Which two statements are correct about a sham link? (Choose two.)
You want to ensure that L1 IS-IS routers have only the most specific routes available from L2 IS-IS routers. Which action accomplishes this task?
Exhibit
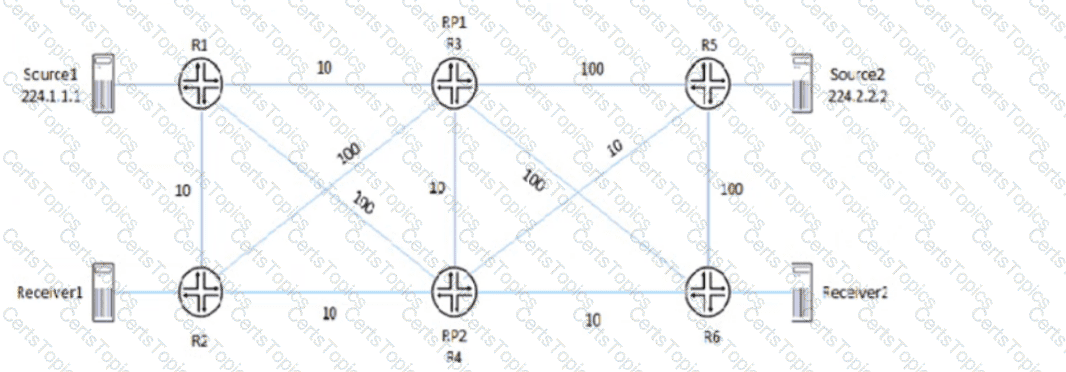
Referring to the exhibit, PIM-SM is configured on all routers, and Anycast-RP with Anycast-PIM is used for the discovery mechanism on RP1 and RP2. The interface metric values are shown for the OSPF area.
In this scenario, which two statements are correct about which RP is used? (Choose two.)
Refer to the Exhibit:
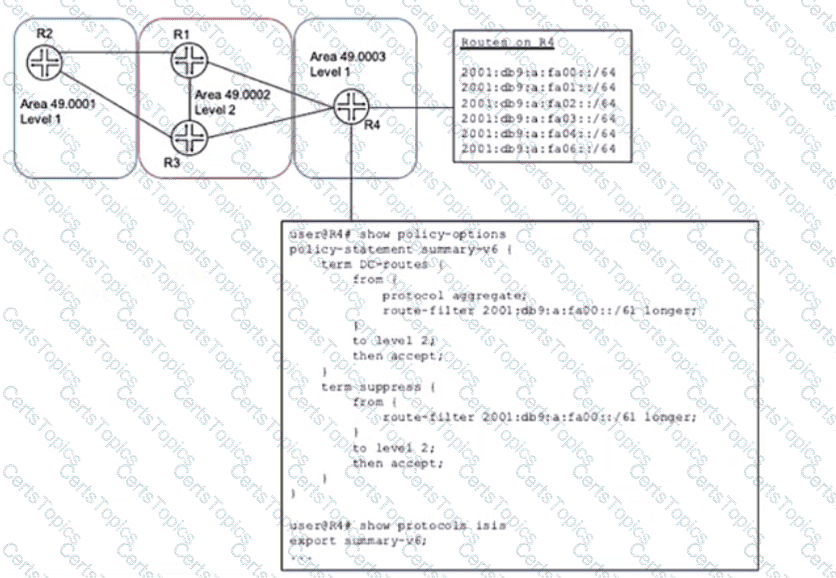
A network designer would like to advertise a single summary route from R4 to IS-IS level 2 neighbors as shown in the exhibit, but the configuration is not working.
Which three configuration changes will accomplish this task? (Choose three.)