In FusionCompute, the security auditor in role-based access control (RBAC) mode is only permitted to view and export logs.
The following table lists the FusionAccess environment plan. Which of the following network segments is the most suitable for deploying FusionAccess Linux infrastructure VMs?
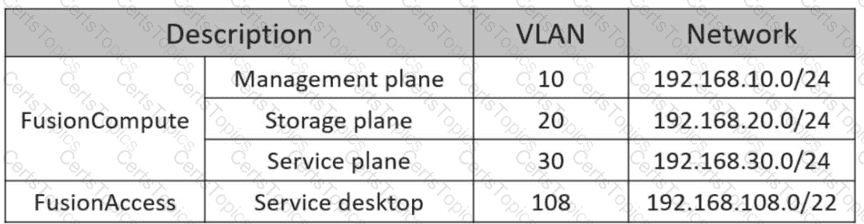
Which of the following statements are true about system encapsulation and Sysprep (system encapsulation tool) for creating a full copy template on FusionAccess?
The Central Processing Unit (CPU) is the computer's computing and control core. Mainly composed of an arithmetic logic unit (ALU) and a controller, it reads and executes data according to instructions.