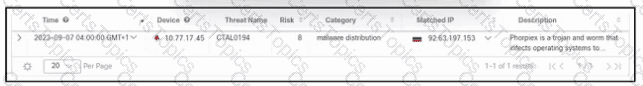
Refer to the exhibit. A security engineer deployed Cisco Secure XDR, and during testing, the log entry shows a security incident. Which action must the engineer take first?
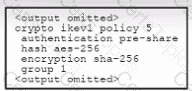
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the requirement? (Choose two.)
What helps prevent drive-by compromise?
What is a crucial component in the MITRE ATT&CK framework?
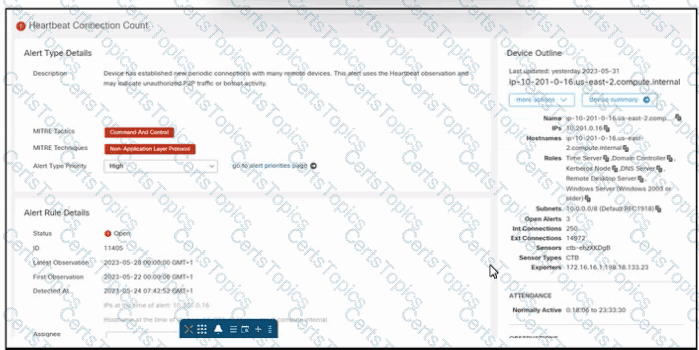
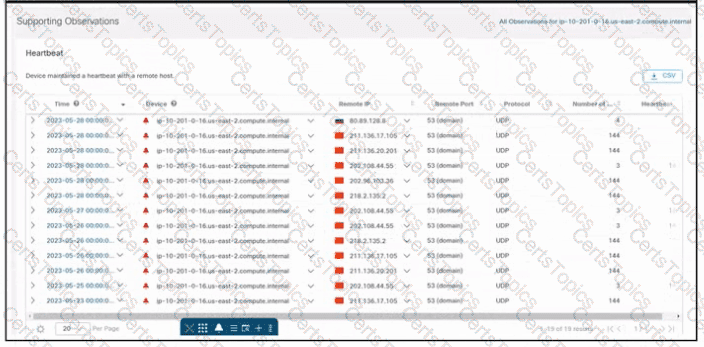
Refer to the exhibit. An engineer is investigating an unauthorized connection issue using Cisco Secure Cloud Analytics. Which two actions must be taken? (Choose two.)
Which types of algorithm does a web application firewall use for zero-day DDoS protection?
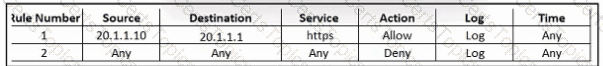
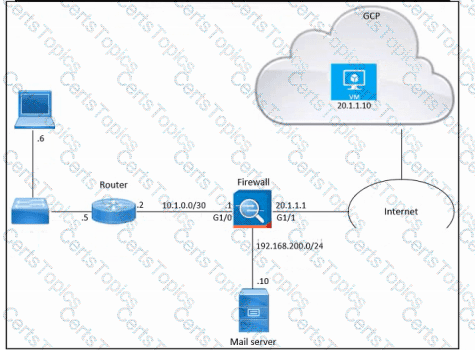
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
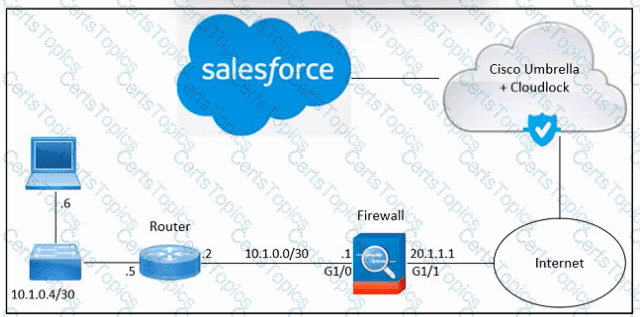
Refer to the exhibit. An engineer must integrate Cisco Cloudlock with Salesforce in an organization. Despite the engineer's successful execution of the Salesforce integration with Cloudlock, the administrator still lacks the necessary visibility. What should be done to meet the requirement?
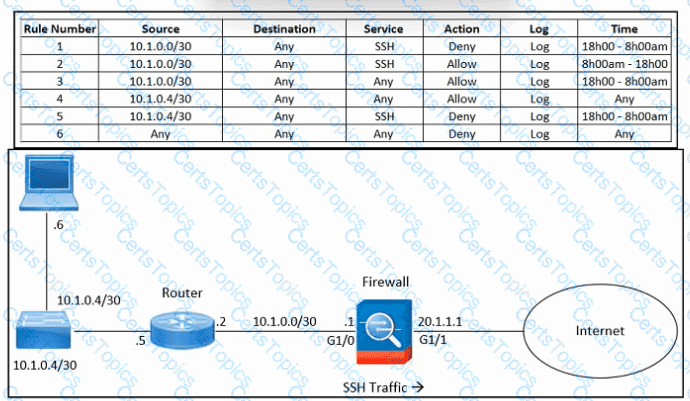
Refer to the exhibit. An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists. What should be done to meet the requirement?
Which web application firewall deployment in the Cisco Secure DDoS protects against application layer and volumetric attacks?
Which mitigation technique does a web application firewall use to protect a web server against DDoS attacks?
A network administrator uses Cisco Umbrella to protect internal users from malicious content. A customer is using an IPsec tunnel to connect to an Umbrella Organization. The administrator was informed about a zero-day vulnerability that infects user machines and uploads sensitive data through the RDP port. The administrator must ensure that no users are connected to the internet using the RDP protocol. Which Umbrella configuration must the administrator apply?
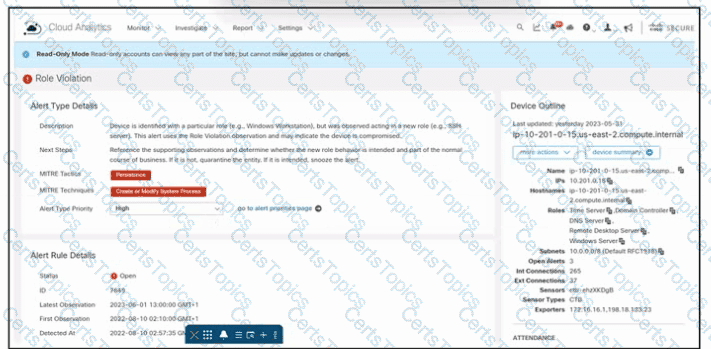

Refer to the exhibit. An engineer is troubleshooting an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?

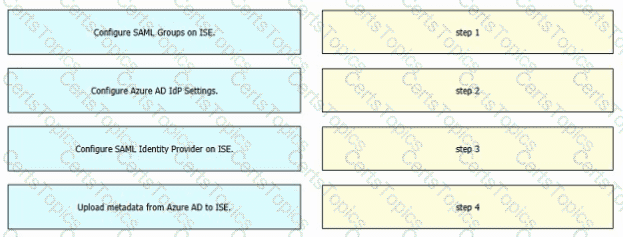
Refer to the exhibit. An engineer must configure SAML single sign-on in Cisco ISE to use Microsoft Azure AD as an identity provider. Drag and drop the steps from the left into the sequence on the right to configure Cisco ISE with SAML single sign-on.
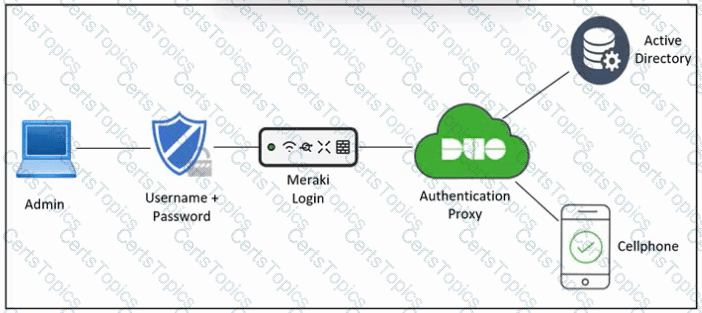
An engineer is configuring multifactor authentication using Duo. The implementation must use Duo Authentication Proxy and the Active Directory as an identity source. The company uses Azure and a local Active Directory. Which configuration is needed to meet the requirement?
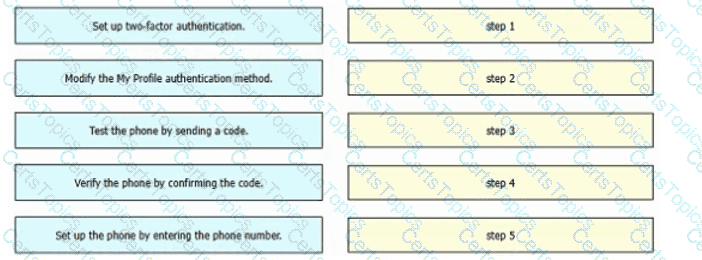
Refer to the exhibit. An engineer must configure multifactor authentication using the Duo Mobile app to provide admin access to a Cisco Meraki switch. The engineer already configured Duo Mobile and received an activation code. Drag and drop the steps from left to right to complete the configuration.
What must be automated to enhance the efficiency of a security team response?
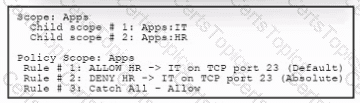
Refer to the exhibit. An engineer must analyze a segmentation policy in Cisco Secure Workload. What is the result of applying the policy?