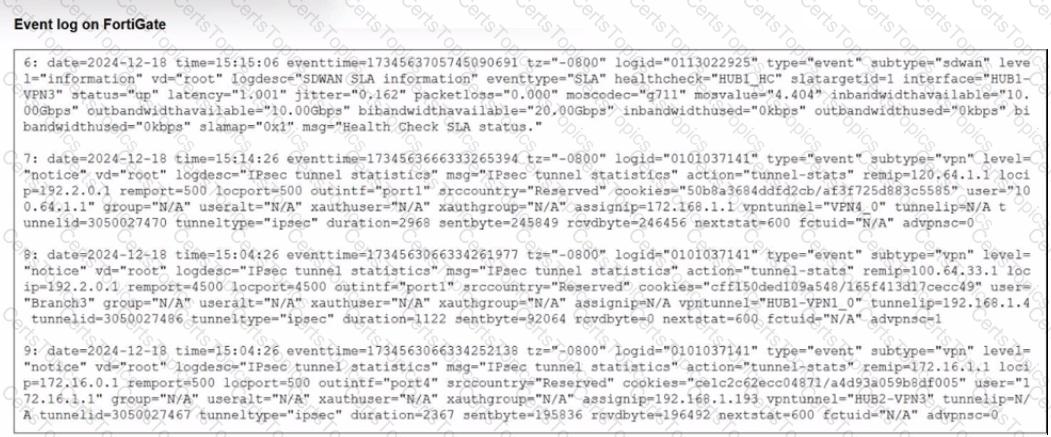
Refer to the exhibit that shows event logs on FortiGate.
Based on the output shown in the exhibit, what can you say about the tunnels on this device?
Refer to the exhibits.
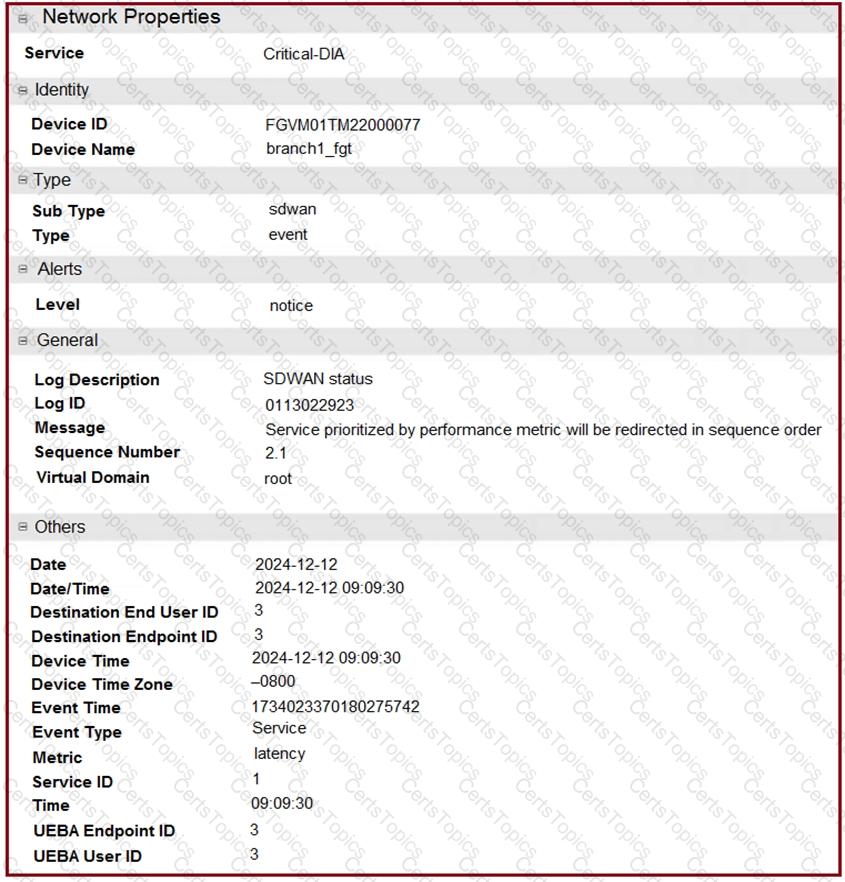

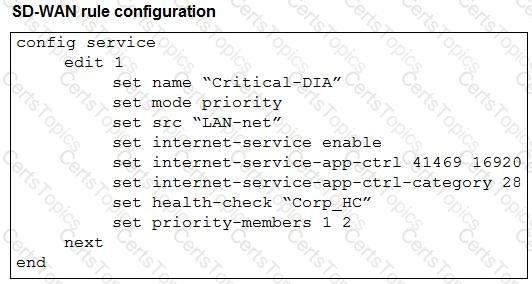
The exhibits show an SD-WAN event log, the member status, and the SD-WAN rule configuration.
Which two conclusions can you draw from the information shown? (Choose two.)
(Refer to the exhibit.
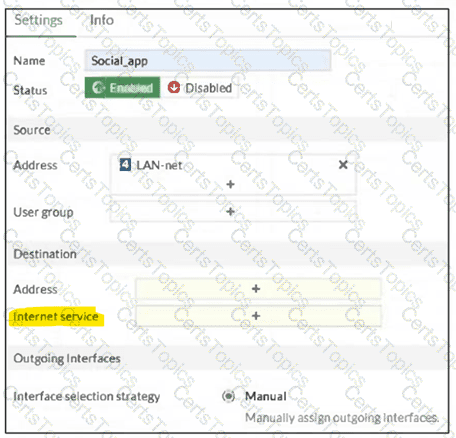
You configure SD-WAN on a standalone FortiGate device.
You want to create an SD-WAN rule that steers traffic related to Facebook and LinkedIn through the less costly internet link.
What must you do to set Facebook and LinkedIn applications as destinations from the GUI? Choose one answer.)
(In which order does FortiGate consider the following elements during the route lookup process? Choose one answer.)
(Refer to the exhibit.
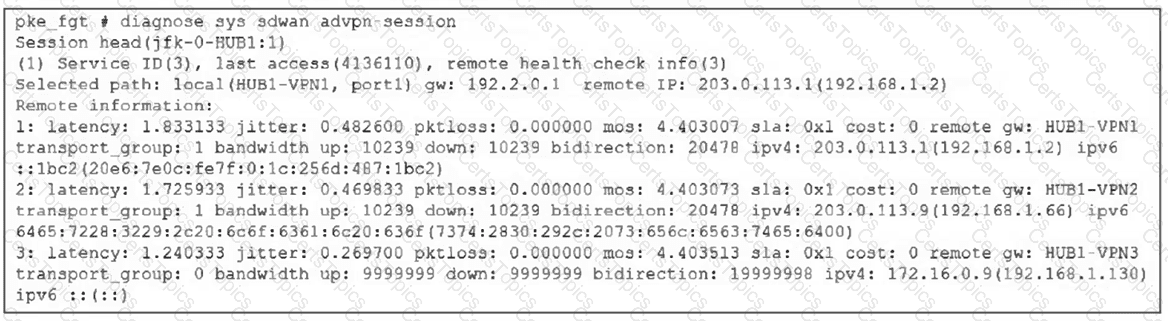
Based on the output shown in the exhibit, what can you conclude about the device role and how it handles health checks? Choose one answer.)
Refer to the exhibits.
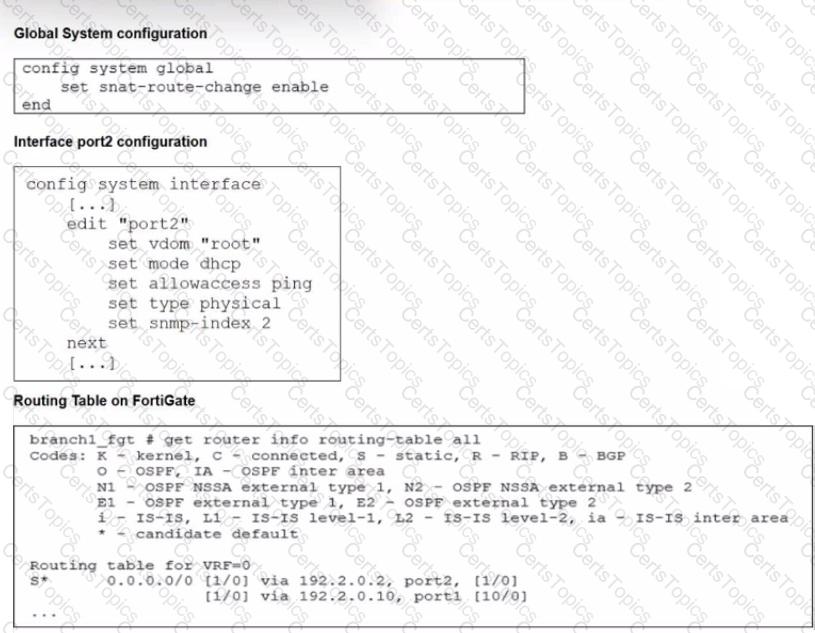
The exhibits show the source NAT (SNAT) global setting. port2 interface settings, and the routing table on FortiGate.
The administrator increases the member priority on port2 to 20.
Upon configuration changes and the receipt of new packets, which two actions does FortiGate perform on existing sessions established over port2? (Choose two.)
Refer to the exhibit.
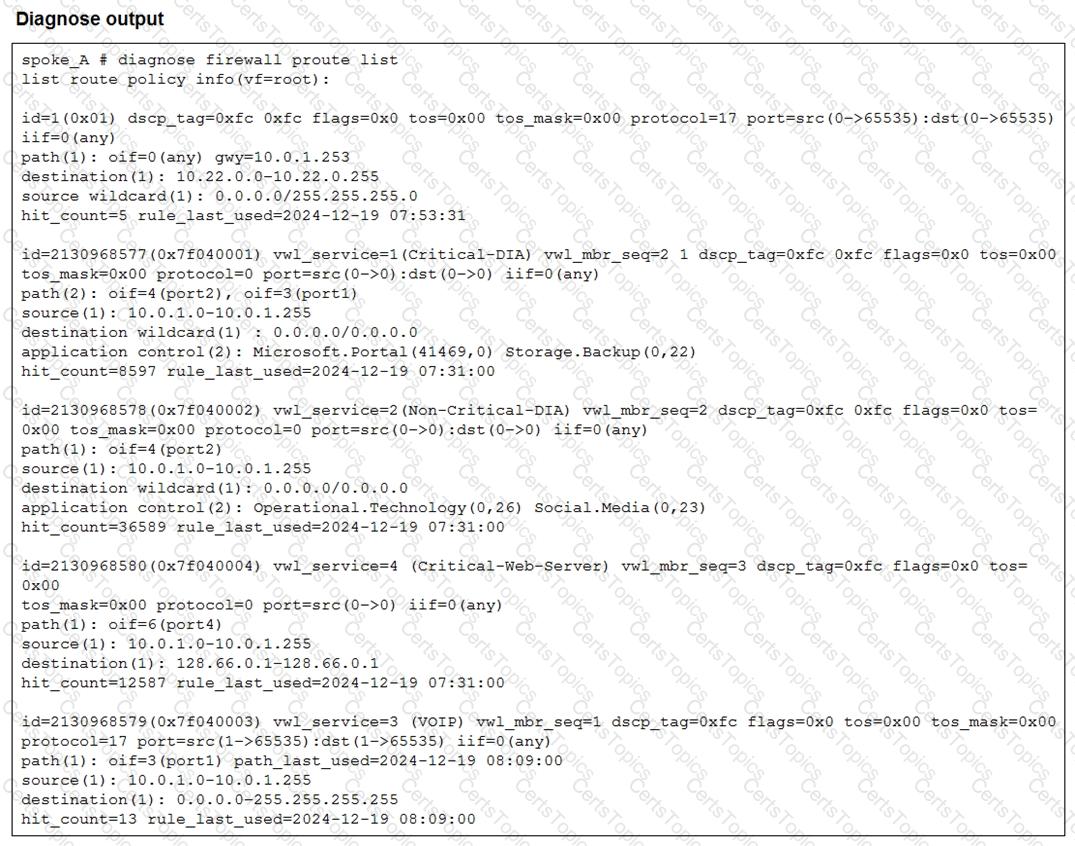
Which two conclusions can you draw from the output shown? (Choose two.)
Refer to the exhibits.
You use FortiManager to configure SD-WAN on three branch devices.
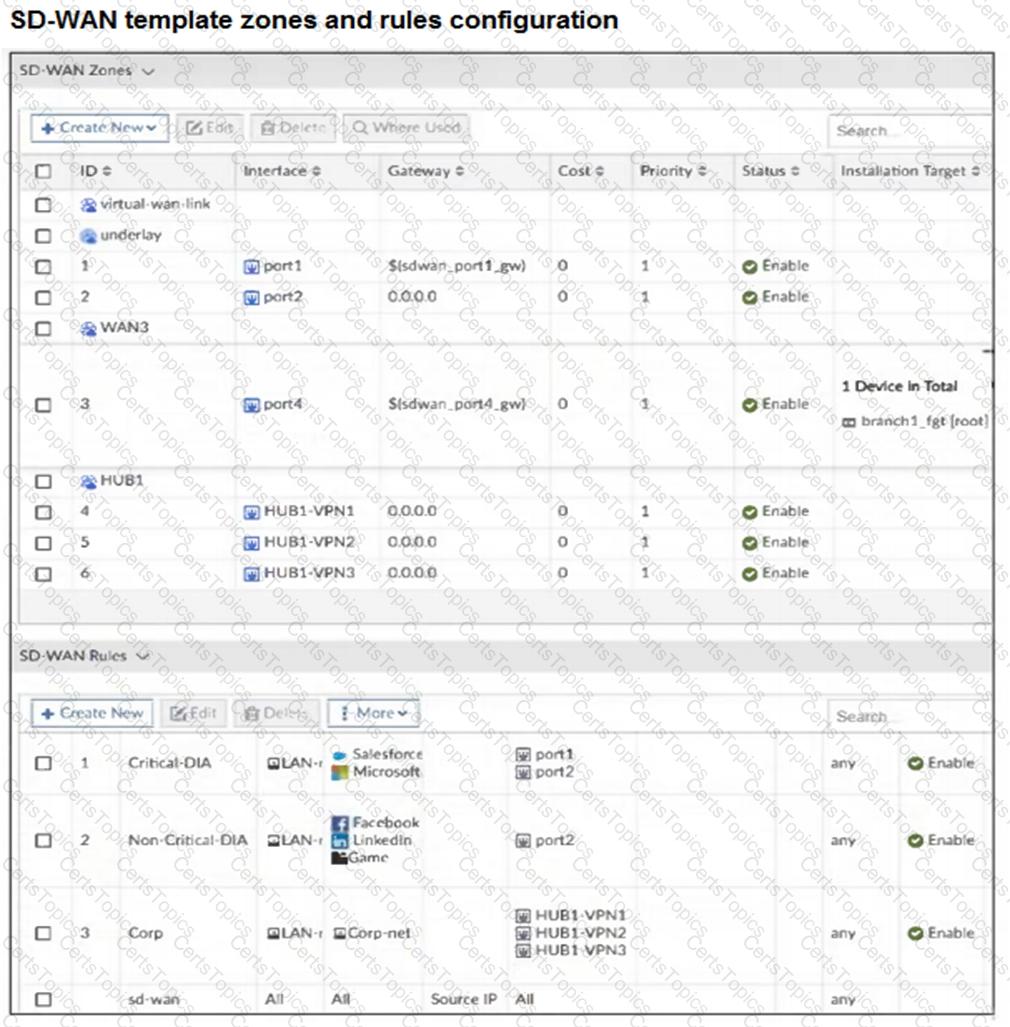

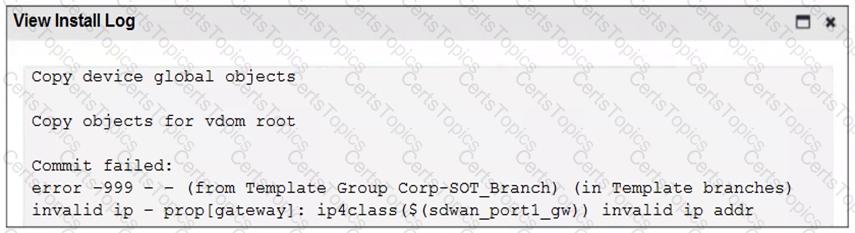
When you install the device settings, FortiManager prompts you with the error “Copy Failed” for the device branch1_fgt. When you click the log button, FortiManager displays the message shown in the exhibit.
There are two different ways to resolve this issue. Based on the exhibits, which methods could you use? (Choose two.)
The FortiGate devices are managed by ForliManager, and are configured for direct internet access (DIA). You confirm that DIA is working as expected for each branch, and check the SD-WAN zone configuration and firewall policies shown in the exhibits.
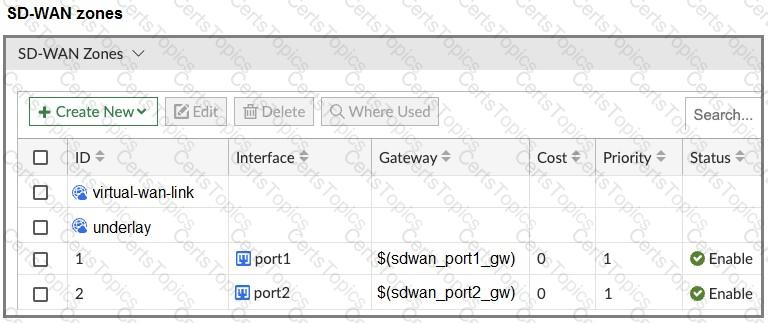
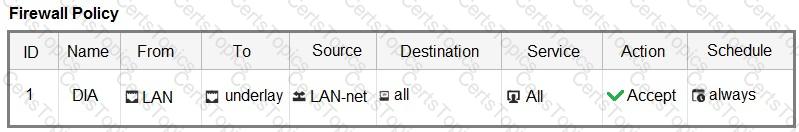

Then, you use the SD-WAN overlay template to configure the IPsec overlay tunnels. You create the associated SD-WAN rules to connect existing branches to the company hub device and apply the changes on the branches.
After those changes, users complain that they lost internet access. DIA is no longer working.
Based on the exhibit, which statement best describes the possible root cause of this issue?
You configured an SD-WAN rule with the best quality strategy and selected the predefined health check, Default_FortiGuard, to check the link performances against FortiGuard servers.
For the quality criteria, you selected Custom-profile-1.
Which factors does FortiGate use, and in which order. to determine the link that it should use to steer the traffic?
(Refer to the exhibits.

Two SD-WAN event logs, the member status, the SD-WAN rule configuration, and the health-check configuration for a FortiGate device are shown.
Immediately after the log messages are displayed, how will the FortiGate steer the traffic based on the information shown in the exhibits? Choose one answer.)
Refer to the exhibit.

An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network.
The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over HUB1-VPN1. However, the traffic is routed over HUB1-VPN3.
Based on the output shown in the exhibit, which two reasons, individually or together, could explain the observed behavior? (Choose two.)
Refer to the exhibit.
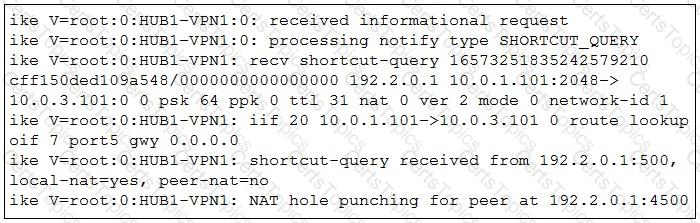
Which statement best describe the role of the ADVPN device in handling traffic?
(Refer to the exhibit.

An SD-WAN zone configuration on the FortiGate GUI is shown.
What can you conclude about the zone and member configuration on this device? Choose one answer.)
(You want to configure two static routes: one that references an SD-WAN zone and a second one that references an SD-WAN member that belongs to that zone.
Which statement about this scenario is true? Choose one answer.)
(In the context of SD-WAN, the terms underlay and overlay are commonly used to categorize links.
Which two statements about underlay and overlay links are correct? Choose two answers.)
(Refer to the exhibit.
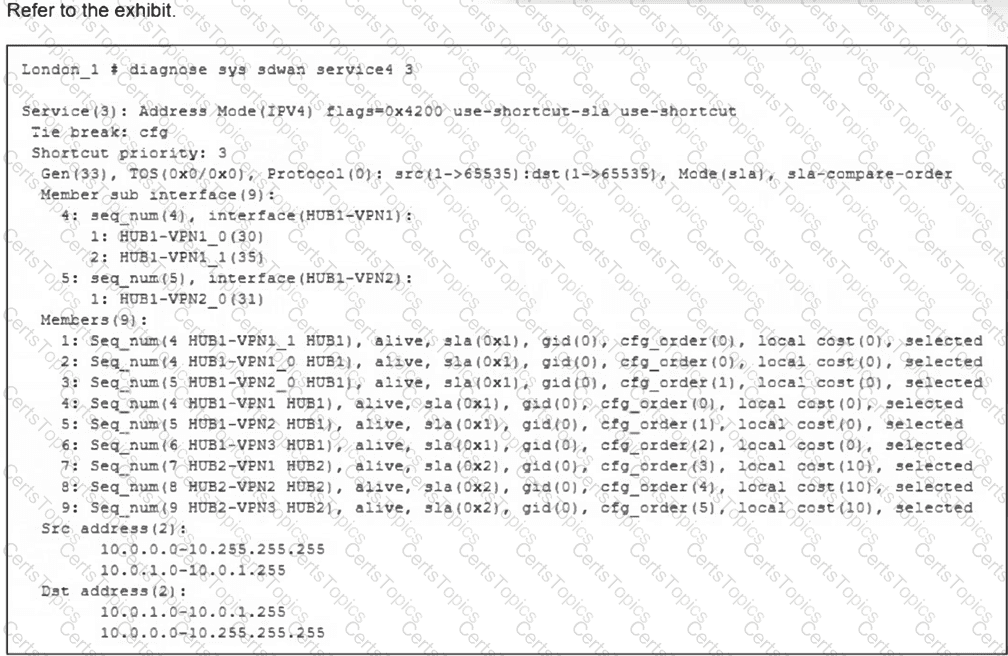
What can you conclude from the output shown? Choose one answer.)
Refer to the exhibits.
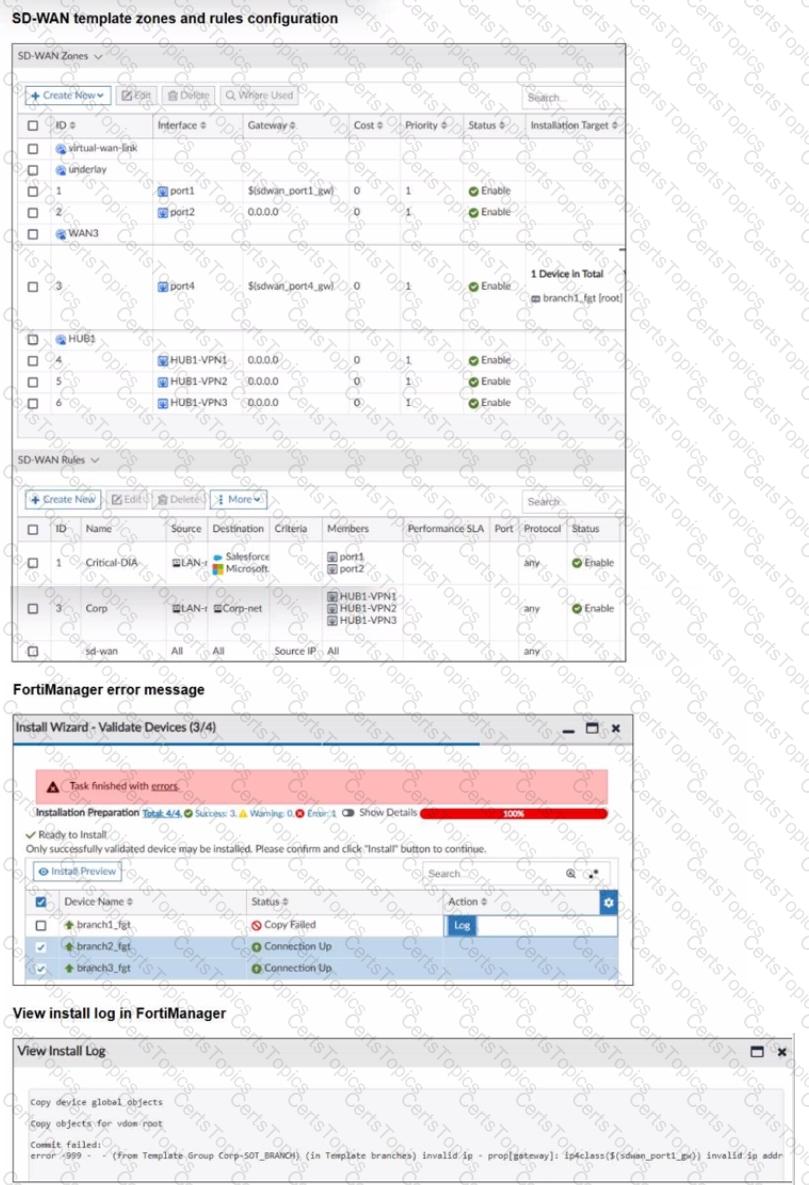
You use FortiManager to configure SD-WAN on three branch devices.
When you install the device settings. FortiManager prompts you with the error "Copy Failed" for the device branch1_fat When you click the log button. FortiManager displays the message shown in the exhibit.
(Refer to the exhibit.
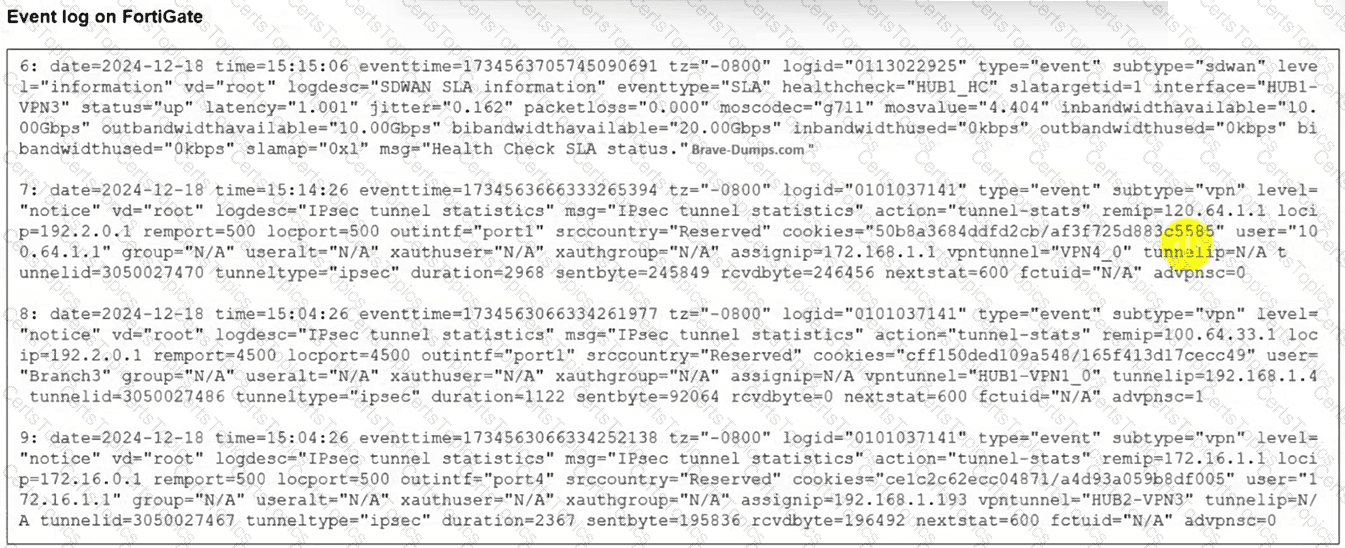
The event log on a FortiGate device is shown.
Based on the output shown in the exhibit, what can you conclude about the tunnels on this device? (Choose one answer))
Which three factors about SLA targets and SD-WAN rules should you consider when configuring SD-WAN rules? (Choose three.)
Your FortiGate is in production. To optimize WAN link use and improve redundancy, you enable and configure SD-WAN.
What must you do as part of this configuration update process?
Exhibit.
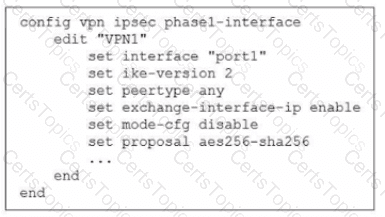
The administrator configured the IPsec tunnel VPN1 on a FortiGate device with the parameters shown in exhibit.
Based on the configuration, which three conclusions can you draw about the characteristics and requirements of the VPN tunnel? (Choose three.)
Refer to the exhibit.

An administrator checks the status of an SD-WAN topology using the FortiManager SD-WAN monitor menus. All members are configured with one or two SLAs.
Which two conclusions can you draw from the output shown? (Choose two.)