Using Pattern Designer, when configuring the first step in an Identification Section, which one of the following is considered a good practice?
In Service Mapping, which one of the following best represents the process flow of discovery?
Within the CMDB, all application CI Types/Classes are children of which parent class?
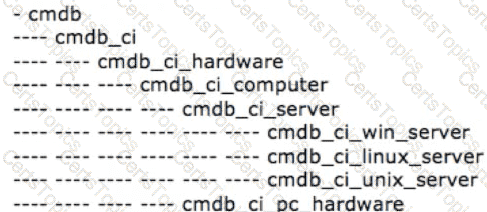
Given the CMDB class structure shown below, if an implementer were to extend the Server [cmdb_ci_server] table, which one of the following best describes the fields that would be inherited by the new table?
Which one of the following best represents the breadth of types of Configuration Items (CIs) discovered by
running Service Mapping?
From Pattern Designer under the CI Attributes section, next to the name field, the key displayed in this example represents?
Which one of the following Linux commands can be used by a non root user to return the process ID listening on port 8080?
How many ServiceNow instances can one MID Server connect to?
When using the Pattern Designer, a Regular Expression parsing strategy is available from which operation?
In Service Mapping, which one of the following is used to discover the applications and outbound connections to other applications that appear on a Service map?
Which best describes what Identification Rules are?
In Service Mapping, which one of the following best describes the process of discovery after an Entry Point is configured?
What are the roles of the Application Service Readiness Dashboard in ML-powered Service Mapping?
Choose 2 answers
Which of the following are created automatically when using the map option Create pattern from generic application?
Which one of the following ECC Queue records contains the XML payload returned from the MID Server that will be processed by the ServiceNow instance?
Which one of the following Regular Expressions could be used to parse the value 5.2.0 from the string?
Version 5.2.0
The application stack is as follows: IIS Web Server with an inclusion connection to an IIS Virtual Directory, and an outbound connection from the IIS Virtual Directory to an MSSQL database.
Which describes the correct number of Discovery Pattern Identification and Connection Sections that evaluate to true when Service Mapping discovers a service with this application stack?
A customer has recently placed check scanners in some of their branches across Europe. The scanners send the scanned images of the checks to the bank's data center through a web service that goes through an F5 load balancer. The images then go through the bank's Apache web servers and are processed by an application server named ImageSmart. Eventually, the images are stored in a cluster of Oracle databases.
The bank's tellers log into ImageSmart through a Citrix Portal and have the capability to review the checks and approve them.
Which one of the following represents most accurately how many business services and entry points are involved in this process?
Using Pattern Designer, which one of the following Delimited Text Parsing Strategies could be used to parse CO from the string:
Location, Denver,CO
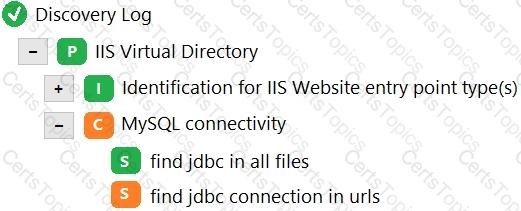
In the following image of the Discovery Log, the green S represents which one of the following?
What describes the main feature offered by Service Mapping Plus?
Which represents the skills needed that a Service Mapping administrator or implementer should have?
Choose 4 answers
Which one of the following Identification Rule (CI Identifier) fields, when selected, determines CMDB update/inserts based on the configuration item's (CI) own attributes, without taking other CIs or relationships into consideration?
Which one of the following is the baseline Identification Rule (CI Identifier) used to determine inserts or updates to all servers discovered by ServiceNow Discovery or Service Mapping?
Predictive Intelligence provides which one of the following benefits?
Service Mapping uses which table to build tag-based maps from?
A CI Type is also known as which one of the following?
What is the function of the Unified Map feature in the Service Mapping Workspace?
Assuming Reconciliation Rules (Reconciliation Definitions) were configured exactly the same for both Data Sources, ServiceNow and ServiceWatch, for the Application [cmdb_ci_appl] table and the following Data Source Precedence Rules are configured.
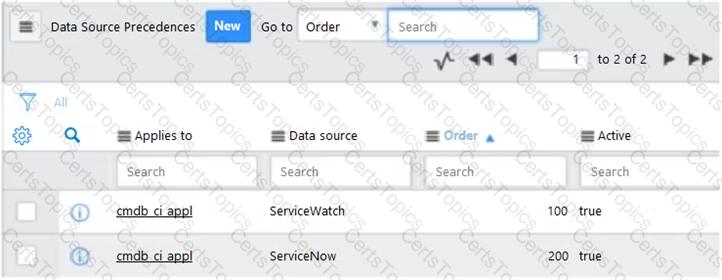
Which one of the following is true?
In Event Management, if a Message key is not passed from an Event, which of the following Alert fields combine to populate the Message key on an Alert?
In Service Mapping, when discovery is started, what is the execution strategy used to run Connection Sections?