Refer to the exhibits, which show a network topology and VPN configuration.
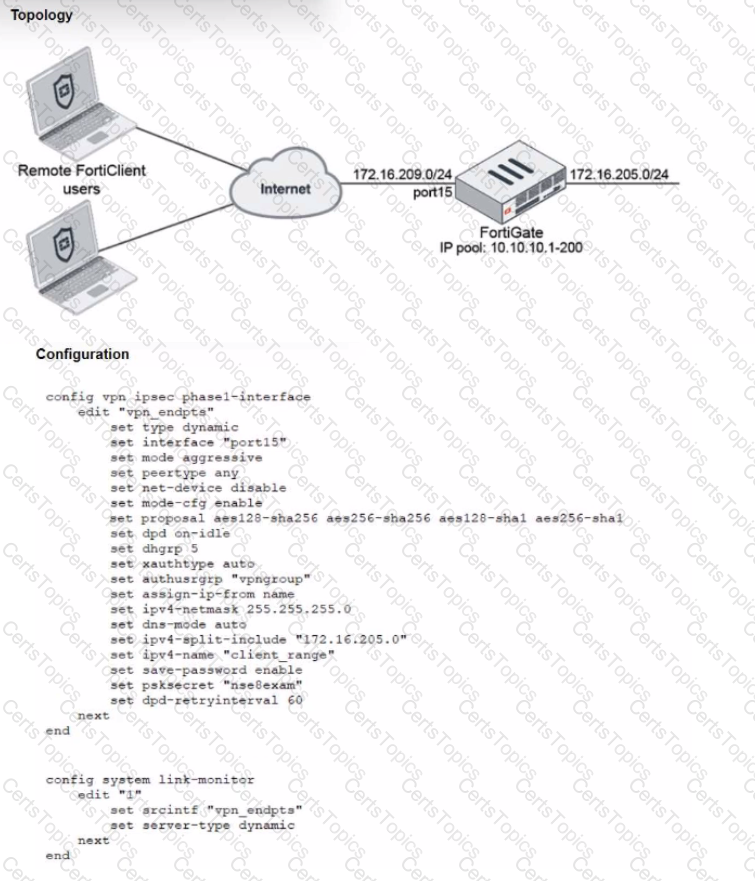
A network administrator has been tasked with modifying the existing dial-up IPsec VPN infrastructure to detect the path quality to the remote endpoints.
After applying the configuration shown in the configuration exhibit, the VPN clients can still connect and access the protected 172.16.205.0/24 network, but no SLA information shows up for the client tunnels when issuing the diagnose sys link-monitor tunnel all command on the FortiGate CLI.
What is wrong with the configuration?
Refer to the exhibits.
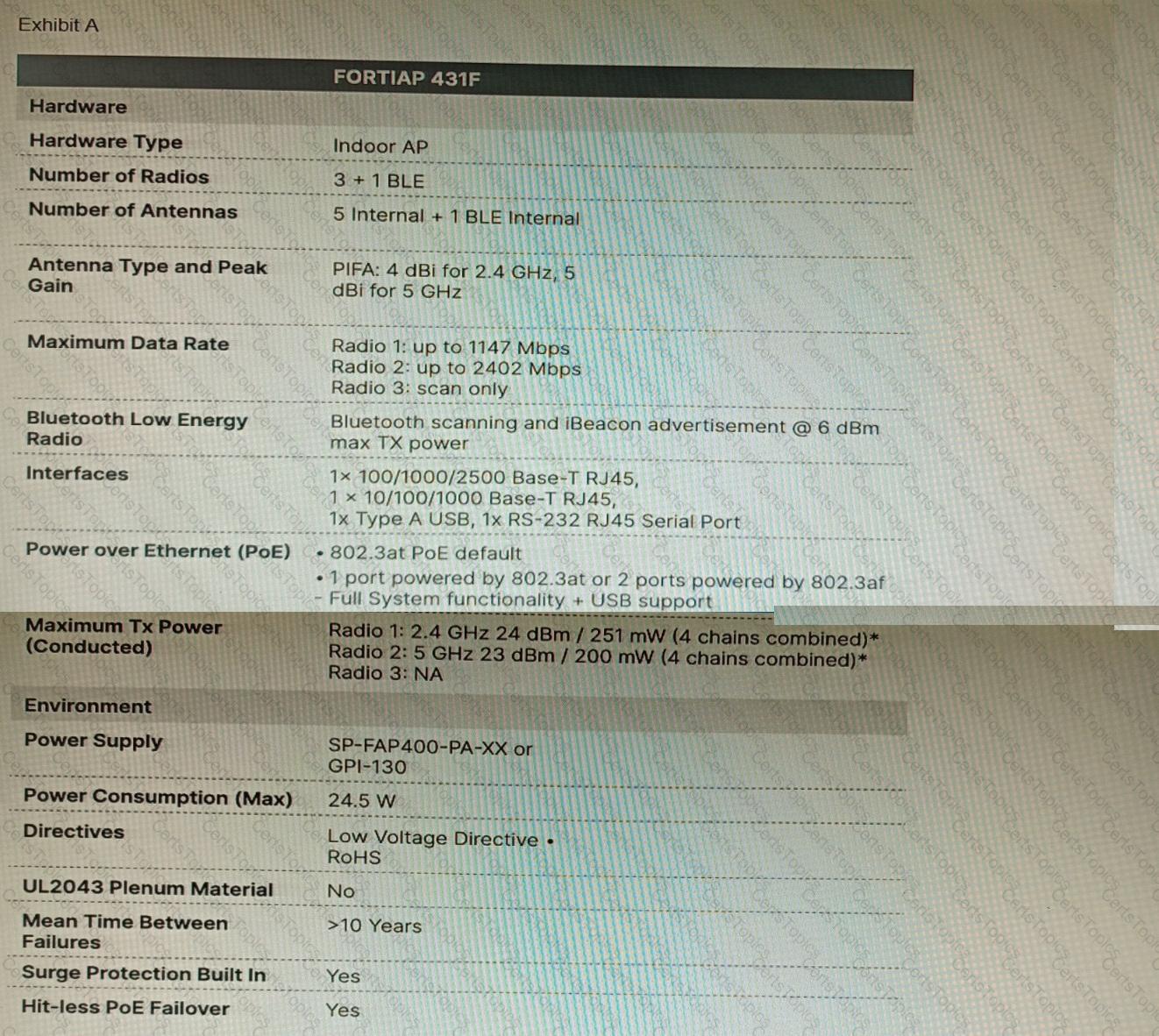
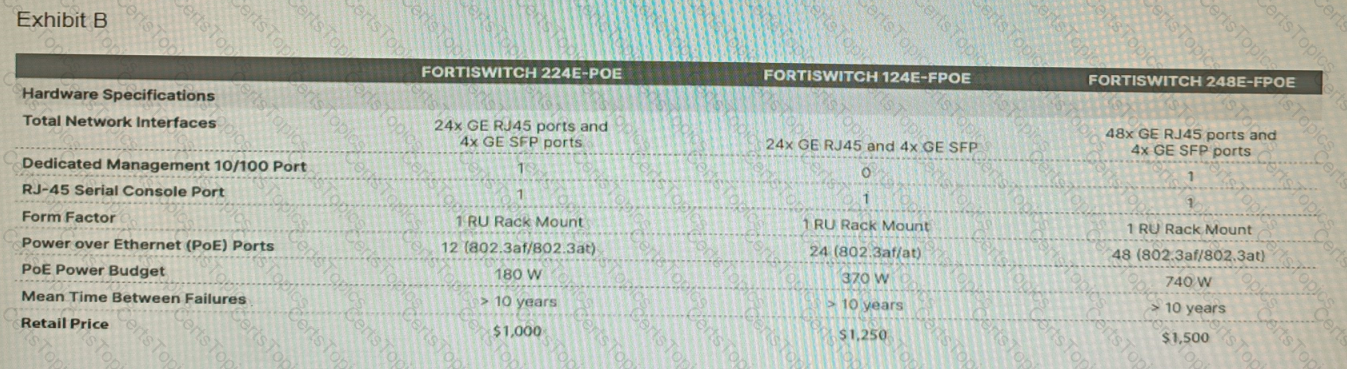
A customer wants to deploy 12 FortiAP 431F devices on high density conference center, but they do not currently have any PoE switches to connect them to. They want to be able to run them at full power while having network redundancy
From the FortiSwitch models and sample retail prices shown in the exhibit, which build of materials would have the lowest cost, while fulfilling the customer's requirements?
Refer to the exhibit showing a FortiView monitor screen.
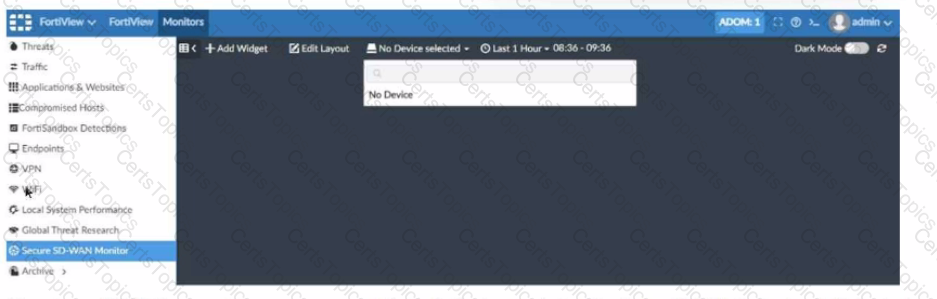
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection.
What can cause this issue?
Refer to the exhibit, which shows an SD-WAN configuration.
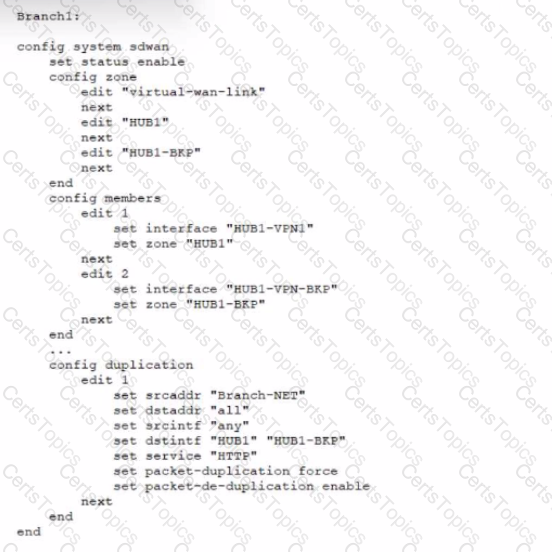
You configured the SD-WAN from Branch1 to the HUB and enabled packet duplication. You later notice that the traffic is not being duplicated. In this scenario, what is causing this problem?
Refer to the exhibit.
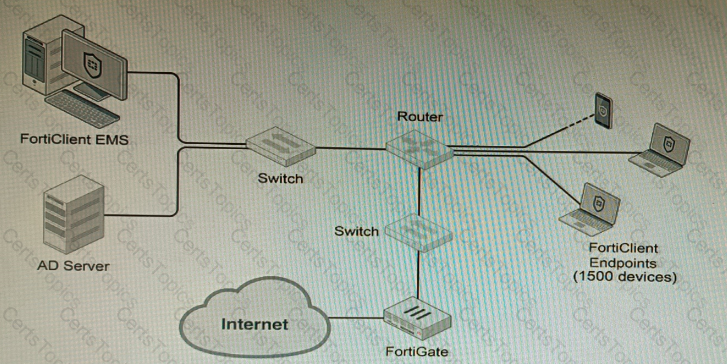
A customer wants FortiClient EMS configured to deploy to 1500 endpoints. The deployment will be integrated with FortiOS and there is an Active Directory server.
Given the configuration shown in the exhibit, which two statements about the installation are correct? (Choose two.)
Refer to the CLI configuration of an SSL inspection profile from a FortiGate device configured to protect a web server:
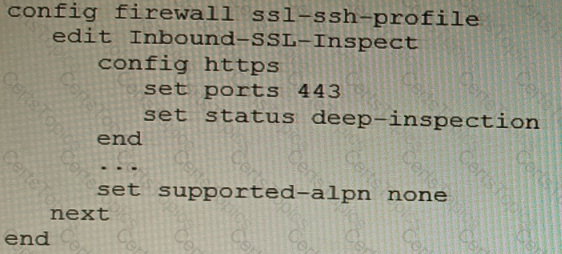
Based on the information shown, what is the expected behavior when an HTTP/2 request comes in?
Refer to the exhibit.
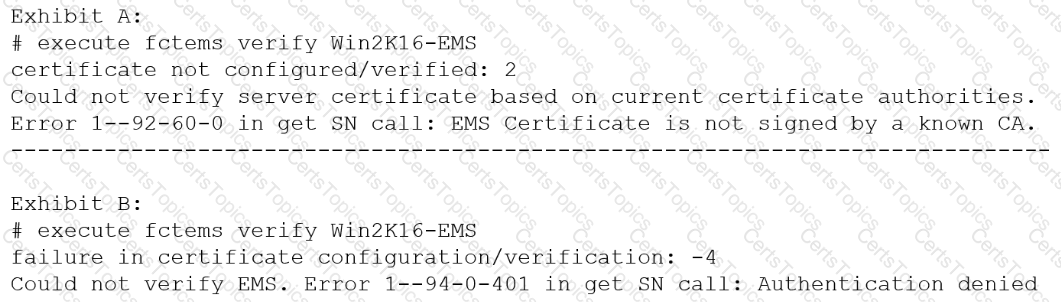
The exhibit shows two error messages from a FortiGate root Security Fabric device when you try to configure a new connection to a FortiClient EMS Server.
Referring to the exhibit, which two actions will fix these errors? (Choose two.)
Refer to the exhibits, which show a firewall policy configuration and a network topology.
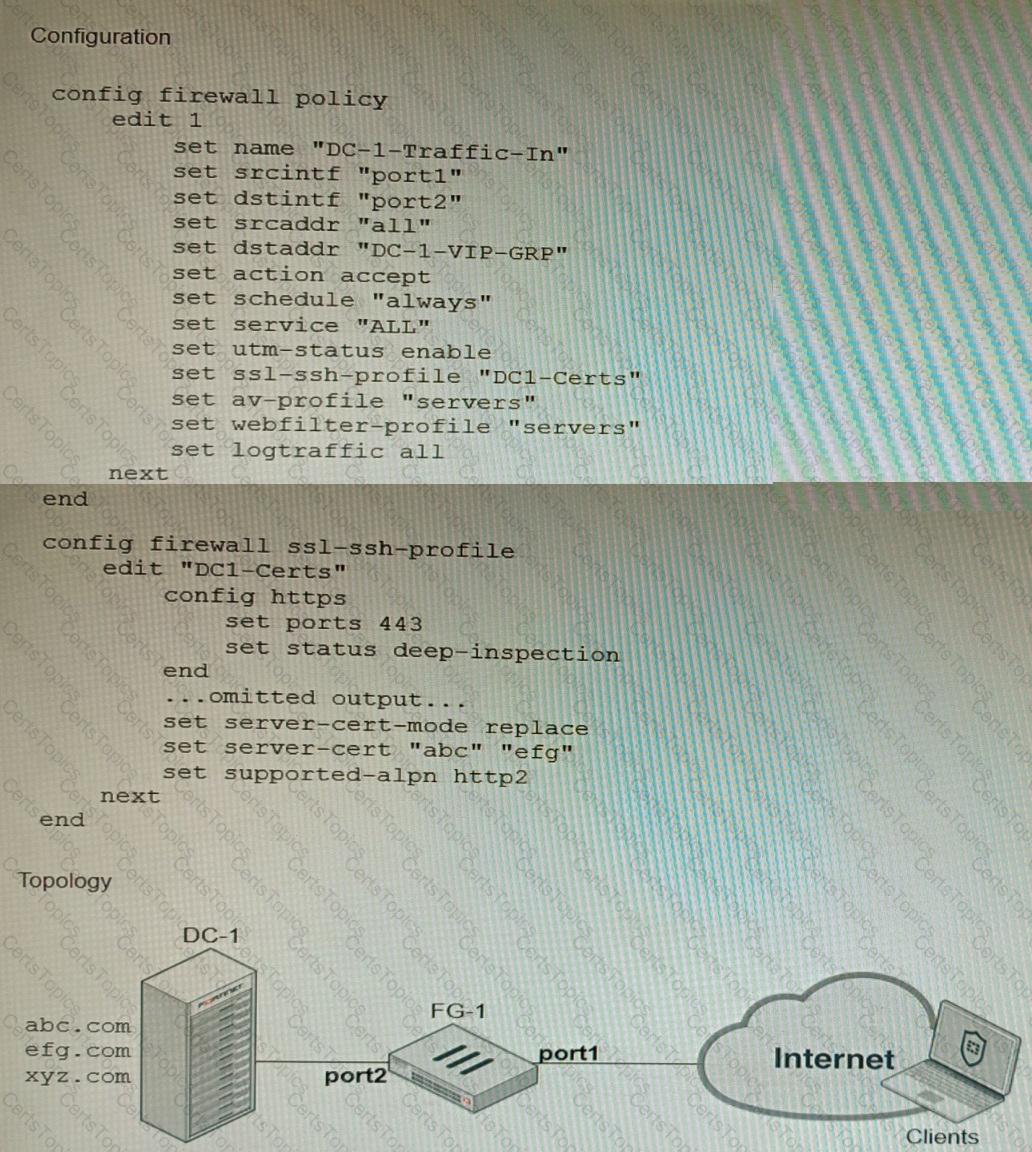
An administrator has configured an inbound SSL inspection profile on a FortiGate device (FG-1) that is protecting a data center hosting multiple web pages-Given the scenario shown in the exhibits, which certificate will FortiGate use to handle requests to xyz.com?
A customer's cybersecurity department needs to implement security for the traffic between two VPCs in AWS, but these belong to different departments within the company. The company uses a single region for all their VPCs.
Which two actions will achieve this requirement while keeping separate management of each department's VPC? (Choose two.)
You are performing a packet capture on a FortiGate 2600F with the hyperscale licensing installed. You need to display on screen all egress/ingress packets from the port16 interface that have been offloaded to the NP7.
Which three commands need to be run? (Choose three.)
Refer to the exhibits.
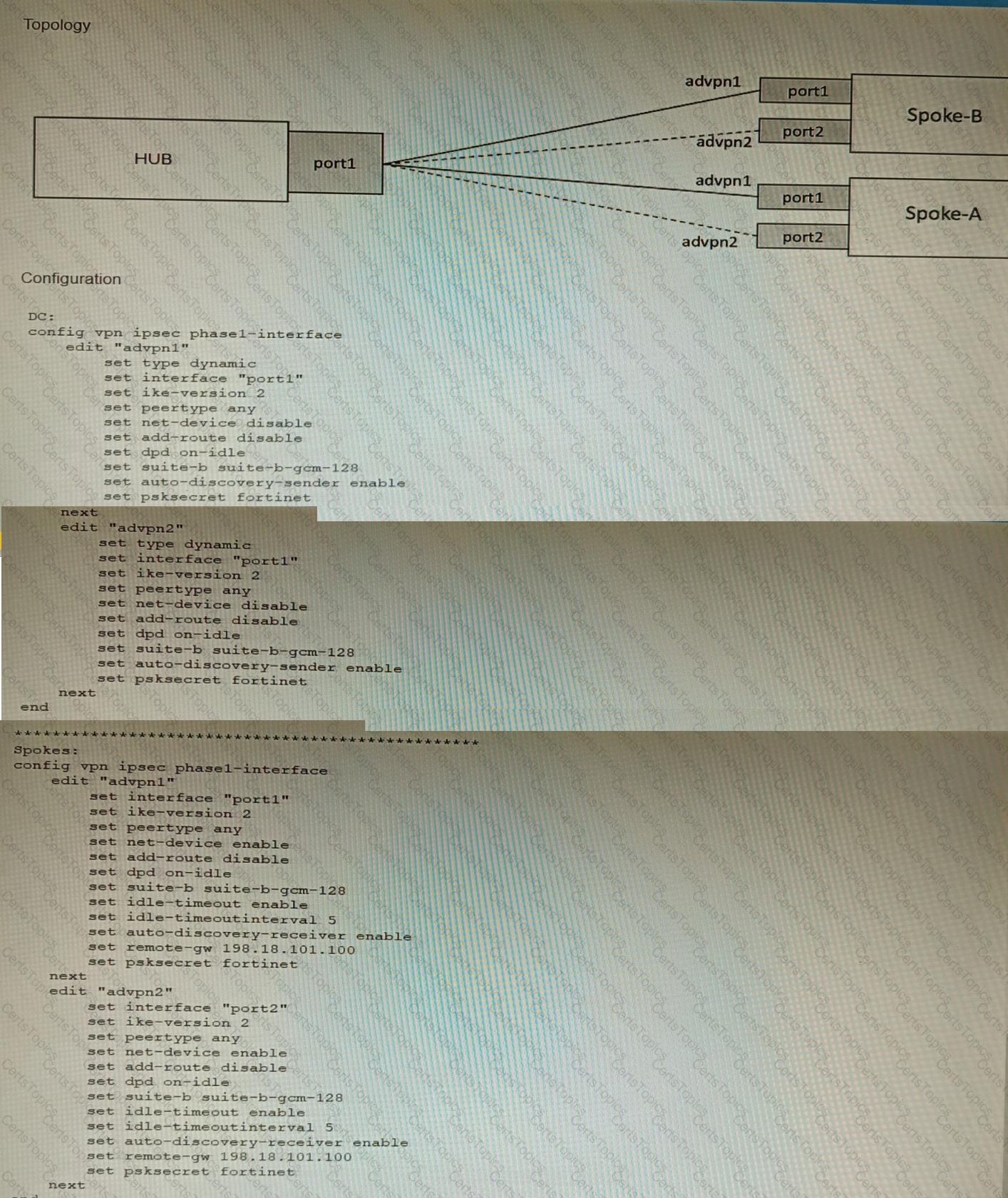
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
Refer to the exhibit showing the history logs from a FortiMail device.
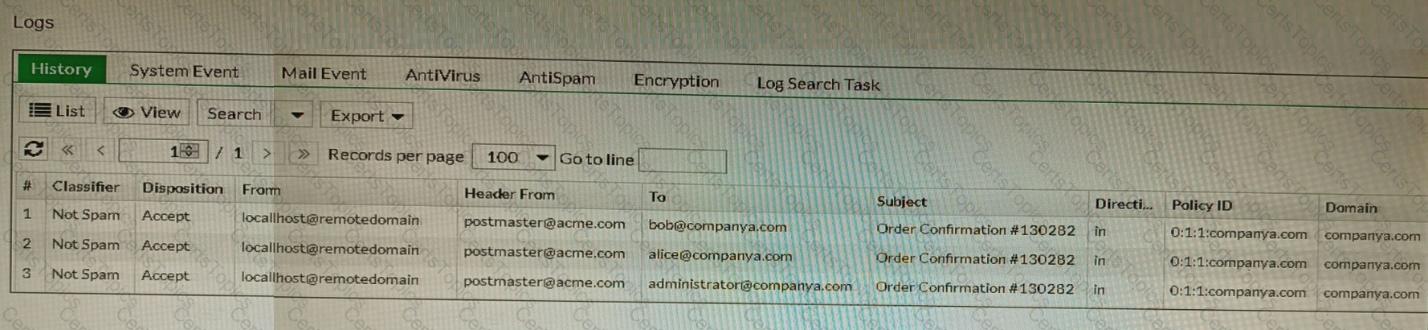
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
Refer to the exhibit, which shows a Branch1 configuration and routing table.
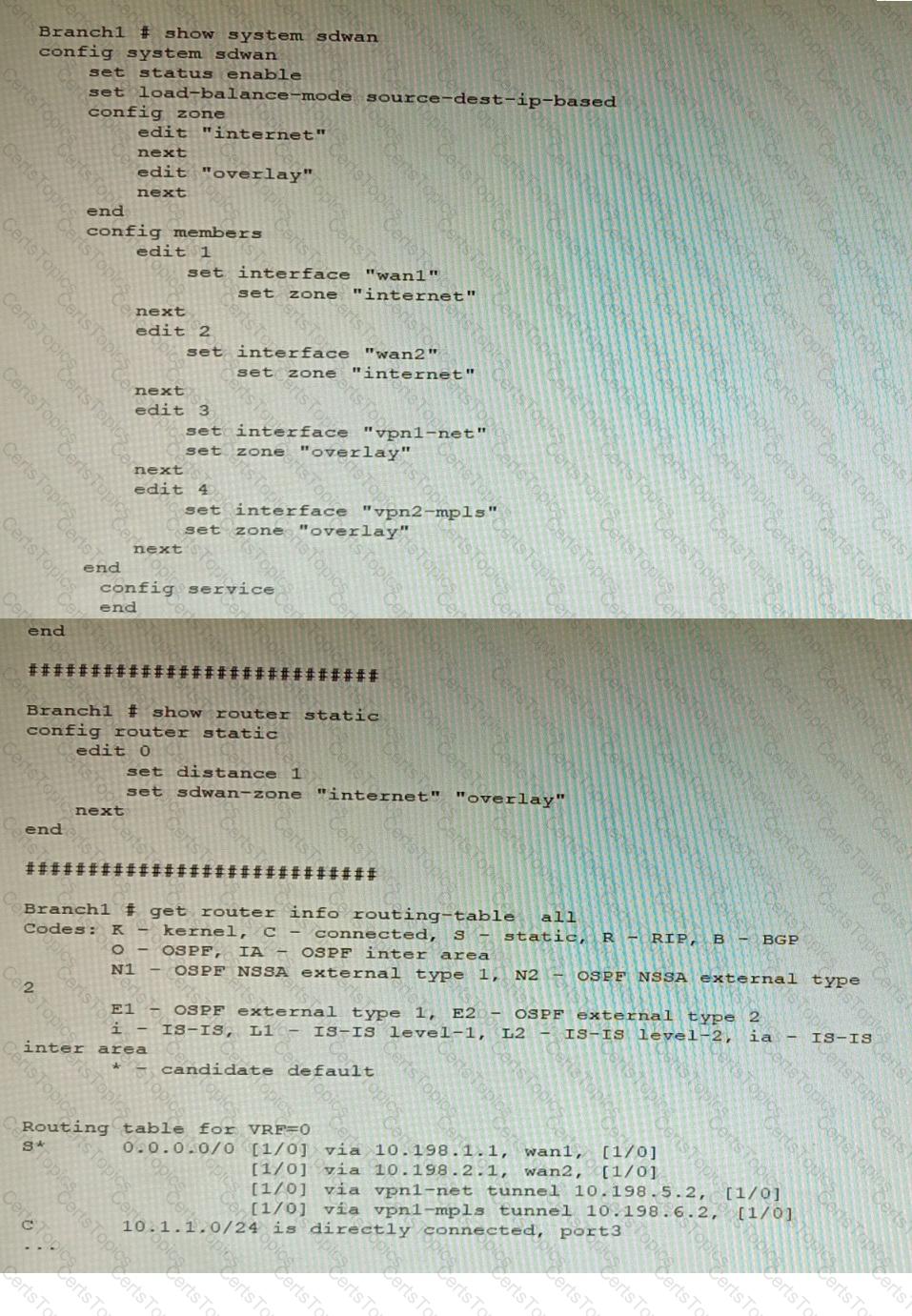
In the SD-WAN implicit rule, you do not want the traffic load balance for the overlay interface when all members are available.
In this scenario, which configuration change will meet this requirement?
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
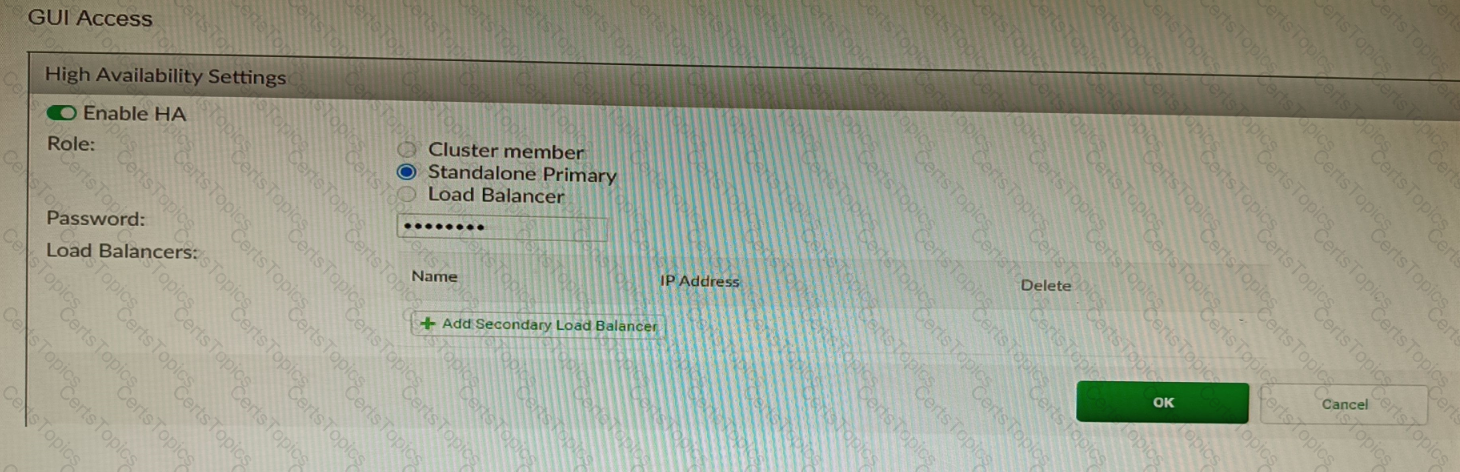
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
Refer to the exhibit.
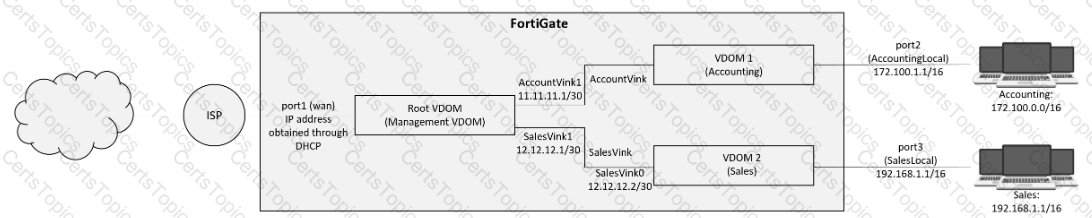
A customer has deployed a FortiGate 300E with virtual domains (VDOMs) enabled in the multi-VDOM mode. There are three VDOMs: Root is for management and internet access, while VDOM 1 and VDOM 2 are used for segregating internal traffic. AccountVInk and SalesVInk are standard VDOM links in Ethernet mode.
Given the exhibit, which two statements below about VDOM behavior are correct? (Choose two.)
Refer to the exhibits.
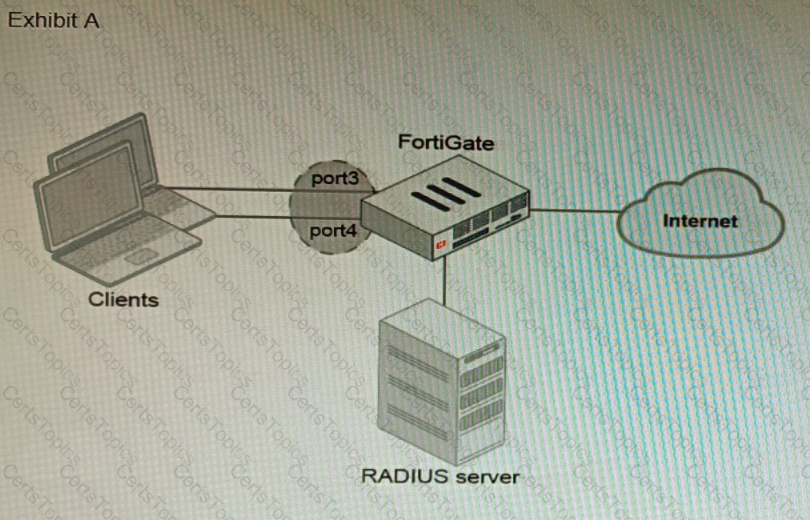
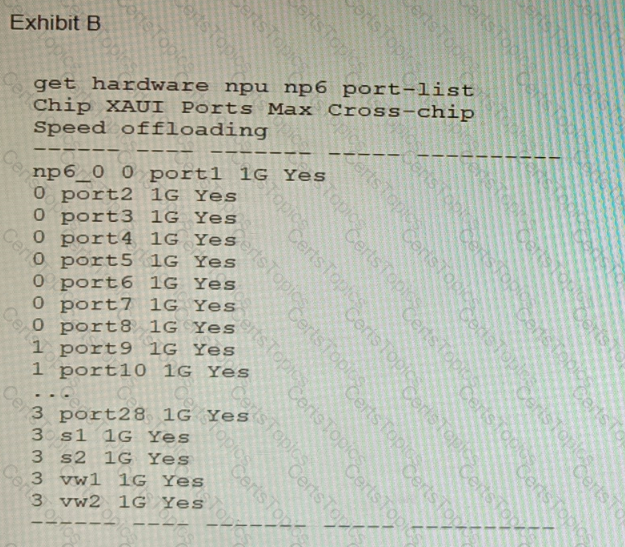
A customer is looking for a solution to authenticate the clients connected to a hardware switch interface of a FortiGate 400E.
Referring to the exhibits, which two conditions allow authentication to the client devices before assigning an IP address? (Choose two.)
A customer is planning on moving their secondary data center to a cloud-based laaS. They want to place all the Oracle-based systems Oracle Cloud, while the other systems will be on Microsoft Azure with ExpressRoute service to their main data center.
They have about 200 branches with two internet services as their only WAN connections. As a security consultant you are asked to design an architecture using Fortinet products with security, redundancy and performance as a priority.
Which two design options are true based on these requirements? (Choose two.)
Refer to the exhibit showing FortiGate configurations
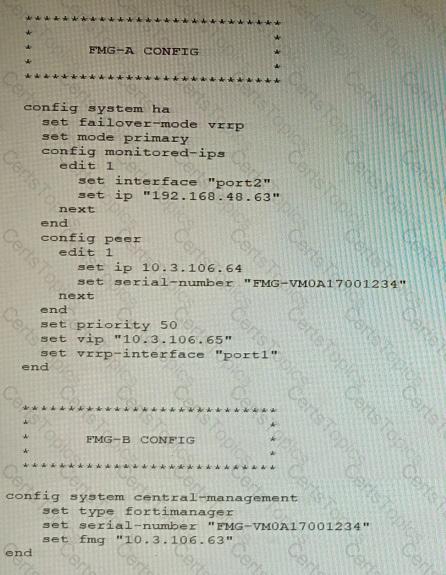
FortiManager VM high availability (HA) is not functioning as expected after being added to an existing deployment.
The administrator finds that VRRP HA mode is selected, but primary and secondary roles are greyed out in the GUI The managed devices never show online when FMG-B becomes primary, but they will show online whenever the FMG-A becomes primary.
What change will correct HA functionality in this scenario?
Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
Refer to The exhibit showing a FortiEDR configuration.
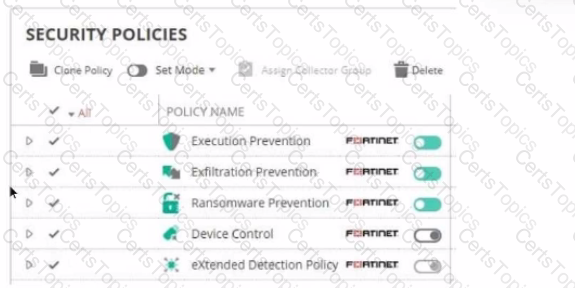
Based on the exhibit, which statement is correct?
Refer to the exhibits.

You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.

Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)
Refer to the exhibit.
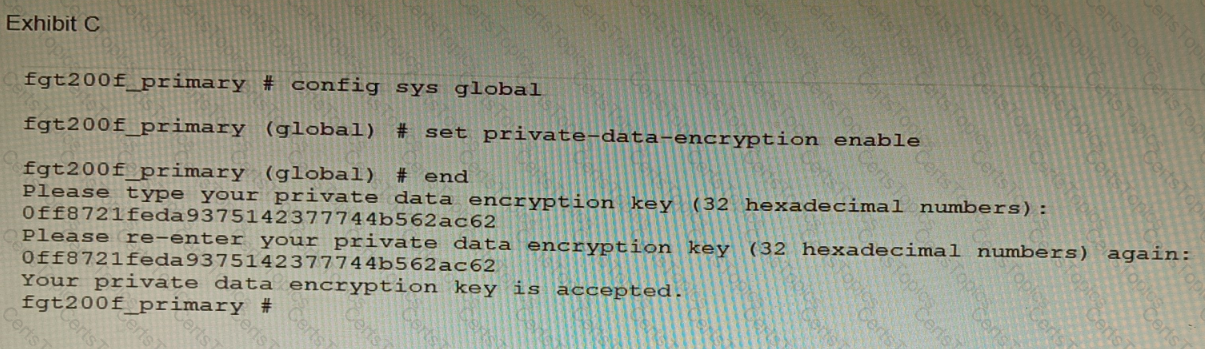
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
Refer to the exhibit containing the configuration snippets from the FortiGate. Customer requirements:
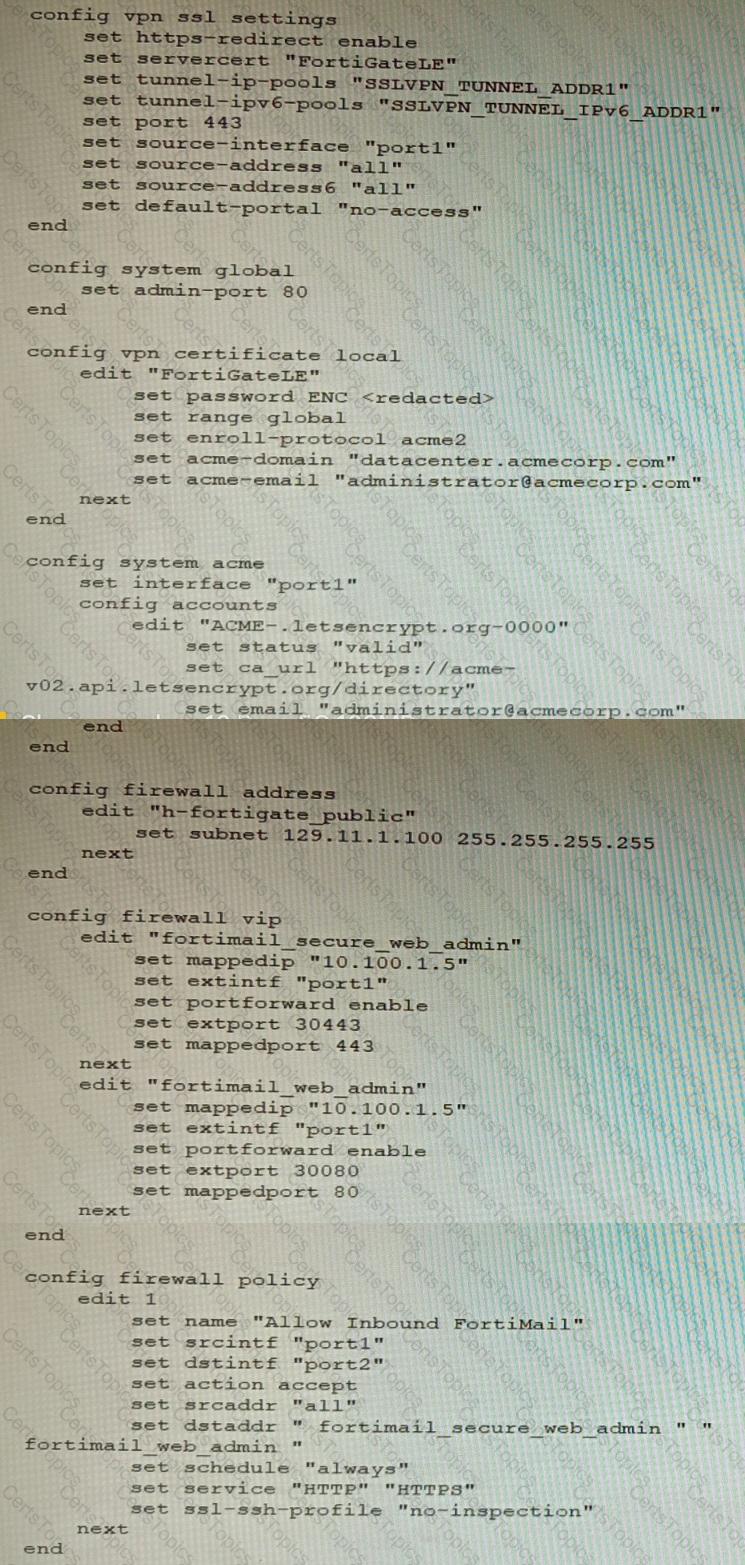
• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let's Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
A)
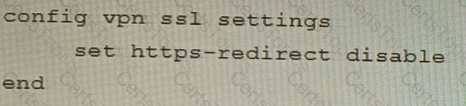
B)
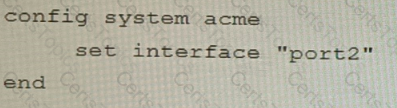
C)
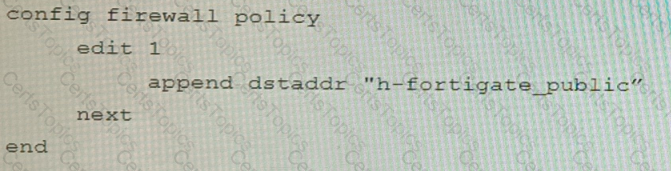
D)

Refer to the exhibit.
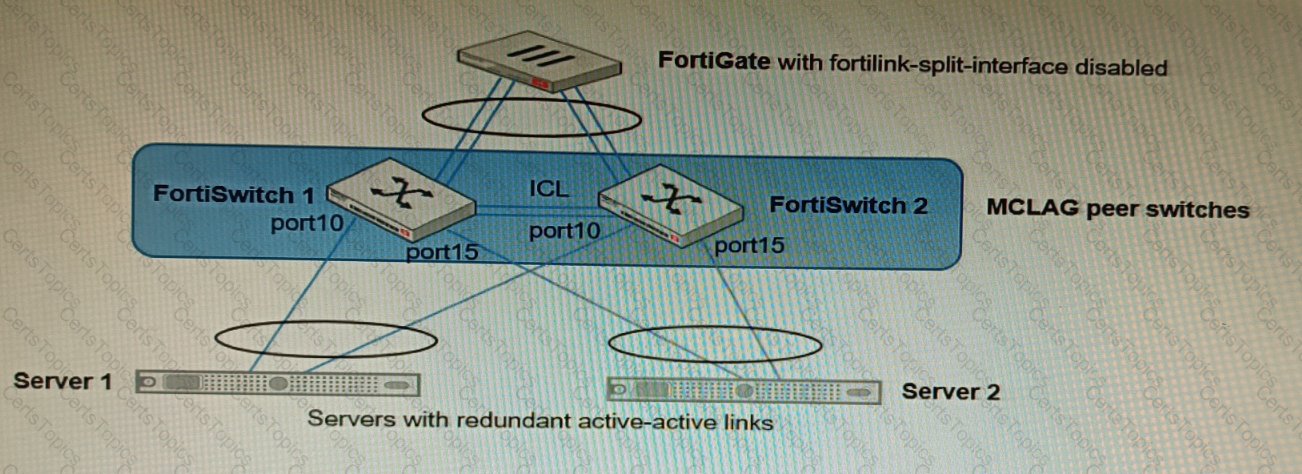
You have been tasked with replacing the managed switch Forti Switch 2 shown in the topology.
Which two actions are correct regarding the replacement process? (Choose two.)
Refer to the exhibits.
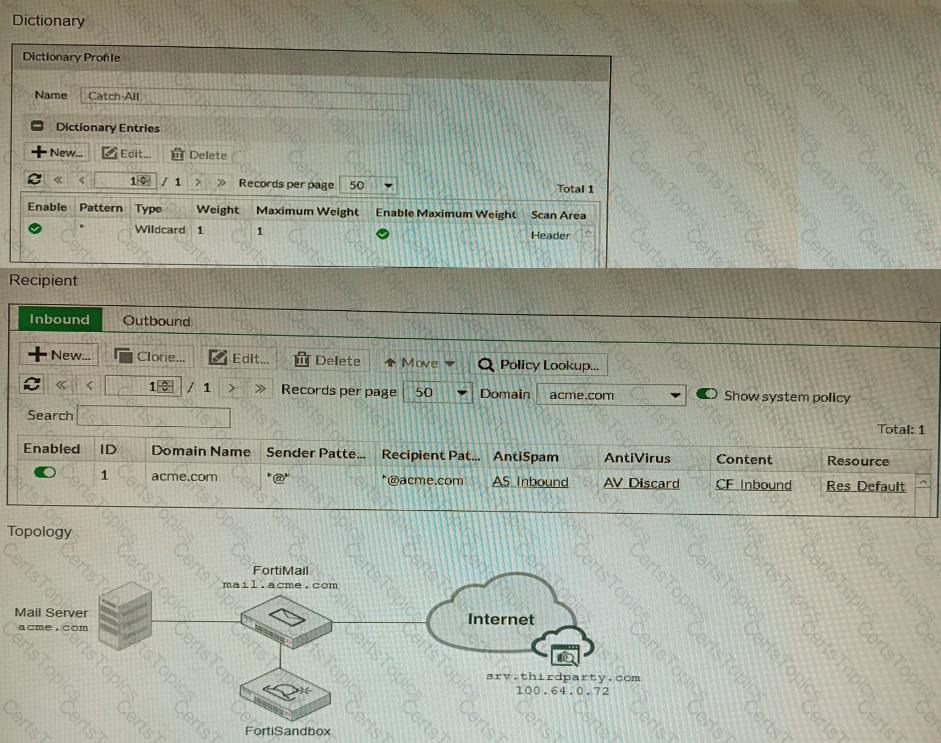
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
Refer to the exhibits.
Exhibit A
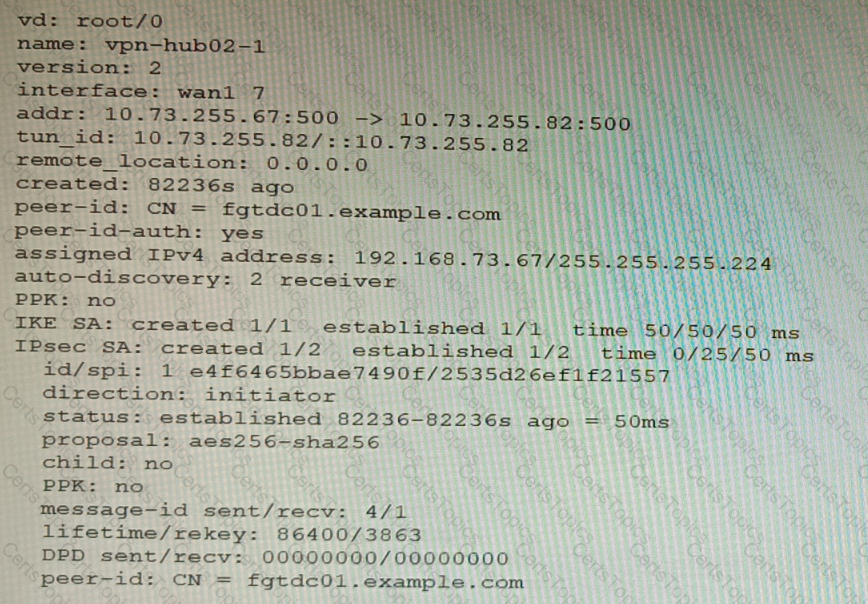
Exhibit B
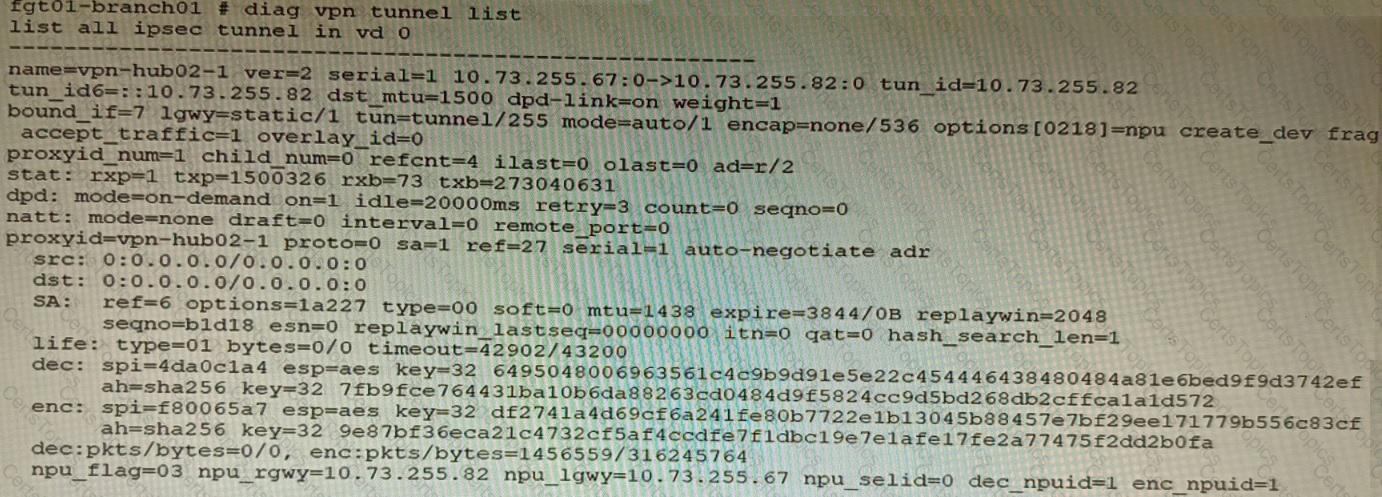
Exhibit C
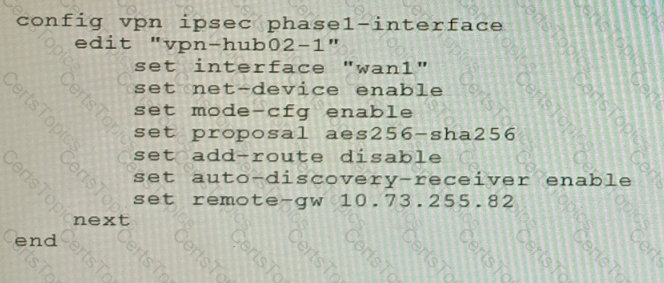
A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
A)
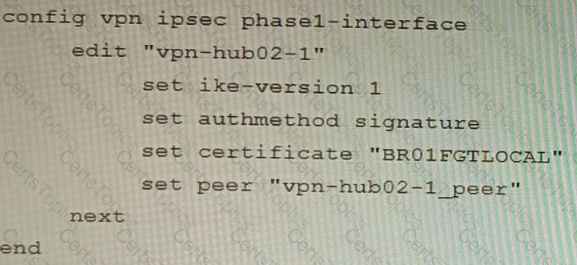
B)
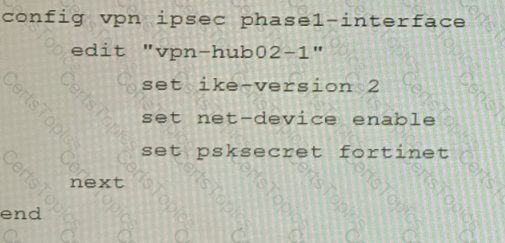
C)
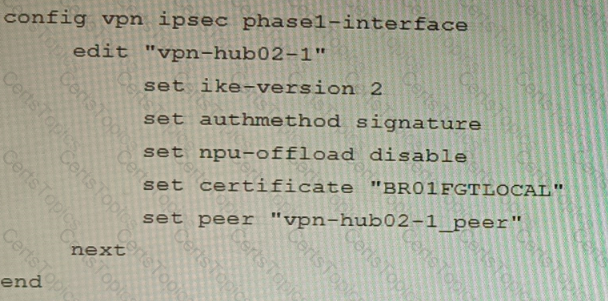
D)
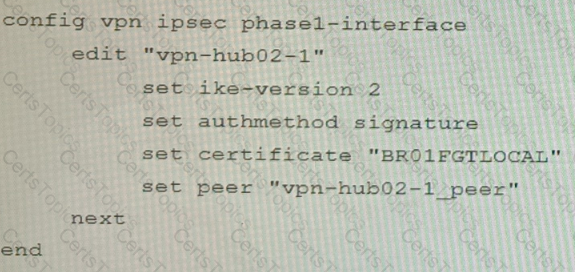
On a FortiGate Configured in Transparent mode, which configuration option allows you to control Multicast traffic passing through the?

A FortiGate deployment contains the following configuration:
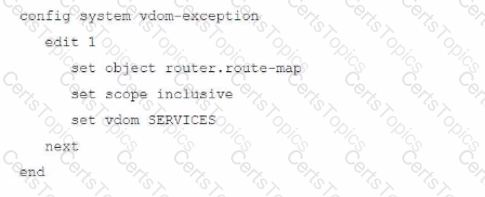
What is the result of this configuration?
Refer to the exhibits.
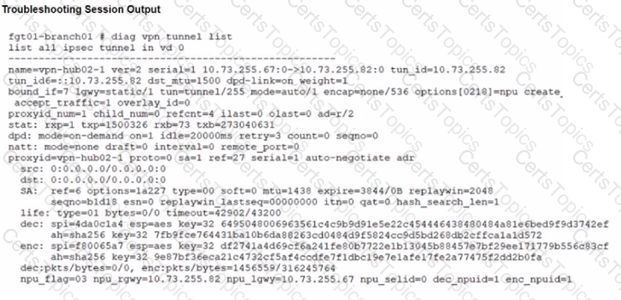
A customer is trying to restore a VPN connection configured on a FortiGate. Exhibits show output during a troubleshooting session when the VPN was working and the current baseline VPN configuration.
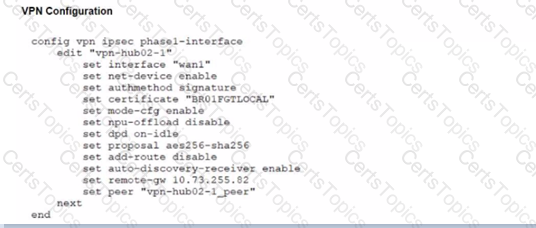
Which configuration parameters will restore VPN connectivity based on the diagnostic output?
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)