An AWS administrator must ensure that each member of the cloud deployment team has the correct permissions to deploy and manage resources using CloudFormation. The administrator is researching which tasks must be executed with CloudFormation and therefore require CloudFormation permissions.
Which task is run using CloudFormation?
What are two main features in Amazon Web Services (AWS) network access control lists (NACLs)? (Choose two answers)
Refer to the exhibit.
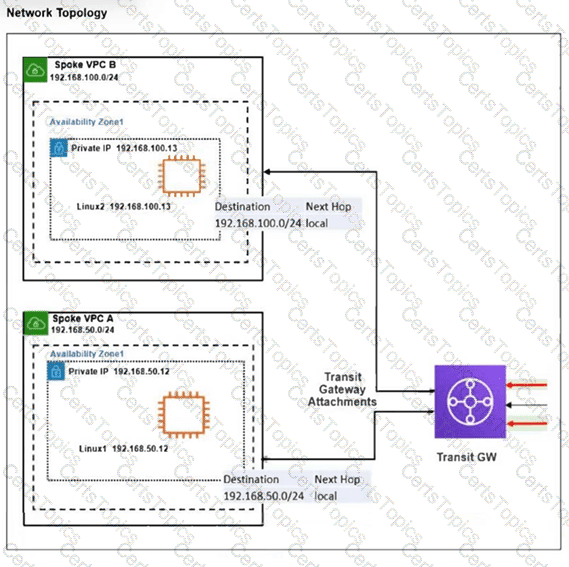
The exhibit shows a customer deployment of two Linux instances and their main routing table in Amazon Web Services (AWS). The customer also created a Transit Gateway (TGW) and two attachments. Which two steps are required to route traffic from Linux instances to the TGW? (Choose two answers)
Exhibit.
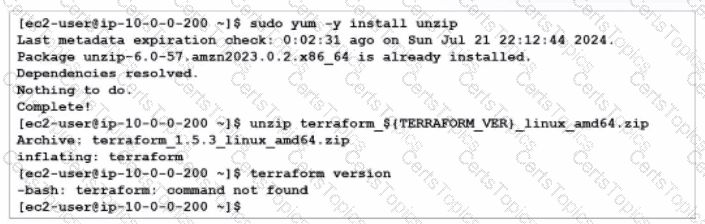
You are tasked with deploying FortiGate using Terraform. When you run the terraform version command during the Terraform installation, you get an error message.
What could you do to resolve the command not found error?
Refer to the exhibit.

An administrator used the what-if tool to preview changes to an Azure Bicep file.
What will happen if the administrator decides to apply these changes in Azure?
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
An organization is deploying FortiDevSec to enhance security for containerized applications, and they need to ensure containers are monitored for suspicious behavior at runtime.
Which FortiDevSec feature is best for detecting runtime threats?
Refer to the exhibit.
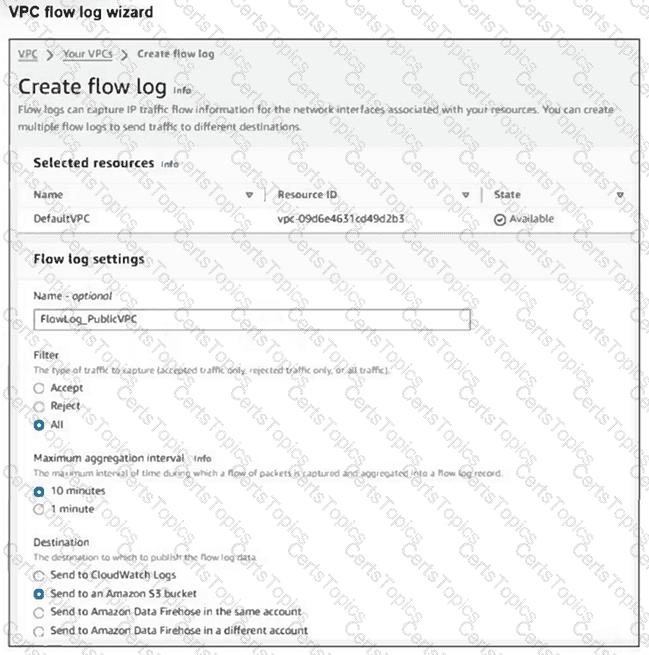
Your team notices an unusually high volume of traffic sourced at one of the organizations FortiGate EC2 instances. They create a flow log to obtain and analyze detailed information about this traffic. However, when they checked the log, they found that it included traffic that was not associated with the FortiGate instance in question.
What can they do to obtain the correct logs? (Choose one answer)
An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.

What can you conclude about the topology shown in FortiView?
Refer to the exhibit.
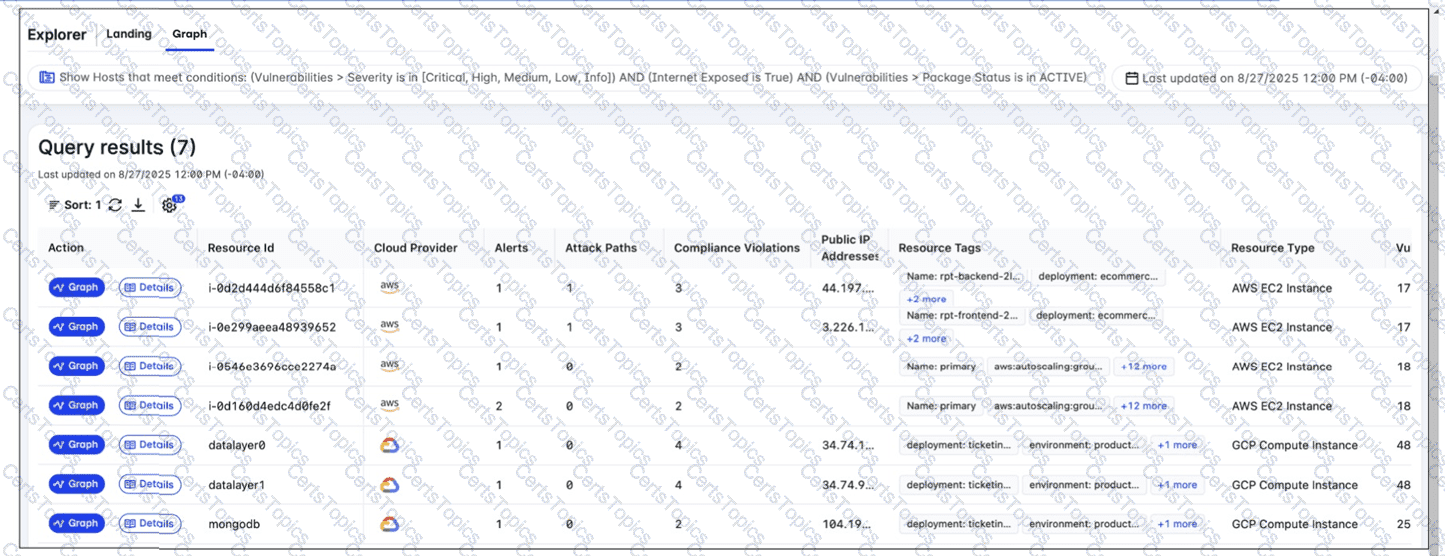
A FortiCNAPP administrator used the FortiCNAPP Explorer to reveal all hosts exposed to the internet that are running active packages with vulnerabilities of all severity levels. Why do only the first two results have an attack path? (Choose one answer)
Refer to the exhibit.
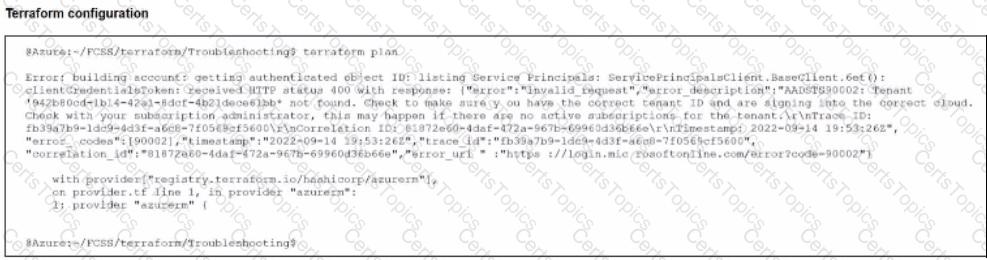
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run.
Which two statements about running the terraform plan command are true? (Choose two.)
You are investigating an attack path for a top risky host. You notice that the Common Vulnerability Scoring System (CVSS) and the vulnerability impact scores are very high. However, the attack path severity for the top risky host itself is low. Which two pieces of contextualized information can help you understand why? (Choose two answers)
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs. What is the best connection solution available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose one answer)
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?