Which of the following statements is false about centralized storage and distributed storage?
Generally, a subnet mask is used together with an IP address. The 0s in the binary value represent the network portion of an IP address, and the 1s represent the host portion.
Which of the following statements is false about concepts of virtualization?
Which of the following statements aretrueabout deploying Compute Node Agent (CNA) and Virtual Resource Management (VRM) in Huawei FusionCompute?
In FusionCompute, the user can set the priority for each member port in a port group.
Desktop users on the same FusionAccess can be authenticated using different domains.
Which of the following statements isfalseabout High Availability (HA) in Huawei FusionCompute?
Which of the following statements is false about virtualized storage?
The application scenarios of FusionAccess include secure offices, public terminals, general offices, and GPU graphics. Which of the following desktop types ismost suitable for new media operations?
When an administrator uses alinked clone templateto quickly provision virtual machines (VMs) on FusionAccess, which of the following are thesteps of the quick provision process?
During FusionAccess virtual desktop provisioning, which of the following components receives the registration request sent by the desktop VM?
In virtualization, KVM and Xen are typical hardware-assisted virtualization technologies. They implement virtualization based on kernel modules in the operating system.
In FusionCompute, the security auditor in role-based access control (RBAC) mode is only permitted to view and export logs.
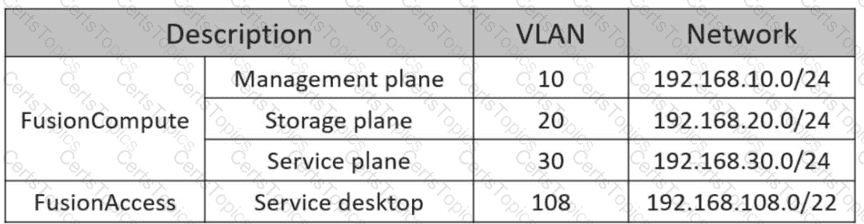
The following table lists the FusionAccess environment plan. Which of the following network segments is the most suitable for deploying FusionAccess Linux infrastructure VMs?
Which of the following statements are true about system encapsulation and Sysprep (system encapsulation tool) for creating a full copy template on FusionAccess?
The Central Processing Unit (CPU) is the computer's computing and control core. Mainly composed of an arithmetic logic unit (ALU) and a controller, it reads and executes data according to instructions.
Which of the following statements isfalseabout virtualization concepts?
Two virtual machines run on the same host and are in the same network segment, but they cannot communicate with each other. Which of the following isnota possible cause?
Which of the following statements istrueabout the FusionCompute storage architecture?
Which of the following statements isfalseabout host requirements during FusionCompute installation?
At which layer of the TCP/IP reference model does a router work?
A bare VM is required when creating a virtual desktop template on FusionAccess. Which of the following statements aretrueabout creating a bare VM?
Which of the following operations must be performed on FusionAccess when you create a Windows template?
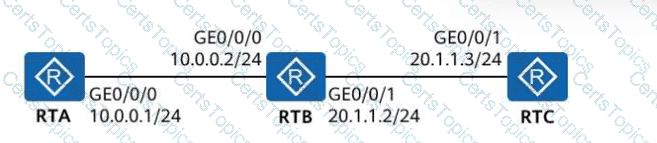
Which of the following statements arefalseabout the network shown in the figure?
A router manages path information by managing its___
Enterprise administrators provision virtual desktops and perform routine maintenance through virtual desktop service management. Which of the following are the provisioning proportion modes of preset virtual desktops in desktop provisioning management?
On FusionAccess software deployment, if multiple FusionAccess systems share a License, the License component should be deployed independently.
TAP is a virtual network device independently maintained in Linux.
When a VM template is created on FusionAccess, select“Configure user login”if the_____group members want to log in to the VM.
(Enter the correct word on the GUI)
The essence of ___ technology is to convert physical devices into logical ones, thereby decoupling software from hardware.
Which of the following statements are true about high-fidelity audio and video based on Huawei Desktop Protocol (HDP)?
TAP is a virtual network device independently maintained in Linux.1
Which of the following commands are used to view common files on Linux?
Complete the following configuration file for a network interface card (NIC) in theopenEuleroperating system to set astatic IP addressand enable the NIC toautomatically start upon system boot.
TYPE=Ethernet
BOOTPROTO=_____
NAME=enp0s4
DEVICE=enp0s4
ONBOOT=_____
IPADDR=172.28.100.100
NETMASK=255.255.255.0