Citrix Related Exams
1Y0-440 Exam







Scenario: Based on a discussion between a Citrix Architect and team of Workspacelab has been created across three (3) sites.
They captured the following requirements during the design discussion held for NetScaler design projects:
Which design decision must the architect make to meet the design requirements above?
Under which two circumstances will a service be taken out of the slow start phase with automated slow start? (Choose Two)
Scenario: A Citrix Architect needs to design a new multi-datacenter NetScaler deployment. The customer wants NetScaler to provide access to various backend resources by using Global Server Load Balancing (GSLB) in an Active-Active deployment.
Click the Exhibit button to view additional requirements identified by the architect.
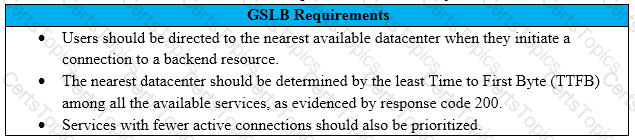
Which GSLB algorithm or method should the architect use for the deployment, based on the stated requirements?