There are several devices on a network that are considered critical and need to be placed into the ISE database and a policy used for them. The organization does not want to use profiling. What must be done to accomplish this goal?
A network engineer must configure a policy rule to check the endpoint. The policy must ensure disk encryption is enabled and the appropriate antivirus software version is installed. Which configuration must the engineer apply to the rule?
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from the Cisco ISE node?
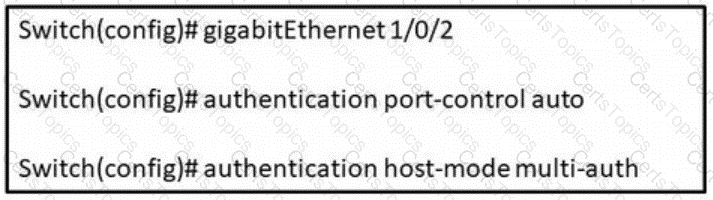
Refer to the exhibit. In which scenario does this switch configuration apply?
A network engineer needs to deploy 802.1x using Cisco ISE in a wired network environment where thin clients download their system image upon bootup using PXE. For which mode must the switch ports be configured?
Which two authentication protocols are supported by RADIUS but not by TACACS+? (Choose two.)
A network administrator is configuring a secondary cisco ISE node from the backup configuration of the primary cisco ISE node to create a high availability pair The Cisco ISE CA certificates and keys must be manually backed up from the primary Cisco ISE and copied into the secondary Cisco ISE Which command most be issued for this to work?
What should be considered when configuring certificates for BYOD?
An endpoint certificate is mandatory for the Cisco ISE BYOD
Which port does Cisco ISE use for native supplicant provisioning of a Windows laptop?
A network engineer is in the predeployment discovery phase o! a Cisco ISE deployment and must discover the network. There is an existing network management system in the network. Which type of probe must be configured to gather the information?
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
An administrator is trying to collect metadata information about the traffic going across the network to gam added visibility into the hosts. This Information will be used to create profiling policies for devices us mg Cisco ISE so that network access policies can be used What must be done to accomplish this task?
What is a valid guest portal type?
A user misplaces a personal phone and wants to blacklist the device from accessing the company network. The company uses Cisco ISE for corporate and BYOD device authentication. Which action must the user take in Cisco ISE?
An administrator replaced a PSN in the distributed Cisco ISE environment. When endpoints authenticate to it, the devices are not getting the right profiles or attributes and as a result, are not hitting the correct policies. This was working correctly on the previous PSN. Which action must be taken to ensure the endpoints get identified?
A network engineer is configuring a network device that needs to filter traffic based on security group tags using a security policy on a routed into this task?
Which supplicant(s) and server(s) are capable of supporting EAP-CHAINING?
Which term refers to an endpoint agent that tries to join an 802 1X-enabled network?
A customer wants to set up the Sponsor portal and delegate the authentication flow to a third party for added security while using Kerberos Which database should be used to accomplish this goal?
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
What is the maximum number of PSN nodes supported in a medium-sized deployment?
An administrator is configuring a Cisco WLC for web authentication Which two client profiling methods are enabled by default if the Apply Cisco ISE Default Settings check box has been selected'? (Choose two.)
What is the difference between how RADIUS and TACACS+ handle encryption?
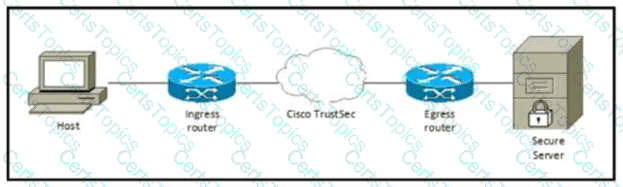
Refer to the exhibit Which component must be configured to apply the SGACL?
An administrator needs to add a new third party network device to be used with Cisco ISE for Guest and BYOD authorizations. Which two features must be configured under Network Device Profile to achieve this? (Choose two.)
An engineer is configuring Cisco ISE policies to support MAB for devices that do not have 802.1X capabilities. The engineer is configuring new endpoint identity groups as conditions to be used in the AuthZ policies, but noticed that the endpoints are not hitting the correct policies. What must be done in order to get the devices into the right policies?
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
What is the difference between how RADIUS and TACACS+ handle encryption?
What does a fully distributed Cisco ISE deployment include?
There is a need within an organization for a new policy to be created in Cisco ISE. It must validate that a specific anti-virus application is not only installed, but running on a machine before it is allowed access to the network. Which posture condition should the administrator configure in order for this policy to work?
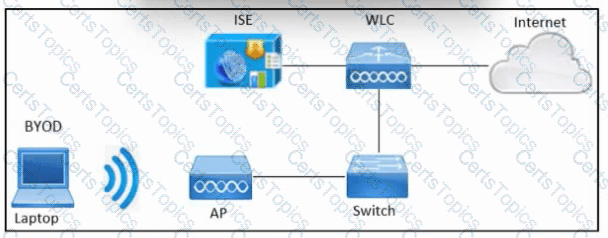
Refer to the exhibit. An engineer must configure BYOD in Cisco ISE. A single SSID must be used to allow BYOD devices to connect to the network. These configurations have been performed on Wireless LAN Controller already:
RADIUS server
BYOD-Dot1x SSID
Which two configurations must be done in Cisco ISE to meet the requirement? (Choose two.)
An engineer has been tasked with standing up a new guest portal for customers that are waiting in the lobby. There is a requirement to allow guests to use their social media logins to access the guest network to appeal to more customers What must be done to accomplish this task?
What are the minimum requirements for deploying the Automatic Failover feature on Administration nodes in a distributed Cisco ISE deployment?
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles?
(Choose two.)
A network engineer has been tasked with enabling a switch to support standard web authentication for Cisco ISE. This must include the ability to provision for URL redirection on authentication Which two commands must be entered to meet this requirement? (Choose two)
What is a difference between RADIUS versus TACACS+ with regards to packet encryption?
An administrator is adding a switch to a network that is running Cisco ISE and is only for IP Phones The phones do not have the ability to authenticate via 802 1X Which command is needed on each switch port for authentication?
An organization is adding new profiling probes to the system to improve profiling on Oseo ISE The probes must support a common network management protocol to receive information about the endpoints and the ports to which they are connected What must be configured on the network device to accomplish this goal?
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two )
Which two features should be used on Cisco ISE to enable the TACACS+ feature? (Choose two )
An engineer deploys Cisco ISE and must configure Active Directory to then use information from Active Directory in an authorization policy. Which two components must be configured, in addition to Active Directory groups, to achieve this goat? (Choose two )
Which two fields are available when creating an endpoint on the context visibility page of Cisco IS? (Choose two)
An administrator is configuring a switch port for use with 802 1X What must be done so that the port will allow voice and multiple data endpoints?
An administrator must configure Cisco ISE to send CoA requests to a Cisco switch using SNMP. These configurations were already performed:
enabled SNMP on the switch
added the switch to Cisco ISE
configured a network device profile
configured the NAD port detection method
configured the operation to be performed on the switch port
configured an authorization profile
Which two configurations must be performed to send the CoA requests? (Choose two.)
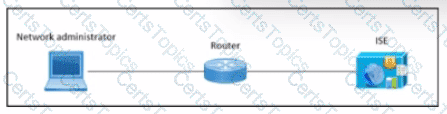
The security engineer for a company has recently deployed Cisco ISE to perform centralized authentication of all network device logins using TACACS+ against the local AD domain. Some of the other network engineers are having a hard time remembering to enter their AD account password instead of the local admin password that they have used for years. The security engineer wants to change the password prompt to "Use Local AD Password:" as a way of providing a hint to the network engineers when logging in. Under which page in Cisco ISE would this change be made?
Using the SAK Active Directory Federation Services server. The configurations were performed:
• created a new SAML Identity provider profile in Cisco ISE
• exported the service provider Information
• configured all the required Active Directory Federation Services configurations
• Imported the Active Directory Federation Services metadata
• configured groups in the new SAML identity
• added attributes to the new SAML identity provider profile
• configured Advanced Settings in the new SAML identity provider profile
Which two actions must be taken to complete the configuration? (Choose two.)
An engineer is configuring a new Cisco ISE node. Context-sensitive information must be shared between the Cisco ISE and a Cisco ASA. Which persona must be enabled?
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node is deregistered?
An engineer is enabling a newly configured wireless SSID for tablets and needs visibility into which other types of devices are connecting to it. What must be done on the Cisco WLC to provide this information to Cisco ISE9
An engineer is unable to use SSH to connect to a switch after adding the required CLI commands to the device to enable TACACS+. The device administration license has been added to Cisco ISE, and the required policies have been created. Which action is needed to enable access to the switch?
What is the minimum certainty factor when creating a profiler policy?
An engineer is configuring Cisco ISE for guest services They would like to have any unregistered guests redirected to the guest portal for authentication then have a CoA provide them with full access to the network that is segmented via firewalls Why is the given configuration failing to accomplish this goal?
A Cisco device has a port configured in multi-authentication mode and is accepting connections only from hosts assigned the SGT of SGT_0422048549 The VLAN trunk link supports a maximum of 8 VLANS What is the reason for these restrictions?
Which two default guest portals are available with Cisco ISE? (Choose two.)
A network administrator is currently using Cisco ISE to authenticate devices and users via 802 1X There is now a need to also authorize devices and users using EAP-TLS. Which two additional components must be configured in Cisco ISE to accomplish this'? (Choose two.)
A network security administrator wants to integrate Cisco ISE with Active Directory. Which configuration action must the security administrator take to accomplish the task?
A network engineer must enable a profiling probe. The profiling must take details through the Active Directory. Where in the Cisco ISE interface would the engineer enable the probe?
Which two features must be used on Cisco ISE to enable the TACACS. feature? (Choose two)
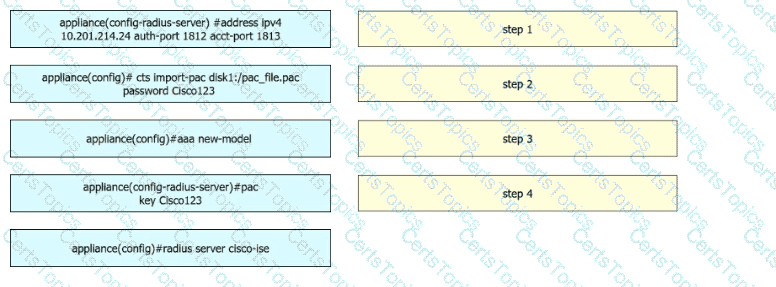
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco IISE. Drag and drop the commands from the left into sequence on the right. Not all options are used.
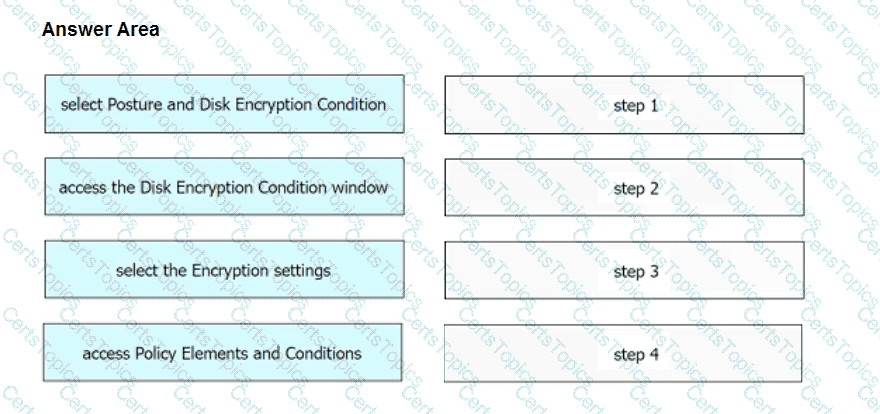
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
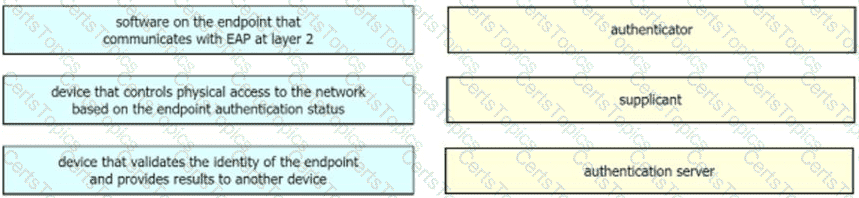
Drag the descriptions on the left onto the components of 802.1X on the right.
An administrator is responsible for configuring network access for a temporary network printer. The administrator must only use the printer MAC address 50:89:65: 18:8: AB for authentication. Which authentication method will accomplish the task?
A network administrator is configuring client provisioning resource policies for client machines and must ensure that an agent pop-up is presented to the client when attempting to connect to the network Which configuration item needs to be added to allow for this'?
An engineer is migrating users from MAB to 802.1X on the network. This must be done during normal business hours with minimal impact to users. Which CoA method should be used?
Refer to the exhibit.
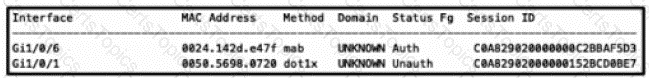
An engineer is configuring a client but cannot authenticate to Cisco ISE During troubleshooting, the show authentication sessions command was issued to display the authentication status of each port Which command gives additional information to help identify the problem with the authentication?
A network engineer must create a guest portal for wireless guests on Cisco ISE. The guest users must not be able to create accounts; however, the portal should require a username and password to connect. Which portal type must be created in Cisco ISE to meet the requirements?
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information system-description and platform-type to profile Cisco IP phones and allow access. Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
An engineer needs to configure a new certificate template in the Cisco ISE Internal Certificate Authority to prevent BYOD devices from needing to re-enroll when their MAC address changes. Which option must be selected in the Subject Alternative Name field?
An organization wants to enable web-based guest access for both employees and visitors The goal is to use a single portal for both user types Which two authentication methods should be used to meet this requirement? (Choose two )
Which nodes are supported in a distributed Cisco ISE deployment?
The security team identified a rogue endpoint with MAC address 00:46:91:02:28:4A attached to the network. Which action must security engineer take within Cisco ISE to effectively
restrict network access for this endpoint?
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
An engineer is configuring 802.1X and is testing out their policy sets. After authentication, some endpoints are given an access-reject message but are still allowed onto the network. What is causing this issue to occur?
What is a method for transporting security group tags throughout the network?
Which two responses from the RADIUS server to NAS are valid during the authentication process? (Choose two)
Refer to the exhibit.
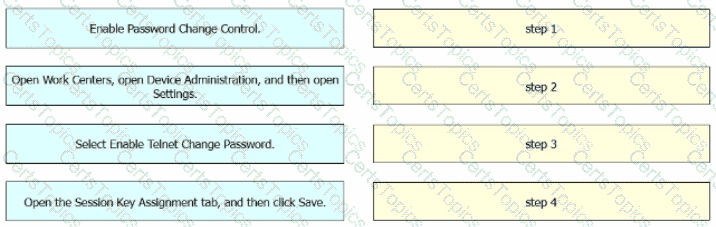
An engineer must configure Cisco ISE to be used as the TACACS+ server for any administrator that signs into the router. Users must be able to change their Telnet password through the TACACS+ server. Drag and drop the configuration steps from the left into the sequence on the right.
Which two ports do network devices typically use for CoA? (Choose two)
Which two external identity stores support EAP-TLS and PEAP-TLS? (Choose two.)
Which two roles are taken on by the administration person within a Cisco ISE distributed environment? (Choose two.)
Which compliance status is set when a matching posture policy has been defined for that endpomt. but all the mandatory requirements during posture assessment are not met?
A network administrator must configura endpoints using an 802 1X authentication method with EAP identity certificates that are provided by the Cisco ISE When the endpoint presents the identity certificate to Cisco ISE to validate the certificate, endpoints must be authorized to connect to the network Which EAP type must be configured by the network administrator to complete this task?
An administrator adds a new network device to the Cisco ISE configuration to authenticate endpoints to the network. The RADIUS test fails after the administrator configures all of the settings in Cisco ISE and adds the proper configurations to the switch. What is the issue"?
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting. Which policy condition must be used in order to accomplish this?
An administrator connects an HP printer to a dot1x enable port, but the printer in not accessible Which feature must the administrator enable to access the printer?
An ISE administrator must change the inactivity timer for MAB endpoints to terminate the authentication session whenever a switch port that is connected to an IP phone does not detect packets from the device for 30 minutes. Which action must be taken to accomplish this task?
Which two external identity stores are supported by Cisco ISE for password types? (Choose two.)