A business analyst is examining a report and notices compute costs are very high for four cloud-based, load- balanced virtual machines hosting an application. The application will be in use for at least two more years, but there are no developers available to help optimize it. Which of the following should the analyst recommend to BEST reduce costs without impacting performance?
Decommission a virtual machine.
Change to a pay-as-you-go plan.
Convert the application to a SaaS solution.
Switch the virtual machines to reserved instances.
Reserved instances are a discount billing concept in which businesses can obtain significant discounts compared to standard on-demand cloud computing prices in return for committing to a specified level of usage1. Reserved instances are not physical instances, but rather a billing discount applied to the use of on-demand instances in the account2. Reserved instances can save up to 75% over equivalent on-demand capacity3. By switching the virtual machines to reserved instances, the analyst can best reduce costs without impacting performance, as long as the application’s usage pattern is predictable and consistent. Decommissioning a virtual machine might affect the performance and availability of the application. Changing to a pay-as-you-go plan might not reduce costs if the application’s usage is high and stable. Converting the application to a SaaS solution might require additional development and migration efforts, which are not feasible in this scenario. References:
A cloud administrator needs to enable users to access business applications remotely while ensuring these applications are only installed on company-controlled equipment. All users require the ability to modify personal working environments. Which of the following is the BEST solution?
SSO
VDI
SSH
VPN
The best solution for this scenario is Virtual Desktop Infrastructure (VDI). VDI is a cloud service model that provides users with virtual desktops that run on a centralized server. Users can access their virtual desktops remotely from any device, such as a laptop, tablet, or smartphone, using a thin client or a web browser. VDI enables users to access business applications without installing them on their own devices, which ensures that these applications are only installed on company-controlled equipment. VDI also allows users to modify their personal working environments, such as desktop settings, wallpapers, or preferences, which are saved on the server and persist across sessions. VDI can offer benefits such as improved security, reduced hardware costs, centralized management, and enhanced user experience. The other options are not the best solutions for this scenario. Single Sign-On (SSO) is a cloud service that enables users to log in to multiple applications or systems with one set of credentials, which simplifies authentication and improves security. However, SSO does not provide users with remote access to business applications or personal working environments. Secure Shell (SSH) is a network protocol that allows secure remote access to a server or a device using encryption and authentication. SSH can be used to execute commands, transfer files, or tunnel network traffic. However, SSH does not provide users with virtual desktops or business applications. Virtual Private Network (VPN) is a network technology that creates a secure connection between a remote device and a private network over a public network, such as the Internet. VPN can be used to access network resources, such as files, printers, or applications, that are not available otherwise. However, VPN does not provide users with virtual desktops or personal working environments. References: CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002), Chapter 2: Cloud Concepts, Section 2.3: Cloud Service Models, p. 64-65
Which of the following policies dictates when to grant certain read/write permissions?
Access control
Communications
Department-specific
Security
Access control is a policy that dictates when to grant certain read/write permissions to users or systems. Access control is a key component of information security, as it ensures that only authorized and authenticated users can access the data and resources they need, and prevents unauthorized access or modification of data and resources1. Access control policies can be based on various factors, such as identity, role, location, time, or context2.
Communications, department-specific, and security policies are not directly related to granting read/write permissions, although they may have some implications for access control. Communications policies are policies that define how information is exchanged and communicated within or outside an organization, such as the use of email, social media, or encryption3. Department-specific policies are policies that apply to specific functions or units within an organization, such as human resources, finance, or marketing. Security policies are policies that establish the overall goals and objectives of information security in an organization, such as the protection of confidentiality, integrity, and availability of data and systems. References: Access Control Policy and Implementation Guides | CSRC; What Is Access Control? | Microsoft Security; Communication Policy - Definition, Examples, Cases, Processes; [Departmental Policies and Procedures Manual Template | Policies and Procedures Manual Template]; [Security Policy - an overview | ScienceDirect Topics].
Which of the following is the BEST way to secure a web session to a hosted e-commerce website?
SSL
VPN
Firewall
DNS
SSL (Secure Sockets Layer) is the best way to secure a web session to a hosted e-commerce website. SSL is a protocol that encrypts the data exchanged between a web browser and a web server, ensuring that no one can intercept, modify, or steal the information. SSL also provides authentication, which verifies the identity of the web server and the web browser, preventing impersonation or spoofing attacks. SSL is essential for e-commerce websites, as they handle sensitive data, such as credit card numbers, personal information, and login credentials, that need to be protected from hackers and cybercriminals. SSL also helps to build trust and confidence among customers, as they can see that the website is secure and legitimate. SSL can be recognized by the presence of a padlock icon and the HTTPS prefix in the web address. To enable SSL, e-commerce websites need to obtain and install an SSL certificate from a trusted certificate authority (CA), which is a third-party organization that issues and validates SSL certificates. SSL certificates can vary in price, validity, and level of security, depending on the type and provider of the certificate. Some web hosts and e-commerce platforms may offer free or discounted SSL certificates as part of their services. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Cloud Security, Section 4.2: Cloud Security Concepts, Page 154. How to Secure Your E-Commerce Website: 6 Basic Steps1 eCommerce Security: A Complete Guide to Protect Your Store2
For security reasons, a cloud service that can be accessed from anywhere would make BEST use of:
replication.
multifactor authentication.
single sign-on.
data locality
Multifactor authentication is a security method that requires users to provide more than one piece of evidence to verify their identity before accessing a cloud service. For example, users may need to enter a password, a code sent to their phone or email, a biometric scan, or a physical token. Multifactor authentication can enhance the security of a cloud service that can be accessed from anywhere, as it can prevent unauthorized access even if the password is compromised or stolen. Multifactor authentication can also protect the cloud service from phishing, brute force, or replay attacks, as well as comply with regulatory or industry standards.
Multifactor authentication is different from other options, such as replication, single sign-on, or data locality. Replication is the process of copying data or resources across multiple locations, such as regions, zones, or data centers, to improve availability, performance, or backup. Single sign-on is a user authentication method that allows users to access multiple cloud services with one set of credentials, such as username and password. Data locality is the principle of storing data close to where it is used, such as in the same region, country, or jurisdiction, to improve performance, security, or compliance. While these options may also have some benefits for a cloud service that can be accessed from anywhere, they do not directly address the security concern, which is the focus of the question. References: What is MFA? - Multi-Factor Authentication and 2FA Explained - AWS, Multi-Factor Authentication (MFA) for IAM - aws.amazon.com, Multi-Factor Authentication & Single Sign-On | Duo Security
Which of the following cloud migration methods would take full advantage of the cloud computing model?
Rip and replace
Lift and shift
Phased
Hybrid
Rip and replace is a cloud migration method that involves discarding the existing legacy system and building a new one from scratch on the cloud platform. This method allows the organization to take full advantage of the cloud computing model, such as scalability, elasticity, performance, and cost-efficiency. Rip and replace also enables the organization to leverage the cloud-native features and services, such as serverless computing, microservices, and containers. However, rip and replace is also the most complex and risky migration method, as it requires a complete redesign and redevelopment of the system, which can be time-consuming, expensive, and prone to errors. Therefore, rip and replace is only suitable for systems that are outdated, incompatible, or unsuitable for the cloud environment, and that have a clear business case and return on investment for the migration. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 5: Cloud Migration, page 1971
Which of the following BEST describes the open-source licensing model for application software?
Software is free to use, but the source code is not available to modify.
Modifications to existing software are not allowed.
Code modifications must be submitted for approval.
Source code is readily available to view and use.
The open-source licensing model for application software is a type of software license that allows anyone to access, modify, and distribute the source code of the software, subject to certain terms and conditions. The source code is the human-readable version of the software that contains the instructions and logic for how the software works. By making the source code available, open-source software licenses enable collaboration, innovation, and transparency among software developers and users. There are different types of open-source software licenses, such as permissive and copyleft licenses, that vary in the degree of freedom and restriction they impose on the use and modification of the software. However, the common characteristic of all open-source software licenses is that they grant the right to view and use the source code of the software. Therefore, option D is the best description of the open-source licensing model for application software. Option A is incorrect because it describes the opposite of the open-source licensing model. Software that is free to use, but the source code is not available to modify, is called closed-source or proprietary software. Option B is incorrect because it contradicts the open-source licensing model. Modifications to existing software are allowed under open-source software licenses, as long as they comply with the terms and conditions of the license. Option C is incorrect because it does not reflect the open-source licensing model. Code modifications do not need to be submitted for approval under open-source software licenses, although they may need to be shared with the original author or the community, depending on the license. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 2: Cloud Concepts, Section 2.4: Cloud Service Models, Page 531 and Understanding Open-Source Software Licenses | DigitalOcean
A business analyst has been drafting a risk response for a vulnerability that was identified on a server. After considering the options, the analyst decides to decommission the server. Which of the following describes this approach?
Mitigation
Transference
Acceptance
Avoidance
Avoidance is a risk response strategy that involves eliminating the threat or uncertainty associated with a risk by removing the cause or the source of the risk. Avoidance can help to prevent the occurrence or the impact of a negative risk, but it may also result in the loss of potential opportunities or benefits. Avoidance is usually applied when the risk is too high or too costly to mitigate, transfer, or accept12
The business analyst is using the avoidance strategy by decommissioning the server that has a vulnerability. By doing so, the analyst is eliminating the possibility of the vulnerability being exploited or causing harm to the system or the data. However, the analyst is also losing the functionality or the value that the server provides, and may need to find an alternative solution or resource.
Mitigation is not the correct answer, because mitigation is a risk response strategy that involves reducing the probability or the impact of a negative risk by implementing actions or controls that can minimize or counteract the risk. Mitigation can help to lower the exposure or the severity of a risk, but it does not eliminate the risk completely. Mitigation is usually applied when the risk is moderate or manageable, and the cost of mitigation is justified by the potential benefit12
Transference is not the correct answer, because transference is a risk response strategy that involves shifting the responsibility or the impact of a negative risk to a third party, such as a vendor, a partner, or an insurer. Transference can help to share or distribute the risk, but it does not reduce or remove the risk. Transference is usually applied when the risk is beyond the control or the expertise of the organization, and the cost of transference is acceptable or affordable12
Acceptance is not the correct answer, because acceptance is a risk response strategy that involves acknowledging the existence or the possibility of a negative risk, and being prepared to deal with the consequences if the risk occurs. Acceptance can be passive, which means no action is taken to address the risk, or active, which means a contingency plan or a reserve is established to handle the risk. Acceptance is usually applied when the risk is low or inevitable, and the cost of avoidance, mitigation, or transference is higher than the cost of acceptance12
References: 1: 2: page 50
Monthly cloud service costs are BEST described as:
operating expenditures.
fixed expenditures.
capital expenditures.
personnel expenditures.
Monthly cloud service costs are best described as operating expenditures. Operating expenditures (OPEX) are the ongoing costs of running a business or a service, such as rent, utilities, salaries, maintenance, and subscriptions1. Cloud services are typically paid on a monthly or annual basis, depending on the usage and the service level agreement. Cloud services reduce the need for capital expenditures (CAPEX), which are the upfront costs of acquiring assets, such as hardware, software, or infrastructure1. Fixed expenditures are the costs that do not change regardless of the level of output or activity, such as rent or insurance2. Personnel expenditures are the costs of hiring, training, and retaining employees, such as salaries, benefits, or taxes3. References: CompTIA Cloud Essentials+ Certification | CompTIA IT Certifications, CompTIA Cloud Essentials CLO-002 Certification Study Guide, Fixed Costs Definition, Personnel Costs Definition
After performing an initial assessment of a cloud-hosted architecture, a department wants to gain the support of upper management.
Which of the following should be presented to management?
Project charter
Feasibility study
Managed services
Pilot
A project charter is a document that defines the scope, objectives, and stakeholders of a project. It also provides a high-level overview of the project’s benefits, risks, assumptions, constraints, and deliverables. A project charter is used to gain the support and approval of upper management and other key stakeholders before initiating a project. A project charter is one of the outputs of the cloud assessment process, which involves evaluating the feasibility, suitability, and readiness of an organization to adopt cloud services. References: CompTIA Cloud Essentials+ (CLO-002) Study Guide, Chapter 4: Cloud Assessment, Section 4.1: Cloud Assessment Process, page 9712; CompTIA Cloud Essentials+ Certification Exam Objectives, Objective 4.1: Given a scenario, analyze and report the outputs of a cloud assessment, page 143
Which of the following are examples of capital expenditures? (Select TWO).
Cloud consultant fees
Data center wiring
Data center electric bill
Server purchases
Spot instances
Disposable virtual machine
Capital expenditures are costs that a business incurs to acquire or improve long-term assets that will provide benefits beyond the current year. Capital expenditures are also known as PP&E, which stands for Property, Plant, and Equipment. Capital expenditures are usually one-time purchases of fixed assets that have a high initial cost and a long useful life. Capital expenditures are recorded as assets on the balance sheet and depreciated over time12
Data center wiring and server purchases are examples of capital expenditures, because they are part of the physical infrastructure that supports the IT operations of a business. Data center wiring and server purchases have a high upfront cost and a long lifespan, and they provide benefits for several years. Data center wiring and server purchases are also recorded as assets on the balance sheet and depreciated over time34
Cloud consultant fees, data center electric bill, spot instances, and disposable virtual machines are not examples of capital expenditures, but rather operating expenses. Operating expenses are costs that a business incurs to run its day-to-day operations and generate revenue. Operating expenses are also known as OPEX, which stands for Operating Expenses. Operating expenses are usually recurring payments for variable or consumable resources that have a low cost and a short useful life. Operating expenses are recorded as expenses on the income statement and deducted from revenue to calculate profit12
Cloud consultant fees are operating expenses, because they are payments for professional services that help a business implement or optimize its cloud strategy. Cloud consultant fees are recurring payments that vary depending on the scope and duration of the project, and they do not result in the acquisition or improvement of any long-term assets. Cloud consultant fees are also recorded as expenses on the income statement and deducted from revenue to calculate profit5
Data center electric bill is an operating expense, because it is a payment for the utility service that powers the data center equipment. Data center electric bill is a recurring payment that varies depending on the consumption and the rate of electricity, and it does not result in the acquisition or improvement of any long-term assets. Data center electric bill is also recorded as an expense on the income statement and deducted from revenue to calculate profit.
Spot instances and disposable virtual machines are operating expenses, because they are payments for cloud computing resources that are available on-demand and for a short duration. Spot instances and disposable virtual machines are recurring payments that vary depending on the usage and the market price of the resources, and they do not result in the acquisition or improvement of any long-term assets. Spot instances and disposable virtual machines are also recorded as expenses on the income statement and deducted from revenue to calculate profit.
References: 1: 2: page 46 3: 1 4: 3 5: : : :
An organization determines it cannot go forward with a cloud migration due to the risks involved. Which of the following types of risk response does this describe?
Acceptance
Transference
Avoidance
Mitigation
According to the CompTIA Cloud Essentials+ Study Guide, risk response is the process of developing and implementing strategies to address the identified risks in a cloud project1. There are four types of risk response strategies: acceptance, transference, avoidance, and mitigation1. Each strategy has its own advantages and disadvantages, depending on the nature and impact of the risk.
Acceptance is the strategy of acknowledging the risk and its consequences, without taking any action to reduce or eliminate it. This strategy is suitable for risks that have low probability and low impact, or for risks that are unavoidable or too costly to address. Acceptance can be passive, where no contingency plans are prepared, or active, where some reserves or fallback options are allocated1.
Transference is the strategy of shifting the risk and its responsibility to a third party, such as a cloud service provider, an insurance company, or a subcontractor. This strategy is suitable for risks that have high impact but low probability, or for risks that require specialized skills or resources to handle. Transference does not eliminate the risk, but it reduces the exposure and liability of the organization. However, transference also involves some costs and trade-offs, such as loss of control, dependency, or contractual issues1.
Avoidance is the strategy of eliminating the risk and its causes, by changing the scope, plan, or design of the cloud project. This strategy is suitable for risks that have high probability and high impact, or for risks that are unacceptable or intolerable for the organization. Avoidance can be effective in removing the threat, but it can also result in missed opportunities, reduced benefits, or increased costs1.
Mitigation is the strategy of reducing the probability and/or impact of the risk, by implementing some preventive or corrective actions. This strategy is suitable for risks that have moderate probability and impact, or for risks that can be controlled or minimized. Mitigation can be proactive, where actions are taken before the risk occurs, or reactive, where actions are taken after the risk occurs1.
In the given scenario, an organization determines it cannot go forward with a cloud migration due to the risks involved. This describes the avoidance strategy, as the organization is eliminating the risk and its causes by changing the plan of the cloud project. The organization is avoiding the potential negative consequences of the cloud migration, but it is also foregoing the potential benefits and opportunities of the cloud adoption. References: 1: Chapter 7, page 241-243
Which of the following deployment models includes application components on a company’s network as well as on the Internet?
Private
Public
Community
Hybrid
A hybrid cloud deployment model includes application components on a company’s network as well as on the Internet. A hybrid cloud is a combination of two or more cloud deployment models, such as public, private, or community, that are connected by a common network or technology. A hybrid cloud allows the company to leverage the benefits of both public and private clouds, such as scalability, cost-efficiency, security, and control. A hybrid cloud can also enable the company to use different cloud services for different types of workloads, such as sensitive data, high-performance computing, or disaster recovery12. References: CompTIA Cloud Essentials+ Certification | CompTIA IT Certifications, CompTIA Cloud Essentials+: Essential Cloud Principles, CompTIA Cloud Essentials CLO-002 Certification Study Guide, CompTIA Cloud+ Certification Exam Objectives
Which of the following types of risk is MOST likely to be associated with moving all data to one cloud provider?
Vendor lock-in
Data portability
Network connectivity
Data sovereignty
Vendor lock-in is the type of risk that is most likely to be associated with moving all data to one cloud provider. Vendor lock-in refers to the situation where a customer is dependent on a particular vendor’s products and services to such an extent that switching to another vendor becomes difficult, time-consuming, or expensive. Vendor lock-in can limit the customer’s flexibility, choice, and control over their cloud environment, and expose them to potential issues such as price increases, service degradation, security breaches, or compliance violations. Vendor lock-in can also prevent the customer from taking advantage of new technologies, innovations, or opportunities offered by other vendors. Vendor lock-in can be caused by various factors, such as proprietary formats, standards, or protocols, lack of interoperability or compatibility, contractual obligations or penalties, or high switching costs12
References: CompTIA Cloud Essentials+ Certification Exam Objectives3, CompTIA Cloud Essentials+ Study Guide, Chapter 2: Business Principles of Cloud Environments2, Moving All Data to One Cloud Provider: Understanding Risks1
A Chief Information Officer (CIO) wants to identify two business units to be pilots for a new cloud project. A business analyst who was recently assigned to this project will be selecting a cloud provider. Which of the following should the business analyst do FIRST?
Conduct a feasibility study of the environment.
Conduct a benchmark of all major systems.
Draw a matrix diagram of the capabilities of the cloud providers.
Gather business and technical requirements for key stakeholders.
The first step for the business analyst to select a cloud provider for the new cloud project is to gather business and technical requirements for key stakeholders. Business requirements are the needs and expectations of the business units and end users, such as the goals, benefits, and outcomes of the project. Technical requirements are the specifications and constraints of the cloud solution, such as the performance, availability, security, and scalability. Gathering business and technical requirements is essential to understand the scope, objectives, and criteria of the project, and to evaluate and compare different cloud providers based on their capabilities and offerings1.
Conducting a feasibility study of the environment is a possible next step after gathering the requirements, to assess the viability and suitability of the cloud project, and to identify the risks, costs, and benefits of moving to the cloud2. Conducting a benchmark of all major systems is another possible step after gathering the requirements, to measure the current performance and utilization of the existing systems, and to determine the optimal configuration and resources for the cloud solution3. Drawing a matrix diagram of the capabilities of the cloud providers is a possible step after gathering the requirements and conducting the feasibility study and the benchmark, to compare and contrast the features and services of different cloud providers, and to select the best fit for the project4.
References:
A large enterprise has the following invoicing breakdown of current cloud consumption spend:
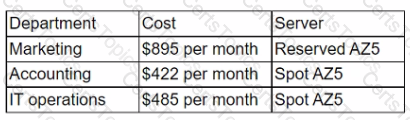
The level of resources consumed by each department is relatively similar. Which of the following is MOST likely affecting monthly costs?
The servers in use by the marketing department are in an availability zone that is generally expensive.
The servers in use by the accounting and IT operations departments are in different geographic zones with lower pricing.
The accounting and IT operations departments are choosing to bid on non-committed resources.
The marketing department likely stores large media files on its servers, leading to increased storage costs.
The marketing department likely stores large media files on its servers, leading to increased storage costs. This is because the marketing department is responsible for creating and distributing various types of digital content, such as videos, images, podcasts, and webinars, to promote the products and services of the enterprise. These media files tend to be large in size and require more storage space than other types of data, such as text documents or spreadsheets. Therefore, the marketing department consumes more storage resources than the other departments, which increases the monthly cloud costs for the enterprise. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 3: Cloud Service and Delivery Models, Section 3.2: Cloud Storage, Page 97
Which of the following describes the process of moving an application from an isolated data center to reduce latency and ensure close proximity to end users?
Replication
Zones
Geo-redundancy
Backup
Geo-redundancy is the distribution of mission-critical components or infrastructures, such as servers, across multiple data centers that reside in different geographic locations1. Geo-redundancy acts as a safety net in case the primary site fails or in the event of a disaster or an outage that impacts an entire region1. Geo-redundancy also reduces latency and ensures close proximity to end users by delivering web content from the nearest data center2. Geo-redundancy is a common feature of cloud computing, as it provides high availability, reliability, and performance for cloud applications and services2.
Replication is the process of copying data from one location to another, such as from a primary site to a secondary site, or from one cloud provider to another3. Replication is a necessary but not sufficient condition for geo-redundancy, as it does not guarantee that the replicated data is accessible or consistent across different regions3. Replication can also introduce operational complexity and data synchronization issues3.
Zones are logical or physical partitions of a cloud provider’s infrastructure that offer high availability and fault tolerance within a region4. Zones are usually located in the same or nearby data centers, and are connected by low-latency network links4. Zones can help distribute the workload and prevent single points of failure, but they do not provide geo-redundancy, as they are still vulnerable to regional outages or disasters4.
Backup is the process of creating and storing copies of data for the purpose of recovery in case of data loss or corruption5. Backup is an important part of data protection and disaster recovery, but it does not provide geo-redundancy, as it does not ensure that the backup data is available or up-to-date in different regions5. Backup can also have longer recovery time and higher cost than geo-redundancy5. References: Use geo-redundancy to design highly available applications; Geo Redundancy Explained | Cloudify; Georedundancy - Open Telekom Cloud; Why geo-redundancy for cloud infrastructure is a ‘must have’; Geo-Redundancy: Why Is It So Important? | Unitrends.
Which of the following concepts is the backup and recovery of data considered?
Risk avoidance
Confidentiality
Integrity
Availability
Backup and recovery of data is considered a concept of availability, which is one of the three pillars of information security, along with confidentiality and integrity. Availability means that data and systems are accessible and usable by authorized users when needed. Backup and recovery of data ensures that data can be restored in case of loss, corruption, or disaster, and that business operations can continue or resume with minimal downtime. Cloud backup and recovery involves creating and storing copies of data in a secondary, offsite storage location, and using the copies to restore the original data in the event of data loss1. Cloud backup and recovery offers many benefits, such as scalability, cost-effectiveness, reliability, and automation234. References: Cloud Essentials+ CLO-002 Study Guide, Chapter 2: Cloud Concepts, Section 2.3: Explain aspects of IT security in the cloud, p. 47. Backup And Disaster Recovery | Google CloudHow does backup and data recovery work in the Cloud? - Devoteam G CloudData Recovery Explained | IBMWhat is Cloud Backup and Recovery | Rackspace Technology
The optimal, sequential order in which cloud resources should be recovered in the event of a major failure would be defined in the:
recovery point objective.
disaster recovery plan.
incident response plan.
network topology diagram.
A disaster recovery plan (DRP) is a document that defines the procedures and resources needed to restore normal operations after a major disruption. A DRP typically includes the following elements:
One of the key components of a DRP is the recovery sequence, which is the optimal, sequential order in which cloud resources should be recovered in the event of a major failure. The recovery sequence is based on the priority and dependency of the resources, as well as the recovery time objective (RTO) and recovery point objective (RPO) of the business. The recovery sequence helps to minimize the downtime and data loss, and ensure the continuity of the business operations.
A recovery point objective (RPO) is the maximum acceptable amount of data loss measured in time. It indicates how often the data should be backed up and how much data can be restored after a disaster. A recovery time objective (RTO) is the maximum acceptable amount of time that a system or application can be offline after a disaster. It indicates how quickly the system or application should be restored and how much downtime can be tolerated by the business.
An incident response plan (IRP) is a document that defines the procedures and actions to be taken in response to a security breach or cyberattack. An IRP typically includes the following elements:
A network topology diagram is a visual representation of the physical and logical layout of a network. It shows the devices, connections, and configurations of the network. A network topology diagram can help to identify the potential points of failure, the impact of a failure, and the recovery options for a network. However, it does not define the optimal, sequential order in which cloud resources should be recovered in the event of a major failure.
References: The following sources were used to create this answer:
Each time a new virtual machine is created, a systems administrator creates a new script to accomplish tasks such as obtaining an IP, provisioning a virtual machine, and populating information in a change management database. Creating a new script to coordinate all of these existing scripts into one is BEST an example of:
automation.
orchestration.
collaboration.
federation.
Orchestration is the process of coordinating multiple automated tasks to create a dynamic and complex workflow1. Orchestration can simplify and streamline the management of cloud resources and services by integrating different scripts, tools, and platforms2. Creating a new script to coordinate all of the existing scripts into one is an example of orchestration, as it involves managing multiple automated tasks to accomplish a larger goal, such as provisioning a virtual machine and updating a change management database. Automation, on the other hand, refers to automating a single task or a small number of related tasks, such as obtaining an IP or populating information in a database1. Automation does not require coordination or decision-making, unlike orchestration. Collaboration and federation are not related to the question, as they refer to the interaction and integration of different cloud providers or users, not the automation or orchestration of cloud tasks3. References: Orchestration vs Automation: The Main Differences - phoenixNAP; Cloud Automation vs Cloud Orchestration: Understanding the Differences; CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 3: Cloud Computing Concepts, pages 85-86.
A company wants to deploy an application in a public cloud. Which of the following service models gives the MOST responsibility to the provider?
PaaS
IaaS
BPaaS
SaaS
SaaS stands for Software as a Service, which is a cloud service model that gives the most responsibility to the provider. In SaaS, the provider delivers the entire software application to the customer over the internet, without requiring any installation, configuration, or maintenance on the customer’s side. The customer only needs a web browser or a thin client to access the software, which is hosted and managed by the provider. The provider is responsible for the security, availability, performance, and updates of the software, as well as the underlying infrastructure, platform, and middleware. The customer has no control over the software, except for some limited customization and configuration options. The customer pays for the software usage, usually on a subscription or pay-per-use basis.
SaaS is different from other service models, such as PaaS, IaaS, or BPaaS. PaaS stands for Platform as a Service, which is a cloud service model that provides the customer with a platform to develop, run, and manage applications without worrying about the infrastructure. The provider is responsible for the infrastructure, operating system, middleware, and runtime environment, while the customer is responsible for the application code, data, and configuration. IaaS stands for Infrastructure as a Service, which is a cloud service model that provides the customer with the basic computing resources, such as servers, storage, network, and virtualization. The provider is responsible for the physical infrastructure, while the customer is responsible for the operating system, middleware, runtime, application, and data. BPaaS stands for Business Process as a Service, which is a cloud service model that provides the customer with a complete business process, such as payroll, accounting, or human resources. The provider is responsible for the software, platform, and infrastructure that support the business process, while the customer is responsible for the input and output of the process. References: Cloud Service Models - CompTIA Cloud Essentials+ (CLO-002) Cert Guide, What is SaaS? Software as a service explained | InfoWorld, What is SaaS? Software as a Service Explained - Salesforce.com, What is SaaS? Software as a Service Definition - AWS
An organization has experienced repeated occurrences of system configurations becoming incorrect over time. After implementing corrections on all system configurations across the enterprise, the Chief Information Security Officer (CISO) purchased an automated tool that will monitor system configurations and identify any deviations. In the future, whic' if th following should be used to identify incorrectly configured systems?
Baseline
Gap analysis
Benchmark
Current and future requirements
A baseline is a standard or reference point that is used to measure and compare the current state of a system or process. A baseline can be established for various aspects of a system, such as performance, security, configuration, functionality, or quality. A baseline can help to identify deviations, anomalies, or changes that occur over time, and to evaluate the impact of those changes on the system or process. A baseline can also help to restore a system or process to its original or desired state, by providing a reference for corrective actions. In this case, the organization has experienced repeated occurrences of system configurations becoming incorrect over time, which can affect the security, reliability, and functionality of the systems. After implementing corrections on all system configurations across the enterprise, the CISO purchased an automated tool that will monitor system configurations and identify any deviations. In the future, the organization should use a baseline to identify incorrectly configured systems, by comparing the current system configurations with the baseline system configurations that were established after the corrections. A baseline can help the organization to detect and prevent configuration drift, which is the gradual but unintentional divergence of a system’s actual configuration settings from its secure baseline configuration. A baseline can also help the organization to apply configuration management, which is the process of planning, identifying, controlling, and verifying the configuration of a system or process throughout its lifecycle. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Cloud Security, Section 4.2: Cloud Security Concepts, Page 153. What a Baseline Configuration Is and How to Prevent Configuration Drift - Netwrix1 Configuration Baselines - AcqNotes2
Which of the following would help a company avoid failure of a cloud project due to a lack of adherence of the company’s operations and business processes to a cloud solution?
Cloud managed services
Company baseline
Proof of value
Industry benchmarks
A proof of value (POV) is a method of testing a cloud solution before fully adopting it, to ensure that it meets the company’s operations and business processes. A POV can help a company avoid failure of a cloud project by validating the feasibility, functionality, and benefits of the cloud solution, and identifying any gaps or issues that need to be resolved. A POV can also help a company compare different cloud solutions and select the best one for their needs. A POV is different from a proof of concept (POC), which is a more technical demonstration of the cloud solution’s capabilities and performance. References: CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002), Chapter 3: Cloud Planning, Section 3.2: Cloud Adoption, Subsection 3.2.2: Proof of Value1
Which of the following are aspects of cloud data availability? (Choose two.)
Resource tagging
Data sovereignty
Locality
Zones
Geo-redundancy
Auto-scaling
Cloud data availability is the process of ensuring that data is accessible to end users and applications, when and where they need it. It defines the degree or extent to which data is readily usable along with the necessary IT and management procedures, tools and technologies required to enable, manage and continue to make data available1. Cloud data availability is influenced by several aspects, such as:
Resource tagging is the practice of assigning metadata or labels to cloud resources, such as instances, volumes, or buckets. It is used to organize, manage, and monitor cloud resources and data, but it does not directly affect data availability.
Data sovereignty is the concept that data is subject to the laws and regulations of the country or region where it is stored or processed. It is a legal and compliance issue that affects data security, privacy, and governance, but it does not directly affect data availability.
Locality is the concept that data is stored or processed close to the source or destination of the data. It is used to optimize data performance, latency, and bandwidth, but it does not directly affect data availability.
Auto-scaling is the practice of automatically adjusting the amount or type of cloud resources, such as instances, nodes, or pods, based on the demand or load of the data. It is used to optimize data efficiency, scalability, and reliability, but it does not directly affect data availability. References:
A company is migrating its e-commerce platform to a cloud service provider. The e-commerce site has a significant number of images. Which of the following is the BEST storage type for storing the images?
Object
Cold
File
Block
Object storage is a type of cloud storage that stores data as objects, which consist of data and metadata. Object storage is ideal for storing large amounts of unstructured data, such as images, videos, audio, documents, etc. Object storage provides high scalability, durability, and availability, as well as easy access via HTTP or REST APIs. Object storage is also more cost-effective than other types of storage, such as block or file storage, which are more suitable for structured data or applications that require high performance or low latency. References: CompTIA Cloud Essentials+ Certification Exam Objectives1, CompTIA Cloud Essentials+ Study Guide, Chapter 4: Cloud Storage2
An architect recently discovered new opportunities the cloud can provide to the company. A business analyst is currently working with the architect to document the business use-case scenarios. Which of the following should be the architect’s NEXT step?
Initialize a PoC.
Conduct a feasibility study.
Perform a gap analysis.
Gather cloud requirements.
After documenting the business use-case scenarios, the architect’s next step should be to conduct a feasibility study. A feasibility study is an analysis of the viability and suitability of a proposed solution or project, such as migrating to the cloud. A feasibility study evaluates the technical, operational, financial, legal, and ethical aspects of the solution, as well as the risks and benefits involved. A feasibility study helps the architect to determine if the solution is feasible, desirable, and achievable, and to identify any potential issues or challenges that may arise1. A feasibility study is one of the key components of a cloud assessment, which is a process of evaluating the readiness and suitability of an organization for cloud adoption1.
A proof of concept (PoC) is a demonstration or prototype of a solution that shows how it works and what it can achieve. A PoC is usually done after a feasibility study, when the solution has been proven to be feasible and the requirements have been defined1.
A gap analysis is a comparison of the current state and the desired state of a process, system, or organization. A gap analysis identifies the gaps or differences between the two states, and the actions or resources needed to close them. A gap analysis is usually done after a feasibility study and a PoC, when the solution has been validated and the goals have been established1.
Gathering cloud requirements is the process of collecting and analyzing the needs and expectations of the stakeholders for the cloud solution. Gathering cloud requirements is usually done after a feasibility study and before a PoC, when the solution has been confirmed to be feasible and the scope has been defined1. References: CompTIA Cloud Essentials+ Certification | CompTIA IT Certifications, The New CompTIA Cloud Essentials+: Setting the Foundation For Vendor-specific IT Certifications, CompTIA Cloud Essentials CLO-002 Certification Study Guide
Which of the following cloud characteristics BEST describes the ability to add resources upon request?
Scalability
Portability
Integrity
Availability
Scalability in cloud computing is the ability to scale up or scale down cloud resources as needed to meet demand1. This is one of the main benefits of using the cloud — and it allows companies to better manage resources and costs2. Scalability enables businesses to easily add or remove computing resources, such as computing power, storage, or network capacity, on demand, without significant hardware investment or infrastructure changes3. Scalability ensures that businesses can efficiently and seamlessly handle varying workloads, optimize resource utilization, and enhance the overall reliability and performance of cloud computing systems4. References: What is Cloud Scalability? | Cloud Scale | VMwareExploring Scalability in Cloud Computing: Benefits and Best Practices | MEGAWhat is Cloud Scalability? | SimplilearnWhat Is Cloud Scalability? 4 Benefits For Every Organization - CloudZero
An IT team documented the procedure for upgrading an existing IT resource within the cloud. Which of the following BEST describes this procedure?
Security procedure
Incident management
Change management
Standard operating procedure
Change management is the process of controlling the lifecycle of all changes to IT services, enabling beneficial changes to be made with minimum disruption and risk1. Change management involves documenting, assessing, approving, implementing, and reviewing changes to IT resources, such as hardware, software, configuration, or capacity2. Change management aims to ensure that changes are aligned with the business objectives, requirements, and expectations, and that they are delivered in a timely, efficient, and effective manner3.
A procedure for upgrading an existing IT resource within the cloud is an example of change management, as it describes the steps and actions needed to make a change to the cloud service. A procedure for upgrading an IT resource should include the following elements4:
A security procedure is a set of rules and guidelines that define how to protect IT resources from unauthorized access, use, modification, or destruction5. A security procedure is not the same as a procedure for upgrading an IT resource, as it focuses on the security aspects of the IT service, rather than the change aspects.
An incident management is the process of restoring normal service operation as quickly as possible after an unplanned disruption or degradation. An incident management is not the same as a procedure for upgrading an IT resource, as it focuses on the incident aspects of the IT service, rather than the change aspects.
A standard operating procedure (SOP) is a document that provides detailed instructions on how to perform a routine or repetitive task or activity. A standard operating procedure is not the same as a procedure for upgrading an IT resource, as it focuses on the operational aspects of the IT service, rather than the change aspects. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 6: Cloud Service Management, pages 229-230.
A report identified that several of a company's SaaS applications are against corporate policy. Which of the following is the MOST likely reason for this issue?
Shadow IT
Sensitive data
Encryption
Vendor lock-in
Shadow IT refers to any IT resource used by employees or end users without the IT department’s approval or oversight. This can include SaaS applications that are not aligned with corporate policy or governance. Employees or teams may adopt shadow IT for convenience, productivity, or innovation, but it can also pose significant security risks and compliance concerns. Therefore, it is important for IT organizations to have visibility and control over the IT devices, software, and services used on the enterprise network. References: : CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 1, page 14 : CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 1, page 15 : CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 1, page 16Top of Form
Bottom of Form
A company purchased insurance due to the risks involved with a cloud migration project. Which of the following risk response strategies is this an example of?
Mitigation
Avoidance
Acceptance
Transference
Transference is a risk response strategy that involves shifting the responsibility or impact of a risk to a third party, such as an insurance company, a vendor, or a partner. By purchasing insurance, the company transferred the financial liability of the cloud migration project to the insurance provider, in case of any losses or damages. Transference does not eliminate the risk, but it reduces the exposure of the company to the risk12. References: CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002), Chapter 4: Risk Management, pages 104-105.
Which of the following would BEST provide access to a Windows VDI?
RDP
VPN
SSH
HTTPS
RDP stands for Remote Desktop Protocol, which is a protocol that allows a user to remotely access and control a Windows-based computer or virtual desktop from another device over a network. RDP can be used to provide access to a Windows VDI, which is a virtual desktop infrastructure that delivers Windows desktops and applications as a cloud service. RDP can provide a full graphical user interface, keyboard, mouse, and audio support, as well as features such as clipboard sharing, printer redirection, and file transfer. RDP can be accessed by using the built-in Remote Desktop Connection client in Windows, or by using third-party applications or web browsers. RDP is more suitable for accessing a Windows VDI than other protocols, such as VPN, SSH, or HTTPS, which may not support the same level of functionality, performance, or security. References: CompTIA Cloud Essentials+ Certification Exam Objectives1, CompTIA Cloud Essentials+ Study Guide, Chapter 6: Cloud Connectivity and Load Balancing2, How To Use The Remote Desktop Protocol To Connect To A Linux Server1
A cloud administrator needs to ensure as much uptime as possible for an application. The application has two database servers. If both servers go down simultaneously, the application will go down. Which of the following must the administrator configure to ensure the CSP does not bring both servers down for maintenance at the same time?
Backups
Availability zones
Autoscaling
Replication
Availability zones are logical data centers within a cloud region that are isolated and independent from each other. Availability zones have their own power, cooling, and networking infrastructure, and are connected by low-latency networks. Availability zones help to ensure high availability and fault tolerance for cloud applications by allowing customers to deploy their resources across multiple zones within a region. If one availability zone experiences an outage or maintenance, the other zones can continue to operate and serve the application12
To ensure the CSP does not bring both servers down for maintenance at the same time, the cloud administrator must configure the application to use availability zones. The administrator can deploy the two database servers in different availability zones within the same region, and enable replication and synchronization between them. This way, the application can access either server in case one of them is unavailable due to maintenance or failure. The administrator can also use load balancers and health checks to distribute the traffic and monitor the status of the servers across the availability zones34
Backups are not the best option to ensure the CSP does not bring both servers down for maintenance at the same time, because backups are copies of data that are stored in another location for recovery purposes. Backups can help to restore the data in case of data loss or corruption, but they do not provide high availability or fault tolerance for the application. Backups are usually performed periodically or on-demand, rather than continuously. Backups also require additional storage space and bandwidth, and may incur additional costs.
Autoscaling is not the best option to ensure the CSP does not bring both servers down for maintenance at the same time, because autoscaling is a feature that allows customers to scale their cloud resources up or down automatically, based on predefined conditions such as traffic or utilization levels. Autoscaling can help to optimize the performance and costs of the application, but it does not guarantee high availability or fault tolerance for the application. Autoscaling may not be able to scale the resources fast enough to handle sudden spikes or drops in demand, and it may also introduce additional complexity and overhead for managing the resources.
Replication is not the best option to ensure the CSP does not bring both servers down for maintenance at the same time, because replication is a process of copying and synchronizing data across multiple locations or devices. Replication can help to improve the availability and consistency of the data, but it does not prevent the CSP from bringing both servers down for maintenance at the same time. Replication also depends on the availability and connectivity of the locations or devices where the data is replicated, and it may also increase the network traffic and storage requirements.
References: 1: 2: page 42 3: 4: : page 44 : page 46 : page 48
A company is moving to the cloud and wants to enhance the provisioning of compute, storage, security, and networking. Which of the following will be leveraged?
Infrastructure as code
Infrastructure templates
Infrastructure orchestration
Infrastructure automation
Infrastructure as code (IaC) is a DevOps practice that uses code to define and deploy infrastructure, such as networks, virtual machines, load balancers, and connection topologies1. IaC ensures consistency, repeatability, and scalability of the infrastructure, as well as enables automation and orchestration of the provisioning process2. IaC is different from infrastructure templates, which are predefined configurations that can be reused for multiple deployments3. Infrastructure orchestration is the process of coordinating multiple automation tasks to achieve a desired state of the infrastructure4. Infrastructure automation is the broader term for any technique that uses technology to perform infrastructure tasks without human intervention5.
References:
Which of the following aspects of cloud design enables a customer to continue doing business after a major data center incident?
Replication
Disaster recovery
Scalability
Autoscaling
Disaster recovery is the aspect of cloud design that enables a customer to continue doing business after a major data center incident. Disaster recovery is the process of restoring and resuming the normal operations of IT systems and services after a disaster, such as a natural calamity, a cyberattack, a power outage, or a human error1. Disaster recovery involves creating and storing backup copies of critical data and workloads in a secondary location or multiple locations, which are known as disaster recovery sites. A disaster recovery site can be a physical data center or a cloud-based platform2. Disaster recovery in cloud computing offers many advantages, such as34:
References: What is Disaster Recovery and Why Is It Important? - Google Cloud, What is Disaster Recovery and Why Is It Important? Disaster Recovery In Cloud Computing: What, How, And Why - NAKIVO, Cloud Disaster Recovery vs. Traditional Disaster Recovery. Benefits of Disaster Recovery in Cloud Computing - NAKIVO, Benefits of Cloud-Based Disaster Recovery. Cloud Disaster Recovery (Cloud DR): What It Is & How It Works - phoenixNAP, Benefits of Cloud Disaster Recovery.
A business analyst is comparing used vs. allocated storage cost for each reserved instance on a financial expenditures report related to the cloud. The CSP is currently billing at the following rates for storage:
The operating expenditures the analyst is reviewing are as follows:
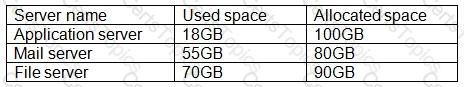
Given this scenario, which of the following servers is costing the firm the least, and which should have storage increased due to over 70% utilization?
Least: File server
Optimize: Application server
Least: Application server Optimize: Mail server
Least: Mail server Optimize: File server
Least: Application server Optimize: File server
The least costing server is the application server because it has the lowest used space and allocated space. The file server should have storage increased due to over 70% utilization because it has the highest used space and allocated space. To calculate the cost of each server, we can use the following formula:
Cost = ($1.50 x Used space) + ($0.75 x Allocated space)
Using this formula, we can find the cost of each server as follows:
The application server has the lowest cost of $466.50, while the file server has the highest cost of $1050. To find the utilization percentage of each server, we can use the following formula:
Utilization = (Used space / Allocated space) x 100%
Using this formula, we can find the utilization percentage of each server as follows:
The file server has the highest utilization percentage of 90%, which means that it is running out of storage space and may affect its performance and availability. The application server has the lowest utilization percentage of 74.4%, which means that it has some unused storage space and may be overprovisioned. Therefore, the file server should have storage increased to reduce its utilization and improve its efficiency, while the application server is costing the firm the least and does not need any changes in its storage allocation. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 3: Cloud Business Principles, Section 3.4: Cloud Billing and Cost Management, Page 87 and [Cloud Storage Utilization and Optimization | CloudHealth by VMware]
Which of the following is a benefit of microservice applications in a cloud environment?
Microservices are dependent on external shared databases found on cloud solutions.
Federation is a mandatory component for an optimized microservice deployment.
The architecture of microservice applications allows the use of auto-scaling.
Microservice applications use orchestration solutions to update components in each service.
Microservice applications are composed of many smaller, loosely coupled, and independently deployable services, each with its own responsibility and technology stack1. One of the benefits of microservice applications in a cloud environment is that they can use auto-scaling, which is the ability to automatically adjust the amount of computing resources allocated to a service based on the current demand2. Auto-scaling can help improve the performance, availability, and cost-efficiency of microservice applications, as it allows each service to scale up or down according to its own needs, without affecting the rest of the application2. Auto-scaling can also help handle unpredictable or variable workloads, such as spikes in traffic or seasonal fluctuations2. Auto-scaling can be implemented using different cloud services, such as Google Kubernetes Engine (GKE) or Cloud Run, which provide both horizontal and vertical scaling options for microservice applications34. References: 1: IBM, What are Microservices?; 2: AWS, What is Auto Scaling?; 3: Google Cloud, Autoscaling Deployments; 4: Google Cloud, Scaling Cloud Run services
Which of the following is the result of performing a physical-to-virtual migration of desktop workstations?
SaaS
laaS
VDI
VPN
VDI, or Virtual Desktop Infrastructure, is the result of performing a physical-to-virtual migration of desktop workstations. VDI is a technology that allows users to access and run desktop operating systems and applications from a centralized server in a data center or a cloud, instead of from a physical machine on their premises. VDI provides users with virtual desktops that are delivered over a network to various devices, such as laptops, tablets, or thin clients1. VDI offers several benefits, such as improved security, reduced costs, increased flexibility, and enhanced performance2.
SaaS, or Software as a Service, is not the result of performing a physical-to-virtual migration of desktop workstations, but a cloud service model that provides ready-to-use software applications that run on the cloud provider’s infrastructure and are accessed via a web browser or an API3. SaaS does not involve migrating desktop workstations, but using software applications that are hosted and managed by the cloud provider.
IaaS, or Infrastructure as a Service, is not the result of performing a physical-to-virtual migration of desktop workstations, but a cloud service model that provides access to basic computing resources, such as servers, storage, network, and virtualization, that are hosted on the cloud provider’s data centers and are rented on-demand. IaaS does not involve migrating desktop workstations, but renting infrastructure resources that can be used to host various workloads.
VPN, or Virtual Private Network, is not the result of performing a physical-to-virtual migration of desktop workstations, but a technology that creates a secure and encrypted connection between a device and a network over the internet. VPN does not involve migrating desktop workstations, but connecting to a network that can provide access to remote resources or services. References: What is VDI? Virtual Desktop Infrastructure Definition - VMware; VDI Benefits: 7 Advantages of Virtual Desktop Infrastructure; What is SaaS? Software as a service | Microsoft Azure; [What is IaaS? Infrastructure as a service | Microsoft Azure]; [What is a VPN? | HowStuffWorks].
Which of the following is true about the use of technologies such as JSON and XML for cloud data interchange and automation tasks?
It can cause cloud vendor lock-in
The company needs to define a specific programming language for cloud management.
The same message format can be used across different cloud platforms.
It is considered an unsafe format of communication.
JSON and XML are both data serialization formats that allow you to exchange data across different applications, platforms, or systems in a standardized manner. They are independent of any programming language and can be used across different cloud platforms. They do not cause cloud vendor lock-in, as they are open and interoperable formats. They do not require the company to define a specific programming language for cloud management, as they can be parsed and processed by various languages. They are not considered unsafe formats of communication, as they can be encrypted and validated for security purposes. References: CompTIA Cloud Essentials+ Certification | CompTIA IT Certifications, CompTIA Cloud Essentials+, CompTIA Cloud Essentials CLO-002 Certification Study Guide
A company is considering moving its database application to a public cloud provider. The application is regulated and requires the data to meet confidentiality standards. Which of the following BEST addresses this requirement?
Authorization
Validation
Encryption
Sanitization
Encryption is the process of transforming data into an unreadable format using a secret key or algorithm. Encryption is the best way to address the requirement of data confidentiality, as it ensures that only authorized parties can access and understand the data, while unauthorized parties cannot. Encryption can protect data at rest, in transit, and in use, which are the three possible states of data in cloud computing environments1. Encryption can also help comply with various regulations and standards that require data protection, such as GDPR, HIPAA, or PCI DSS2.
Authorization, validation, and sanitization are not the best ways to address the requirement of data confidentiality, as they do not provide the same level of protection as encryption. Authorization is the process of granting or denying access to data or resources based on the identity or role of the user or system. Authorization can help control who can access the data, but it does not prevent unauthorized access or leakage of the data3. Validation is the process of verifying the accuracy, completeness, and quality of the data. Validation can help ensure the data is correct and consistent, but it does not prevent the data from being exposed or compromised4. Sanitization is the process of removing sensitive or confidential data from a storage device or a data set. Sanitization can help prevent the data from being recovered or reused, but it does not protect the data while it is stored or processed5. References: Data security and encryption best practices; An Overview of Cloud Cryptography; What is Data Validation? | Talend; Data Sanitization - an overview | ScienceDirect Topics; What is Encryption? | Cloudflare.
A business analyst is drafting a risk assessment.
Which of the following components should be included in the draft? (Choose two.)
Asset management
Database type
Encryption algorithms
Certificate name
Asset inventory
Data classification
Explanation: A risk assessment is a process of identifying, analyzing, and controlling hazards and risks within a situation or a place1. According to the CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002), a risk assessment should include the following steps2:
Based on these steps, two components that should be included in the draft of a risk assessment are asset inventory and data classification. Asset inventory is the process of identifying and documenting the assets that are within the scope of the assessment1. Data classification is the process of categorizing data based on its sensitivity, value, and criticality to the organization3. These components are essential for determining the potential risks and impacts that could affect the assets and data, and for applying the appropriate controls and protection levels.
A company is required to move its human resources application to the cloud to reduce capital expenses. The IT team does a feasibility analysis and learns the application requires legacy infrastructure and cannot be moved to the cloud.
Which of the following is the MOST appropriate cloud migration approach for the company?
Lift and shift
Hybrid
Rip and replace
In-place upgrade
A hybrid cloud migration approach involves using a combination of on-premises and cloud resources to host an application. A hybrid cloud migration approach is suitable for applications that have dependencies or requirements that cannot be met by the cloud alone, such as legacy infrastructure, compliance, security, or performance1. A hybrid cloud migration approach can help reduce capital expenses by moving some components of the application to the cloud, while retaining others on-premises. A hybrid cloud migration approach can also provide flexibility, scalability, and resilience to the application, as it can leverage the best features of both environments2.
A lift and shift cloud migration approach involves moving an application to the cloud as-is, without making any significant changes to its architecture or configuration. A lift and shift cloud migration approach is not appropriate for applications that require legacy infrastructure and cannot be moved to the cloud, as it would result in compatibility issues, performance degradation, or increased costs3.
A rip and replace cloud migration approach involves discarding an application and replacing it with a new one that is designed for the cloud. A rip and replace cloud migration approach is not appropriate for applications that require legacy infrastructure and cannot be moved to the cloud, as it would result in loss of functionality, data, or customization, as well as increased complexity, risk, and cost4.
An in-place upgrade cloud migration approach involves updating an application to a newer version that is compatible with the cloud, without changing its location or platform. An in-place upgrade cloud migration approach is not appropriate for applications that require legacy infrastructure and cannot be moved to the cloud, as it would not reduce capital expenses or provide any benefits of the cloud. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 2: Cloud Migration, pages 49-50.
A cloud service provider is marketing its new PaaS offering to potential clients. Which of the following companies would MOST likely be interested?
A company specializing in application development
A company with many legacy applications
A company with proprietary systems
A company that outsources support of its IT systems
Which of the following concepts will help lower the attack surface after unauthorized user-level access?
Hardening
Validation
Sanitization
Audit
Hardening is the concept that will help lower the attack surface after unauthorized user-level access. Hardening is the process of securing a system by reducing its vulnerability to attacks. Hardening involves applying patches, updates, and configuration changes to eliminate or mitigate known weaknesses. Hardening also involves disabling or removing unnecessary services, features, and accounts that could be exploited by attackers. Hardening can help lower the attack surface by reducing the amount of code running, the number of entry points available, and the potential damage that can be caused by unauthorized access. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Cloud Security, Section 4.2: Cloud Security Concepts, Page 153.
A company deploys a data management capability that reduces RPO. Which of the following BEST describes the capability needed?
Locality
Replication
Portability
Archiving
Replication is a data management capability that involves creating and maintaining copies of data across multiple locations or systems1. Replication can help reduce the Recovery Point Objective (RPO) of an application, which is the maximum acceptable amount of data loss measured in time2. By replicating data frequently and consistently, the risk of losing data in the event of a disruption or failure is minimized, as the data can be restored from the most recent replica. Replication can also improve the availability, performance, and scalability of an application, as the data can be accessed from multiple sources and distributed across different regions3.
Locality is a data management capability that refers to the physical location or proximity of data to the users or applications that access it4. Locality can affect the latency, bandwidth, and cost of data transfer, as well as the compliance with data sovereignty and privacy regulations. Locality does not directly reduce the RPO of an application, but rather influences the choice of where to store and replicate data.
Portability is a data management capability that refers to the ease of moving data across different platforms, systems, or environments. Portability can enable the interoperability, integration, and migration of data, as well as the flexibility and agility of data management. Portability does not directly reduce the RPO of an application, but rather enables the use of different data sources and destinations.
Archiving is a data management capability that involves moving or copying data that is no longer actively used to a separate storage device or system for long-term retention. Archiving can help optimize the storage space, performance, and cost of data, as well as comply with data retention and preservation policies. Archiving does not directly reduce the RPO of an application, but rather preserves the historical data for future reference or analysis. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 3: Cloud Data Management, pages 97-99.
Which of the following can be used by a client’s finance department to identify the cost of cloud use in a public cloud environment shared by different projects and departments?
Reserved instances
Service level agreement
Resource tagging
RFI from the CSP
Resource tagging is the best option for a client’s finance department to identify the cost of cloud use in a public cloud environment shared by different projects and departments. Resource tagging is a feature that allows users to assign metadata to their cloud resources. These tags, which consist of a key and a value, make it easier to manage, search for, and filter resources1. Resource tagging can help to manage costs effectively, especially in large-scale cloud environments, by enabling the following capabilities2:
The other options are not as suitable as resource tagging for the client’s finance department to identify the cost of cloud use because:
References:
Which of the following are the appropriate responses to risks?
Mitigate, accept, avoid, validate
Migrate, accept, avoid, transfer
Mitigate, accept, avoid, transfer
Migrate, accept, avoid, validate
According to the CompTIA Cloud Essentials+ CLO-002 Study Guide, there are four common risk response types: avoid, share or transfer, mitigate, and accept1. These are the appropriate responses to risks, depending on the risk type, assessment, and attitude. The other options are incorrect because they include terms that are not valid risk responses. For example, migrate is not a risk response, but a cloud deployment strategy. Validate is not a risk response, but a quality assurance technique. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Cloud Security, Section 4.2: Cloud Security Concepts, Page 153.
Which of the following risks can an organization transfer by adopting the cloud?
Data breach due to a break-in at the facility
Data sovereignty due to geo-redundancy
Data loss due to incomplete backup sets
Data misclassification due to human error
One of the risks that an organization can transfer by adopting the cloud is data breach due to a break-in at the facility. This is because the cloud service provider (CSP) is responsible for the physical security of the data center where the data is stored and processed. The CSP should have adequate measures to prevent unauthorized access, theft, or damage to the hardware and infrastructure. By outsourcing the data storage and processing to the CSP, the organization transfers the risk of physical breach to the CSP. However, the organization still retains the risk of data breach due to other factors, such as network attacks, misconfiguration, or human error. Therefore, the organization should also implement appropriate controls to protect the data in transit and at rest, such as encryption, authentication, and monitoring. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 5: Risk Management, page 1661 and page 1692. The Top Cloud Computing Risk Treatment Options | CSA3.
Due to local natural disaster concerns, a cloud customer is transferring all of its cold storage data to servers in a safer geographic region. Which of the following risk response techniques is the cloud customer employing?
Avoidance
Transference
Mitigation
Acceptance
Avoidance is a risk response technique that involves changing the project plan to eliminate the risk or protect the project objectives from its impact. Avoidance can be done by modifying the scope, schedule, cost, or quality of the project. Avoidance is usually the most effective way to deal with a risk, but it may not always be possible or desirable. In this case, the cloud customer is transferring all of its cold storage data to servers in a safer geographic region, which means they are changing the location of their data storage to avoid the risk of a natural disaster affecting their data. This way, they are eliminating the possibility of losing their data due to a natural disaster in their original region. This is an example of avoidance as a risk response technique. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Cloud Security, Section 4.2: Cloud Security Concepts, Page 153. 5 Risk Response Strategies - ProjectEngineer1
A business analyst is writing a disaster recovery strategy. Which of the following should the analyst include in the document? (Select THREE).
Capacity on demand
Backups
Resource tagging
Replication
Elasticity
Automation
Geo-redundancy
A disaster recovery strategy is a plan that defines how an organization can recover its data, systems, and operations in the event of a disaster, such as a natural calamity, a cyberattack, or a human error. A disaster recovery strategy should include the following elements12:
References: [CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002)], Chapter 4: Risk Management, pages 105-106.
An analyst is reviewing a report on a company's cloud resource usage. The analyst has noticed many of the cloud instances operate at a fraction of the full processing capacity. Which of the following actions should the analyst consider to lower costs and improve efficiency?
Consolidating into fewer instances
Using spot instances
Right-sizing compute resource instances
Negotiating better prices on the company's reserved instances
Right-sizing compute resource instances is the process of matching instance types and sizes to workload performance and capacity requirements at the lowest possible cost. It’s also the process of identifying opportunities to eliminate or downsize instances without compromising capacity or other requirements, which results in lower costs and higher efficiency1. Right-sizing is a key mechanism for optimizing cloud costs, but it is often ignored or delayed by organizations when they first move to the cloud. They lift and shift their environments and expect to right-size later. Speed and performance are often prioritized over cost, which results in oversized instances and a lot of wasted spend on unused resources2.
Right-sizing compute resource instances is the best action that the analyst should consider to lower costs and improve efficiency, as it can help reduce the amount of resources and money spent on instances that operate at a fraction of the full processing capacity. Right-sizing can also improve the performance and reliability of the instances by ensuring that they have enough resources to meet the workload demands. Right-sizing is an ongoing process that requires continuous monitoring and analysis of the instance usage and performance metrics, as well as the use of tools and frameworks that can simplify and automate the right-sizing decisions1.
Consolidating into fewer instances, using spot instances, or negotiating better prices on the company’s reserved instances are not the best actions that the analyst should consider to lower costs and improve efficiency, as they have some limitations and trade-offs compared to right-sizing. Consolidating into fewer instances can reduce the number of instances, but it does not necessarily optimize the type and size of the instances. Consolidating can also introduce performance and availability issues, such as increased latency, reduced redundancy, or single points of failure3. Using spot instances can reduce the cost of instances, but it also introduces the risk of interruption and termination, as spot instances are subject to fluctuating prices and availability based on the supply and demand of the cloud provider4. Negotiating better prices on the company’s reserved instances can reduce the cost of instances, but it also requires a long-term commitment and upfront payment, which reduces the flexibility and scalability of the cloud environment5. References: Right Sizing - Cloud Computing Services; The 6-Step Guide To Rightsizing Your Instances - CloudZero; Consolidating Cloud Services: How to Do It Right | CloudHealth by VMware; Spot Instances - Amazon Elastic Compute Cloud; Reserved Instances - Amazon Elastic Compute Cloud.
A cloud systems administrator needs to log in to a remote Linux server that is hosted in a public cloud. Which of the following protocols will the administrator MOST likely use?
HTTPS
RDP
Secure Shell
Virtual network computing
Secure Shell (SSH) is a protocol that allows secure and encrypted communication between a client and a server over a network. SSH can be used to log in to a remote Linux server that is hosted in a public cloud, as well as to execute commands, transfer files, or tunnel other protocols. SSH uses public-key cryptography to authenticate the client and the server, and to encrypt the data exchanged between them. SSH is widely supported by most Linux distributions and cloud providers, and it can be accessed by various tools, such as PuTTY, OpenSSH, or WinSCP. SSH is more secure and reliable than other protocols, such as RDP, VNC, or Telnet, which may not support encryption, authentication, or compression. References: CompTIA Cloud Essentials+ Certification Exam Objectives1, CompTIA Cloud Essentials+ Study Guide, Chapter 6: Cloud Connectivity and Load Balancing2, How To Use The Remote Desktop Protocol To Connect To A Linux Server2
Which of the following techniques helps an organization determine benchmarks for application performance within a set of resources?
Auto-scaling
Load testing
Sandboxing
Regression testing
Load testing is the technique that helps an organization determine benchmarks for application performance within a set of resources. Load testing is the process of simulating a high volume of user requests or traffic to a cloud application or service, and measuring its response time, throughput, availability, and reliability. Load testing can help an organization to evaluate the performance and scalability of the cloud application or service, as well as to identify and resolve any bottlenecks, errors, or failures. Load testing can also help the organization to optimize the resource utilization and allocation, and to plan for future growth or peak demand. Load testing can be done using various tools, such as JMeter, LoadRunner, or BlazeMeter12
References: CompTIA Cloud Essentials+ Certification Exam Objectives3, CompTIA Cloud Essentials+ Study Guide, Chapter 6: Cloud Connectivity and Load Balancing4, Cloud Essentials+ Certification Training2
Volume, variety, velocity, and veracity are the four characteristics of:
machine learning.
Big Data.
microservice design.
blockchain.
object storage.
Big Data is a term that refers to data sets that are too large, complex, or diverse to be processed by traditional methods1. Big Data is characterized by four V’s: volume, variety, velocity, and veracity2. Volume refers to the amount of data being generated and collected. Variety refers to the different types of data, such as structured, unstructured, or semi-structured. Velocity refers to the speed at which the data is created, processed, and analyzed. Veracity refers to the quality and reliability of the data.
References:
A systems administrator must select a CSP while considering system uptime and access to critical servers. Which of the following is the MOST important criterion when choosing the CSP?
Elasticity
Scalability
Availability
Serviceability
Encryption in transit is the process of protecting data from unauthorized access or modification while it is being transferred from one location to another, such as from an on-premises data center to a cloud service provider. Encryption in transit uses cryptographic techniques to scramble the data and make it unreadable to anyone who intercepts it, except for the intended recipient who has the key to decrypt it. Encryption in transit is one of the best approaches to optimize data security in an IaaS migration, as it reduces the risk of data breaches, tampering, or leakage during the data transfer. Encryption in transit can be implemented using various methods, such as Transport Layer Security (TLS), Secure Sockets Layer (SSL), Internet Protocol Security (IPsec), or Secure Shell (SSH).
Encryption in transit is different from other options, such as reviewing the risk register, performing a vulnerability scan, or performing server hardening. Reviewing the risk register is the process of identifying, analyzing, and prioritizing the potential threats and impacts to the data and the cloud environment. Performing a vulnerability scan is the process of detecting and assessing the weaknesses or flaws in the data and the cloud infrastructure that could be exploited by attackers. Performing server hardening is the process of applying security measures and configurations to the cloud servers to reduce their attack surface and improve their resilience. While these options are also important for data security, they do not directly address the data protection during the migration process, which is the focus of the question. References: What is encryption in transit? - Definition from WhatIs.com, Data Encryption in Transit Guidelines - UC Berkeley Security, Cloud Computing Security - CompTIA Cloud Essentials+ (CLO-002) Cert Guide
Which of the following explains why a cloud provider would establish and publish a format data sanitization policy for its clients?
To establish guidelines for how the provider will cleanse any data being imported during a cloud migration
To be transparent about how the CSP will handle malware infections that may impact systems housing client data
To provide a value add for clients that will assist in cleansing records at no additional charge
To ensure clients feel comfortable about the handling of any leftover data after termination of the contract
A data sanitization policy is a document that defines how a cloud service provider (CSP) will permanently delete or destroy any data that belongs to its clients after the termination of the contract or the deletion of the service. Data sanitization is a process that ensures that the data is not recoverable by any means, even by advanced forensic tools. Data sanitization is important for cloud security and privacy, as it prevents unauthorized access, disclosure, or misuse of the data by the CSP or any third parties. A data sanitization policy can help the CSP demonstrate its compliance with the data protection laws and regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), that may apply to its clients’ data. A data sanitization policy can also help the CSP build trust and confidence with its clients, as it assures them that their data will be handled securely and responsibly, and that they will have full control and ownership of their data. Therefore, option D is the best explanation of why a cloud provider would establish and publish a format data sanitization policy for its clients. Option A is incorrect because it does not explain why a cloud provider would establish and publish a format data sanitization policy for its clients, but rather how the provider will cleanse any data being imported during a cloud migration. Data cleansing is a process that improves the quality and accuracy of the data by removing or correcting any errors, inconsistencies, or duplicates. Data cleansing is not the same as data sanitization, as it does not involve deleting or destroying the data. Option B is incorrect because it does not explain why a cloud provider would establish and publish a format data sanitization policy for its clients, but rather how the CSP will handle malware infections that may impact systems housing client data. Malware is a malicious software that can harm or compromise the systems or data of the CSP or its clients. Malware prevention and detection are important aspects of cloud security, but they are not the same as data sanitization, as they do not involve deleting or destroying the data. Option C is incorrect because it does not explain why a cloud provider would establish and publish a format data sanitization policy for its clients, but rather how the CSP will provide a value add for clients that will assist in cleansing records at no additional charge. Data cleansing, as explained above, is a process that improves the quality and accuracy of the data, not a process that deletes or destroys the data. Data cleansing may or may not be offered by the CSP as a value-added service, but it is not the same as data sanitization, which is a mandatory and essential service for cloud security and privacy. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 5: Cloud Security Principles, Section 5.2: Data Security Concepts, Page 1471 and Data sanitization for cloud storage | Infosec
A business analyst is reviewing a software upgrade plan. The plan mentions the term “hash” value. Which of the following BEST represents what this term implies?
Non-repudiation of data
Integrity of data
Confidentiality of data
Availability of data
A hash value is a unique code that is generated by applying a mathematical algorithm to a piece of data. Hash values are used to ensure the integrity of data, which means that the data has not been altered or corrupted in any way. By comparing the hash value of the original data with the hash value of the received or stored data, one can verify that the data is identical and has not been tampered with. Hash values can also be used for digital signatures, which provide non-repudiation of data, meaning that the sender or owner of the data cannot deny its authenticity or origin. However, hash values alone do not provide confidentiality or availability of data, which are other aspects of data security. Confidentiality means that the data is protected from unauthorized access or disclosure, and availability means that the data is accessible and usable when needed. Hash values do not encrypt or hide the data, nor do they prevent data loss or downtime. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 5: Cloud Security Principles, Section 5.2: Data Security Concepts, Page 1471 and Ensuring Data Integrity with Hash Codes - .NET | Microsoft Learn
Which of the following service models BEST describes a cloud-hosted application in which the end user only creates user access and configures options?
MaaS
SaaS
PaaS
laaS
According to the CompTIA Cloud Essentials objectives and documents, SaaS, or Software as a Service, is the best option for describing a cloud-hosted application in which the end user only creates user access and configures options. SaaS is a cloud service model that delivers and manages software applications over the internet, without requiring the end user to install, update, or maintain any software or hardware on their own devices. SaaS applications are typically accessed through a web browser or a mobile app, and the end user only pays for the usage or subscription of the service. SaaS providers are responsible for the infrastructure, platform, security, and maintenance of the software applications, and the end user only needs to create user access and configure options according to their preferences and needs. SaaS applications are usually designed for specific purposes or functions, such as email, collaboration, CRM, ERP, or accounting.
The other service models are not as suitable for describing a cloud-hosted application in which the end user only creates user access and configures options. MaaS, or Monitoring as a Service, is a type of cloud service that provides monitoring and management of cloud resources and services, such as performance, availability, security, or compliance. MaaS is not a cloud-hosted application, but rather a cloud service that supports other cloud applications. PaaS, or Platform as a Service, is a cloud service model that delivers and manages the hardware and software resources to develop, test, and deploy applications through the cloud. PaaS provides the end user with a cloud-based platform that includes the operating system, middleware, runtime, database, and other tools and services. PaaS providers are responsible for the infrastructure, security, and maintenance of the platform, and the end user only needs to write and manage the code and data of their applications. PaaS applications are usually customized and developed by the end user, rather than provided by the cloud service provider. IaaS, or Infrastructure as a Service, is a cloud service model that delivers and manages the basic computing resources, such as servers, storage, networking, and virtualization, over the internet. IaaS provides the end user with a cloud-based infrastructure that can be used to run any software or application. IaaS providers are responsible for the hardware, security, and maintenance of the infrastructure, and the end user is responsible for the operating system, middleware, runtime, database, and applications. IaaS applications are usually more complex and require more configuration and management by the end user, rather than by the cloud service provider.
A cloud administrator is reviewing the requirements for a SaaS application and estimates downtime will be very expensive for the organization. Which of the following should the administrator configure to minimize downtime? (Choose two.)
Continuous deployment
Right-sizing
Availability zones
Geo-redundancy
Hardening
Backups
Availability zones and geo-redundancy are two strategies that can help minimize downtime for a SaaS application. Availability zones are distinct locations within a cloud region that are isolated from each other and have independent power, cooling, and networking. They provide high availability and fault tolerance by allowing the SaaS application to run on multiple servers across different zones. If one zone fails, the application can continue to operate on the other zones without interruption. Geo-redundancy is the replication of data and services across multiple geographic regions. It provides disaster recovery and business continuity by allowing the SaaS application to switch to another region in case of a major outage or a natural disaster. Geo-redundancy also improves performance and latency by serving users from the nearest region. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 3: Cloud Business Principles, Section 3.3: Cloud Service Level Agreements, Page 751 and Chapter 4: Cloud Design Principles, Section 4.3: Cloud Scalability and Elasticity, Page 1172
A cloud administrator configures a server to insert an entry into a log file whenever an administrator logs in to the server remotely. Which of the following BEST describes the type of policy being used?
Audit
Authorization
Hardening
Access
An audit policy is a set of rules and guidelines that define how to monitor and record the activities and events that occur on a system or network1. An audit policy can help track and report the actions of users, applications, processes, or devices, and provide evidence of compliance, security, or performance issues. An audit policy can also help deter unauthorized or malicious activities, as the users know that their actions are being logged and reviewed.
A cloud administrator who configures a server to insert an entry into a log file whenever an administrator logs in to the server remotely is using an audit policy, as they are enabling the collection and recording of a specific event that relates to the access and management of the server. The log file can then be used to verify the identity, time, and frequency of the administrator logins, and to detect any anomalies or suspicious activities.
An authorization policy is a set of rules and guidelines that define what actions or resources a user or a system can access or perform2. An authorization policy can help enforce the principle of least privilege, which means that users or systems are only granted the minimum level of access or permissions they need to perform their tasks. An authorization policy can also help prevent unauthorized or malicious activities, as the users or systems are restricted from accessing or performing actions that are not allowed or necessary.
A hardening policy is a set of rules and guidelines that define how to reduce the attack surface and vulnerability of a system or network3. A hardening policy can help improve the security and resilience of a system or network, by applying various measures such as disabling unnecessary services, removing default accounts, applying patches and updates, configuring firewalls and antivirus software, etc. A hardening policy can also help prevent unauthorized or malicious activities, as the users or systems are faced with more obstacles and challenges to compromise the system or network.
An access policy is a set of rules and guidelines that define who or what can access a system or network, and under what conditions or circumstances4. An access policy can help control the authentication and identification of users or systems, and the verification and validation of their credentials. An access policy can also help prevent unauthorized or malicious activities, as the users or systems are required to prove their identity and legitimacy before accessing the system or network. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 6: Cloud Service Management, pages 229-230.
A company is moving its long-term archive data to the cloud. Which of the following storage types will the company MOST likely use?
File
Object
Tape
Block
Object storage is a type of cloud storage that stores data as discrete units called objects. Each object has a unique identifier, metadata, and data. Object storage is ideal for storing long-term archive data in the cloud because it offers high scalability, durability, availability, and cost-effectiveness12. Object storage can handle large amounts of unstructured data, such as documents, images, videos, and backups, and allows users to access them from anywhere using a simple web interface3. Object storage also supports features such as encryption, versioning, lifecycle management, and replication to ensure the security and integrity of the archive data45. References: [CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002)], Chapter 2: Cloud Computing Concepts, pages 36-37.
An incident response team requires documentation for an email phishing campaign against a company's email server. Which of the following is the BEST resource to use to start the investigation?
Audit and system logs
Change management procedures
Departmental policies
Standard operating procedures
Audit and system logs are the best resource to use to start the investigation of an email phishing campaign against a company’s email server. Audit and system logs are records of events and activities that occur on a system or a network, such as user login, file access, configuration changes, or network traffic. Audit and system logs can help an incident response team to identify the source, scope, and impact of the phishing attack, as well as to collect evidence, trace the attack steps, and determine the root cause. Audit and system logs can also help the incident response team to evaluate the security posture and controls of the email server, and to recommend remediation and mitigation actions12
References: CompTIA Cloud Essentials+ Certification Exam Objectives3, CompTIA Cloud Essentials+ Study Guide, Chapter 7: Cloud Security, Cloud Essentials+ Certification Trainin
A company’s new systems administrator has been asked to create a new user for the human resources department. Which of the following will help the systems administrator understand the user privileges for each role in the company?
Identity and access control management policy
Classification and management policy
Change management policy
Standard operating procedures
An identity and access control management policy is a document that defines the roles, responsibilities, and rules for managing the identities and access rights of users in an organization1. It specifies how users are authenticated, authorized, and audited when they access the organization’s resources, such as systems, applications, data, and networks1. An identity and access control management policy also describes the processes and procedures for creating, modifying, suspending, and deleting user accounts and privileges, as well as the standards and guidelines for selecting and managing passwords, tokens, certificates, and other authentication factors1. An identity and access control management policy can help the systems administrator understand the user privileges for each role in the company, as it defines the access levels and permissions that are granted to different types of users, such as employees, contractors, vendors, partners, and customers1. The policy also outlines the criteria and conditions for granting, changing, or revoking access rights, based on the principle of least privilege and the need-to-know basis1. By following the identity and access control management policy, the systems administrator can ensure that the new user for the human resources department has the appropriate and secure access to the resources that are relevant to their job function and responsibilities1. References: 1: CompTIA Cloud Essentials+ Certification Study Guide, Second Edition (Exam CLO-002), Chapter 3: Cloud Planning, Section 3.2: Cloud Adoption, Subsection 3.2.1: Identity and Access Management
The legal team is required to share legal proceedings with an outside council. The team uses SaaS fileshares. Which of the following policies will BEST state the requirements for sharing information with external parties?
Information security policy
Communication policy
Resource management policy
Identity control policy
An information security policy is a document that defines the rules and guidelines for protecting the confidentiality, integrity, and availability of data and systems in an organization. It covers topics such as data classification, access control, encryption, backup, incident response, and compliance. An information security policy is essential for ensuring that data is shared securely with external parties, especially when using SaaS fileshares that may have different security standards and features than the organization’s own systems. A communication policy, a resource management policy, and an identity control policy are all related to information security, but they are not as comprehensive and specific as an information security policy. References: CompTIA Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Security in the Cloud, page 149.
A company requires 24 hours' notice when a database is taken offline for planned maintenance. Which of the following policies provides the BEST guidance about notifying users?
Communication policy
Access control policy
Information security policy
Risk management policy
A communication policy is a set of guidelines that defines how an organization communicates with its internal and external stakeholders, such as employees, customers, partners, and regulators. A communication policy typically covers topics such as the purpose, scope, methods, frequency, tone, and responsibilities of communication within and outside the organization. A communication policy also establishes the standards and expectations for communication quality, accuracy, timeliness, and security. A communication policy is essential for ensuring effective, consistent, and transparent communication across the organization and with its stakeholders. A communication policy can help to avoid misunderstandings, conflicts, and errors that may arise from poor or unclear communication. A communication policy can also help to enhance the reputation, trust, and credibility of the organization.
A communication policy provides the best guidance about notifying users when a database is taken offline for planned maintenance, because it specifies how, when, and to whom such notifications should be sent. A communication policy can help to ensure that users are informed in advance, in a clear and courteous manner, about the reason, duration, and impact of the maintenance, and that they are updated on the progress and completion of the maintenance. A communication policy can also help to address any questions, concerns, or feedback that users may have regarding the maintenance. A communication policy can thus help to minimize the disruption and inconvenience caused by the maintenance, and to maintain a positive relationship with the users.
A communication policy is different from the other policies listed in the question, which are not directly related to notifying users about planned maintenance. An access control policy defines the rules and procedures for granting or denying access to information systems and resources based on the identity, role, and privileges of the users. An information security policy outlines the principles and practices for protecting the confidentiality, integrity, and availability of information assets and systems from unauthorized or malicious use, disclosure, modification, or destruction. A risk management policy describes the process and criteria for identifying, assessing, prioritizing, mitigating, and monitoring the risks that may affect the organization’s objectives, operations, and performance. While these policies are important for ensuring the security and reliability of the database and the organization, they do not provide specific guidance about communicating with users about planned maintenance.
References: Cloud Essentials+ CLO-002 Study Guide, Chapter 4: Cloud Service Management, Section 4.2: Explain aspects of change management within a cloud environment, p. 115. What is Cloud Communications? Your Getting Started Guide, Cloud Communications – Defined. Cloud Computing Policy and Guidelines, 1. Introduction. Define corporate policy for cloud governance, Cloud-based IT policies. DEPARTMENT OF COMMUNICATIONS AND DIGITAL TECHNOLOGIES NO. 306 1 April 2021, 5. Function of cloud security policy and standards, Policy should always address.
Copyright © 2021-2026 CertsTopics. All Rights Reserved

