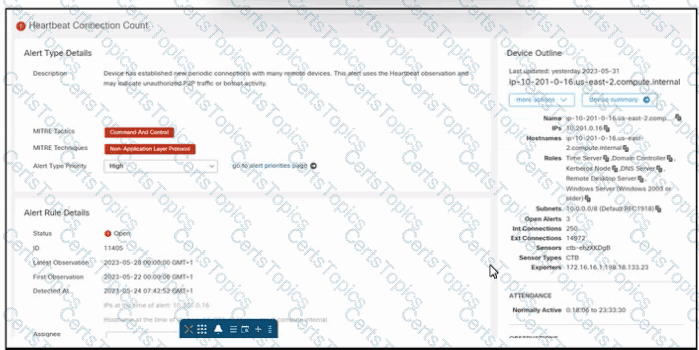
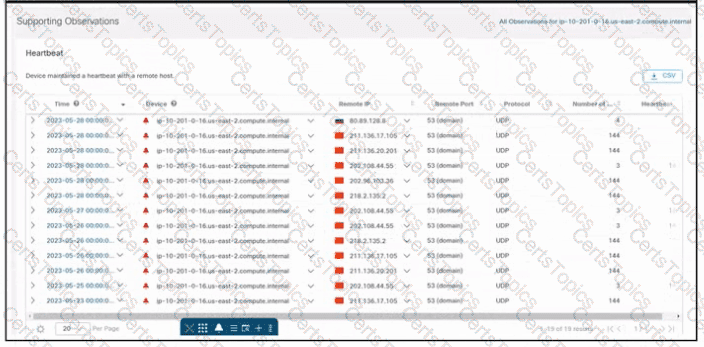
Refer to the exhibit. An engineer is investigating an unauthorized connection issue using Cisco Secure Cloud Analytics. Which two actions must be taken? (Choose two.)
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
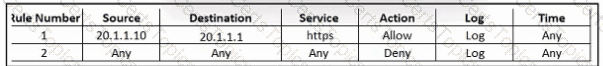
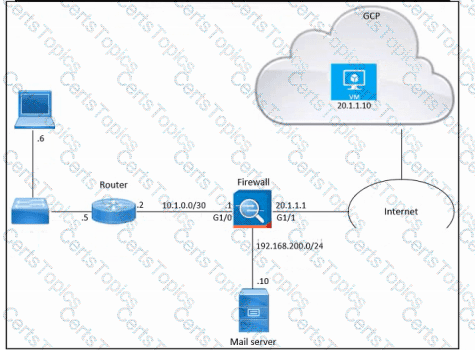
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
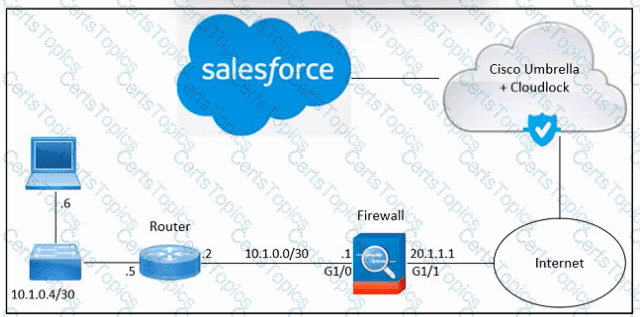
Refer to the exhibit. An engineer must integrate Cisco Cloudlock with Salesforce in an organization. Despite the engineer's successful execution of the Salesforce integration with Cloudlock, the administrator still lacks the necessary visibility. What should be done to meet the requirement?