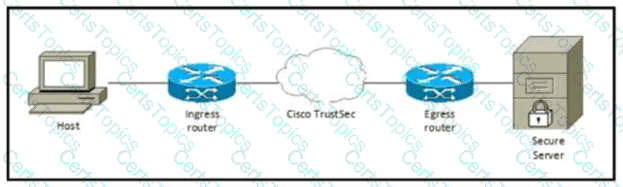
Refer to the exhibit Which component must be configured to apply the SGACL?
An administrator needs to add a new third party network device to be used with Cisco ISE for Guest and BYOD authorizations. Which two features must be configured under Network Device Profile to achieve this? (Choose two.)
An engineer is configuring Cisco ISE policies to support MAB for devices that do not have 802.1X capabilities. The engineer is configuring new endpoint identity groups as conditions to be used in the AuthZ policies, but noticed that the endpoints are not hitting the correct policies. What must be done in order to get the devices into the right policies?
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)