Exhibit
Referring to the exhibit, which statement is correct?
You are a network architect for a service provider and want to offer Layer 2 services to your customers You want to use EVPN for Layer 2 services in your existing MPLS network.
Which two statements are correct in this scenario? (Choose two.)
Exhibit
A network designer would like to create a summary route as shown in the exhibit, but the configuration is not working.
Which three configuration changes will create a summary route? (Choose three.)
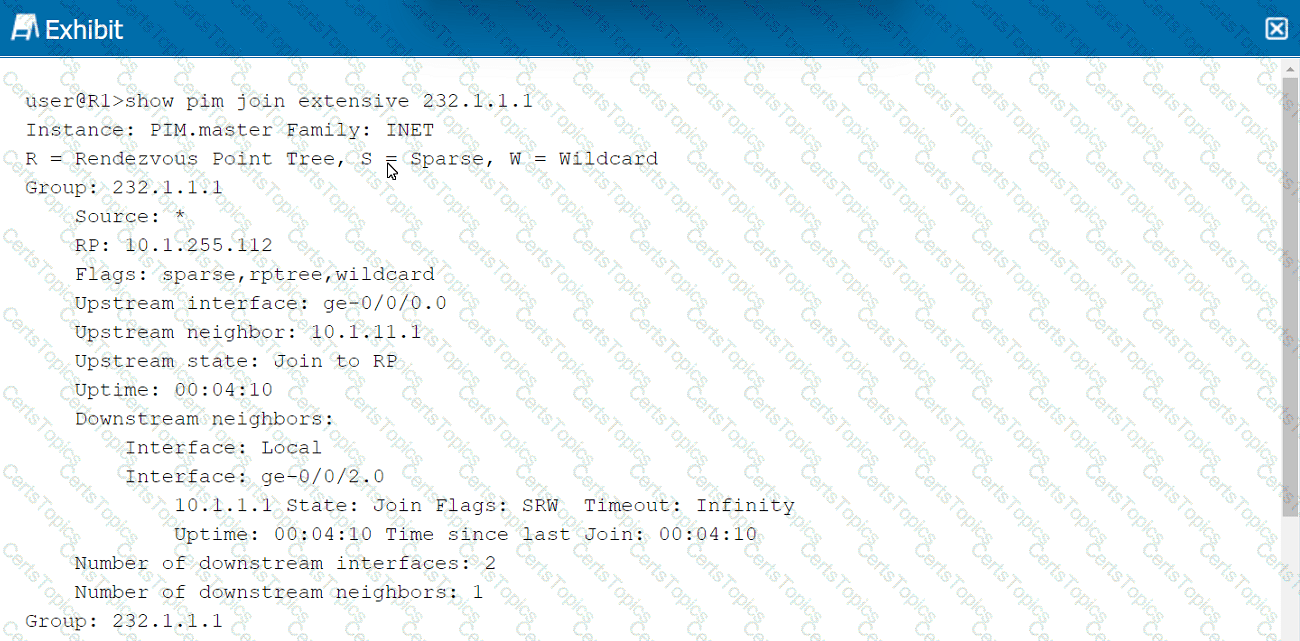
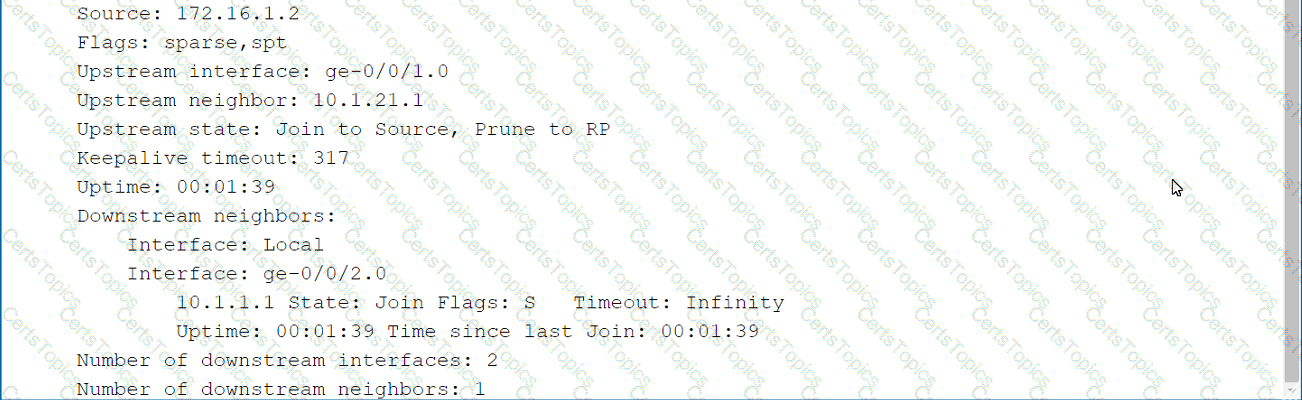
Click the Exhibit button.
Referring to the exhibit, which two statements are correct regarding the output shown in the exhibit? (Choose two.)
When using OSPFv3 for an IPv4 environment, which statement is correct?
When building an interprovider VPN, you notice on the PE router that you have hidden routes which are received from your BGP peer with family inet labeled-unica3t configured.
Which parameter must you configure to solve this problem?
Which two EVPN route types are used to advertise a multihomed Ethernet segment? (Choose two )
Exhibit
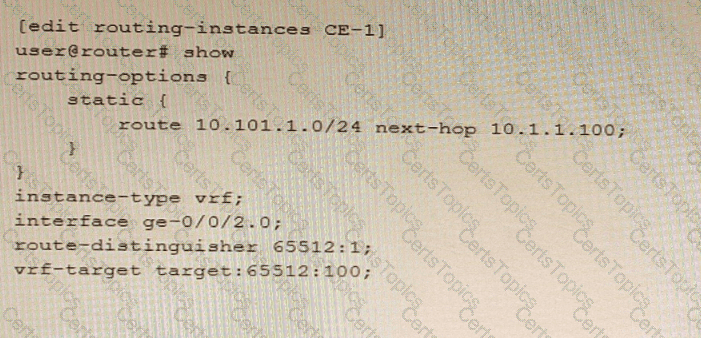
Referring to the exhibit, which statement is true?
Click the Exhibit button.
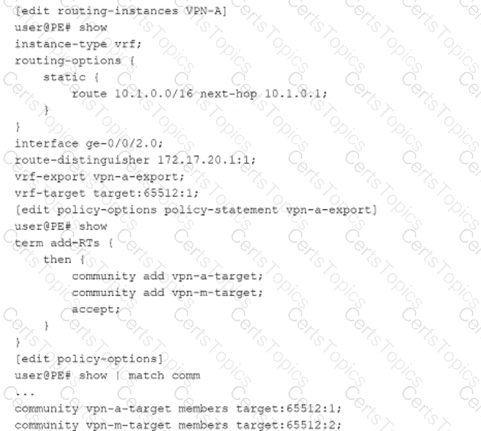
Referring to the exhibit, which statement is correct?
Exhibit
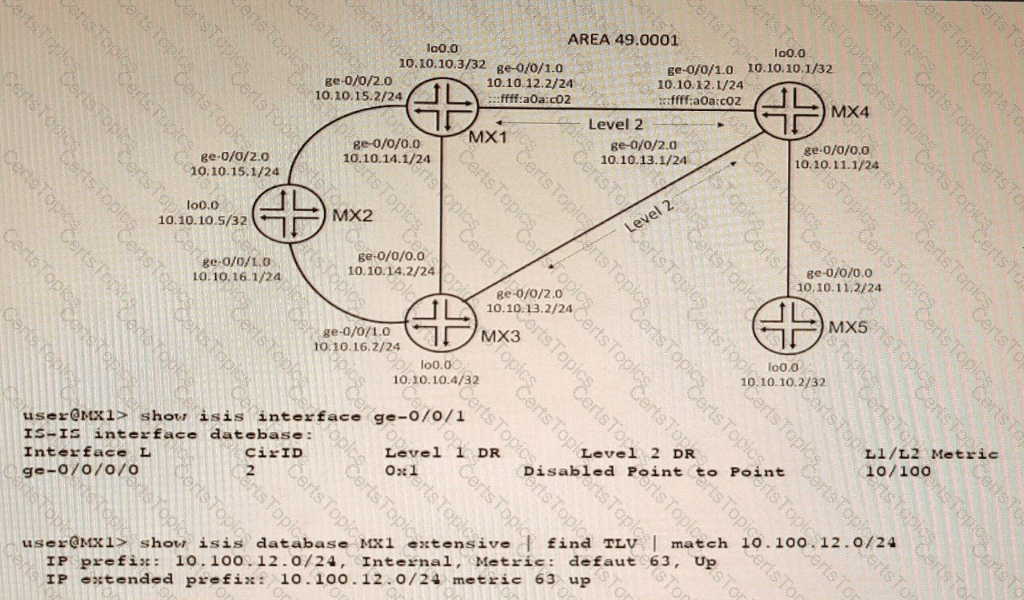
A network is using IS-IS for routing.
In this scenario, why are there two TLVs shown in the exhibit?
Exhibit
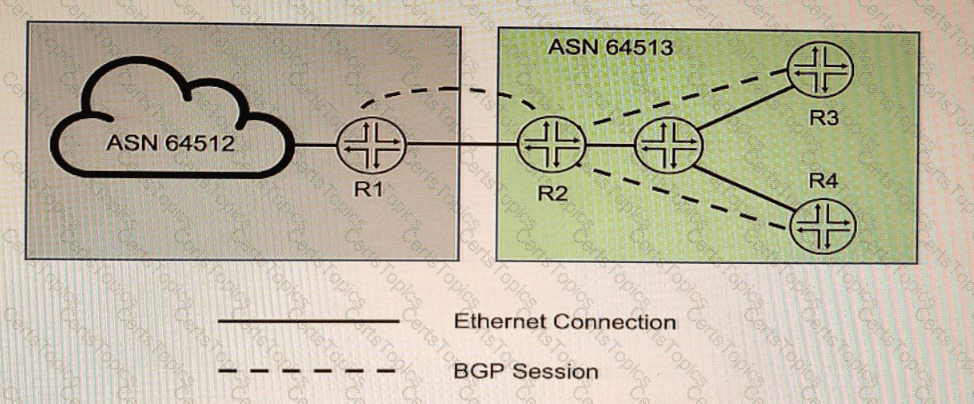
You want to implement the BGP Generalized TTL Security Mechanism (GTSM) on the network
Which three statements are correct in this scenario? (Choose three)
You are responding to an RFP for a new MPLS VPN implementation. The solution must use LDP for signaling and support Layer 2 connectivity without using BGP The solution must be scalable and support multiple VPN connections over a single MPLS LSP The customer wants to maintain all routing for their Private network
In this scenario, which solution do you propose?
Exhibit.
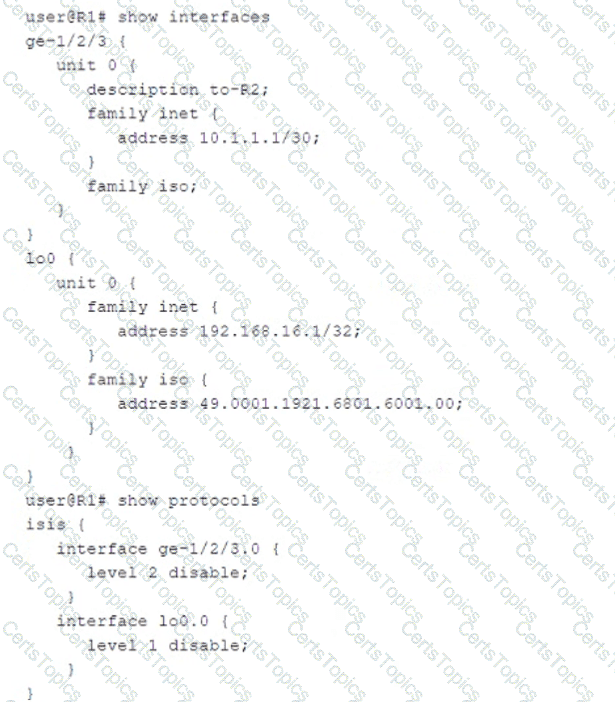

Referring to the exhibit, what must be changed to establish a Level 1 adjacency between routers R1 and R2?
Click the Exhibit hutton.
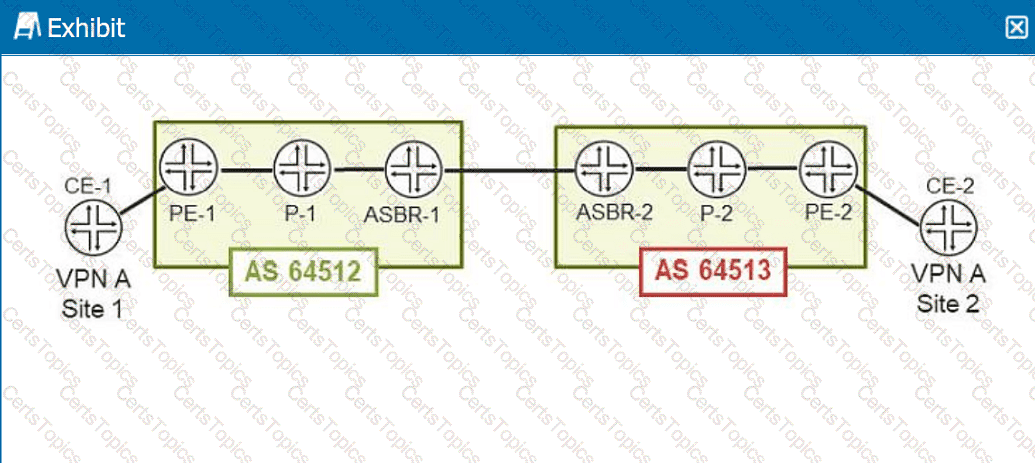
You are configuring an interprovider Option C Layer 3 VPN to connect two customer sites.
Referring to the exhibit, which three statements are correct? (Choose three.)
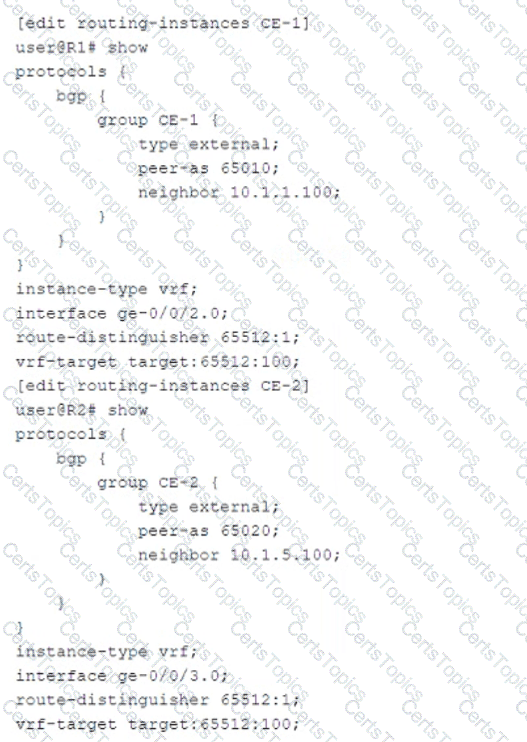
Exhibit
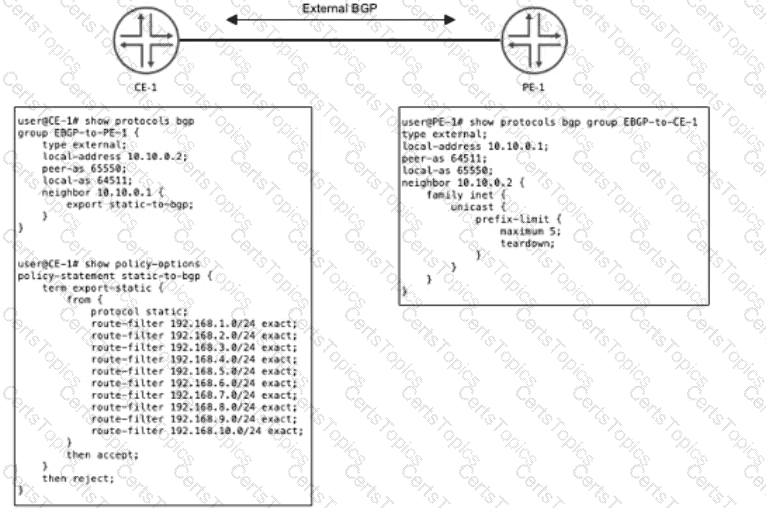
CE-1 must advertise ten subnets to PE-1 using BGP Once CE-1 starts advertising the subnets to PE-1, the BGP peering state changes to Active.
Referring to the CLI output shown in the exhibit, which statement is correct?
Which two statements are correct about a sham link? (Choose two.)
You want to ensure that L1 IS-IS routers have only the most specific routes available from L2 IS-IS routers. Which action accomplishes this task?
Exhibit
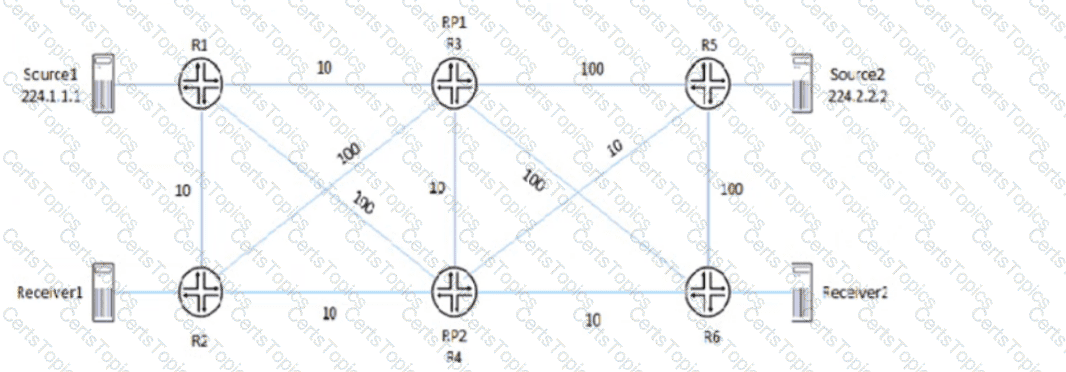
Referring to the exhibit, PIM-SM is configured on all routers, and Anycast-RP with Anycast-PIM is used for the discovery mechanism on RP1 and RP2. The interface metric values are shown for the OSPF area.
In this scenario, which two statements are correct about which RP is used? (Choose two.)
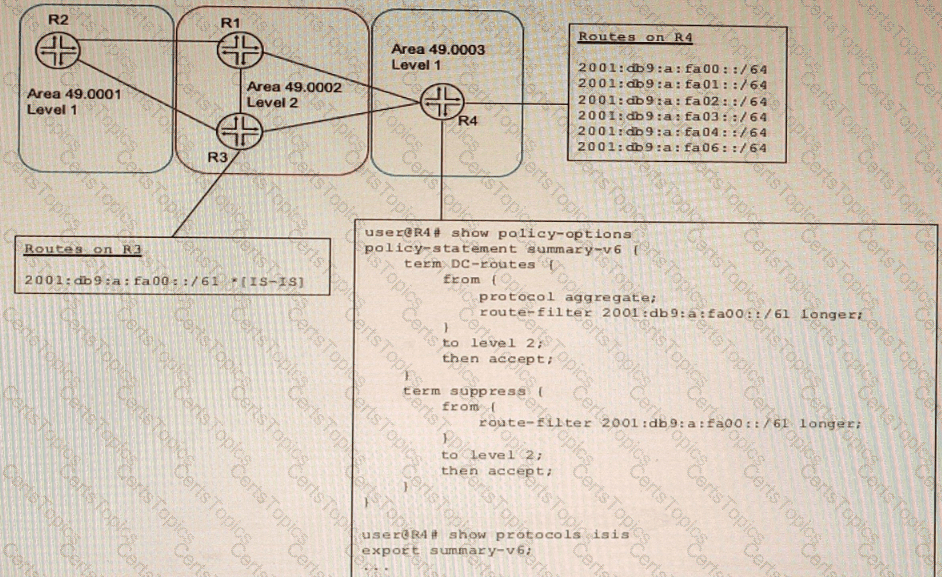
Refer to the Exhibit:
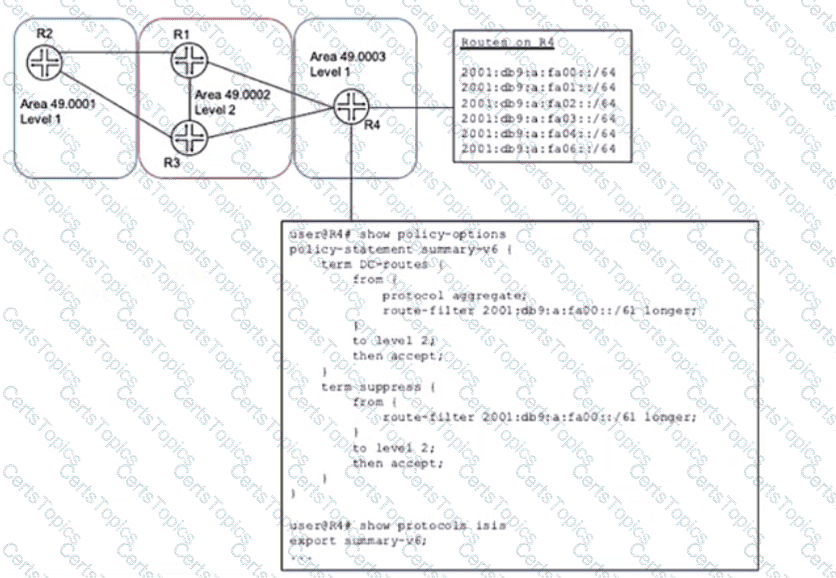
A network designer would like to advertise a single summary route from R4 to IS-IS level 2 neighbors as shown in the exhibit, but the configuration is not working.
Which three configuration changes will accomplish this task? (Choose three.)
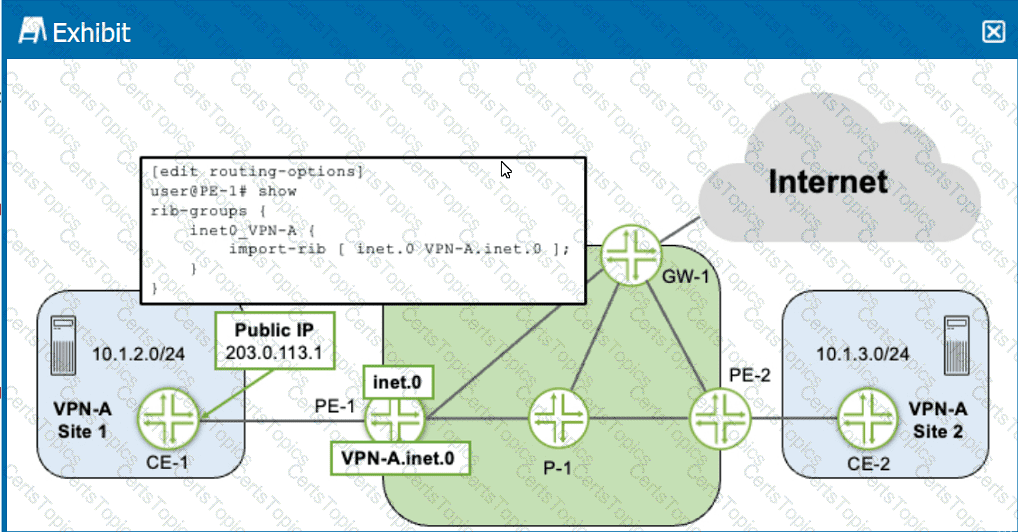
Click the Exhibit button.
Referring to the exhibit, you must provide VRF Internet access over a single connection for VPN-A Site 1, which connects to PE-1.
Which two statements are correct in this scenario? (Choose two.)
Exhibit
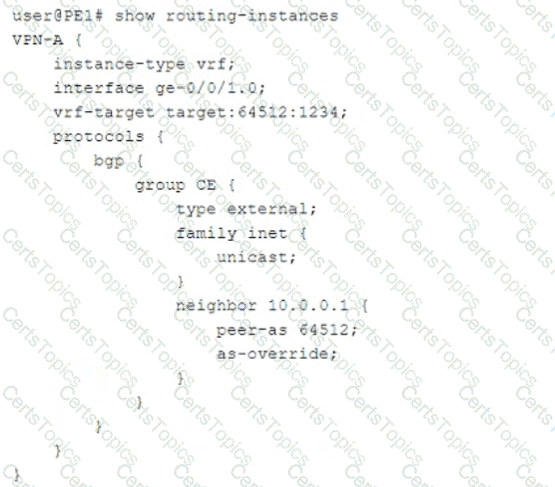
Which two statements about the configuration shown in the exhibit are correct? (Choose two.)
In IS-IS, which two statements are correct about the designated intermediate system (DIS) on a multi-access network segment? (Choose two)
You want to ensure that a single-area OSPF network will be loop free.
In this scenario, what are two requirements that satisfy this requirement? (Choose two.)
Exhibit

CE-1 and CE-2 are part of a VPLS called Customer1 No connectivity exists between CE-1 and CE-2. In the process of troubleshooting, you notice PE-1 is not learning any routes for this VPLS from PE-2, and PE-2 is not learning any routes for this VPLS from PE-1.
Which two statements are correct about the customer interface in an LDP-signaled pseudowire? (Choose two)
Your organization manages a Layer 3 VPN for multiple customers To support advanced route than one BGP community on advertised VPN routes to remote PE routers.
Which routing-instance configuration parameter would support this requirement?
Which two statements are correct regarding the PIM DR in a PIM-SM domain? (Choose two.)