Refer to the exhibits.
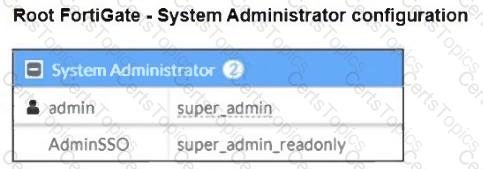
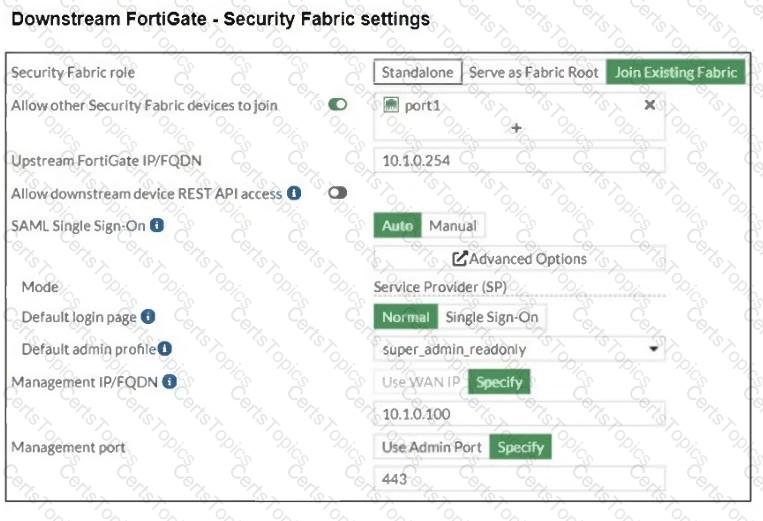
The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?
Refer to the exhibit, which shows an enterprise network connected to an internet service provider.
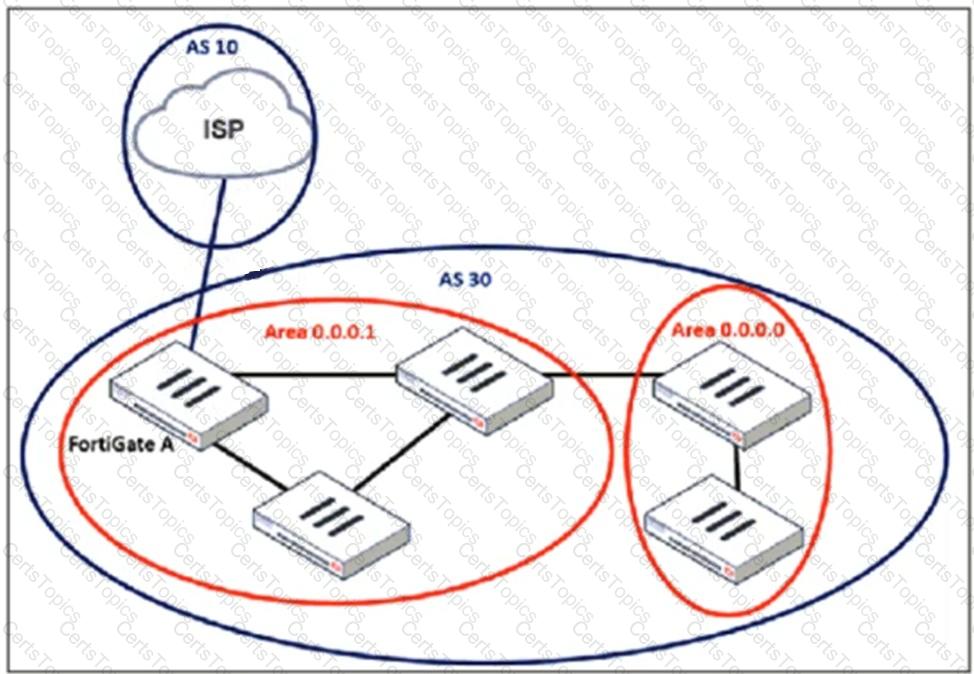
An administrator must configure a loopback as a BGP source to connect to the ISP.
Which two commands are required to establish the connection? (Choose two.)
Refer to the exhibit, which shows the packet capture output of a three-way handshake between FortiGate and FortiManager Cloud.
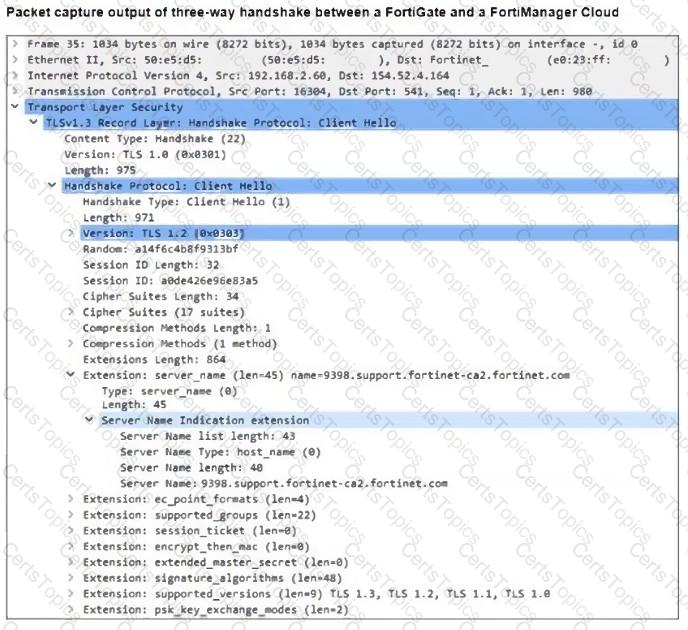
What two conclusions can you draw from the exhibit? (Choose two.)
Refer to the exhibit, which shows a network diagram.
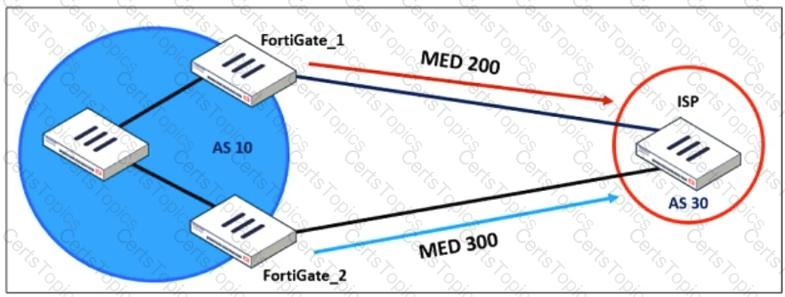
An administrator would like to modify the MED value advertised from FortiGate_1 to a BGP neighbor in the autonomous system 30.
What must the administrator configure on FortiGate_1 to implement this?
An administrator wants to scale the IBGP sessions and optimize the routing table in an IBGP network.
Which parameter should the administrator configure?
Refer to the exhibit, which contains a partial VPN configuration.

What can you conclude from this VPN IPsec phase 1 configuration?
Refer to the exhibit.
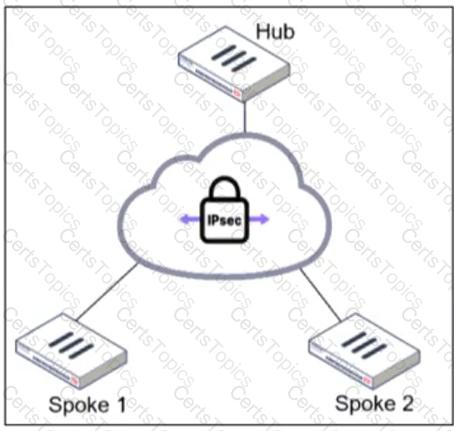
An administrator is deploying a hub and spokes network and using OSPF as dynamic protocol.
Which configuration is mandatory for neighbor adjacency?
Refer to the exhibit, which shows an ADVPN network
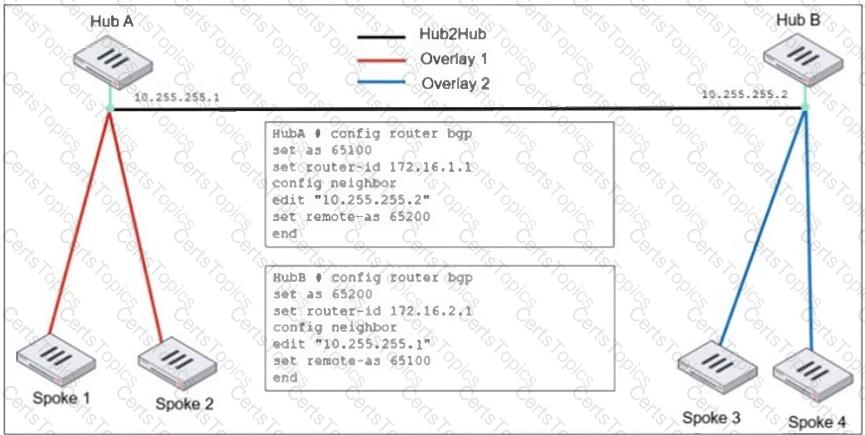
An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with 2.
What two options must the administrator configure in BGP? (Choose two.)
You are using Virtual eXtensible LAN (VXLAN) extensively on FortiGate. Which specialized acceleration hardware must you use to improve FortiGate performance? (Choose one answer)
Refer to the exhibit, which shows a corporate network and a new remote office network.
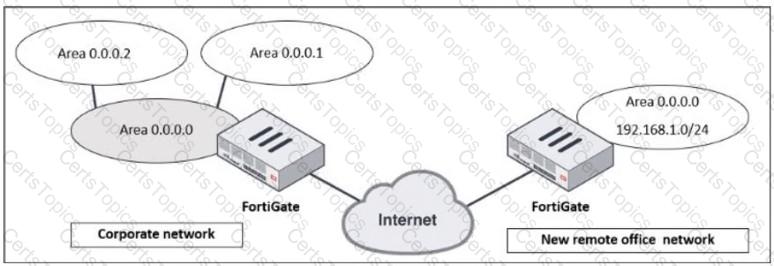
An administrator must integrate the new remote office network with the corporate enterprise network.
What must the administrator do to allow routing between the two networks?
Refer to the exhibit, which shows an OSPF network.
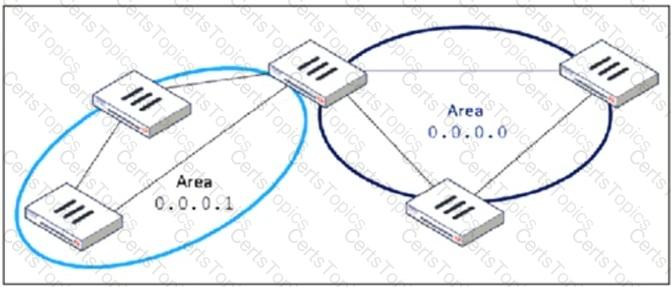
Which configuration must the administrator apply to optimize the OSPF database?
Refer to the exhibit.
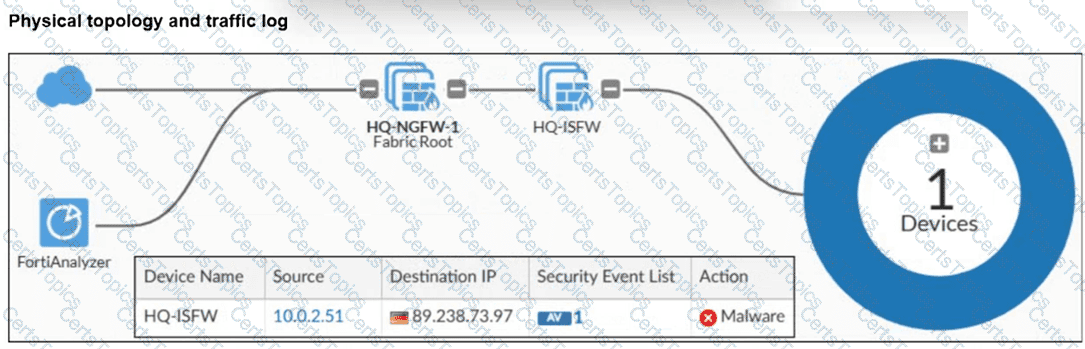
A physical topology along with a traffic log is shown. You are using FortiAnalyzer to monitor traffic from the device with IP address 10.0.2.51, which is located behind the FortiGate internal segmentation firewall (ISFW) device. Unified threat management (UTM) is not enabled in the firewall policy on the HQ-ISFW device, and you are surprised to see a log with the action Malware, as shown in the exhibit. What are two reasons why FortiAnalyzer would display this log? (Choose two answers)
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
Refer to the exhibit, which shows the ADVPN IPsec interface representing the VPN IPsec phase 1 from Hub A to Spoke 1 and Spoke 2, and from Hub В to Spoke 3 and Spoke 4.

An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with 2.
What must the administrator configure in the phase 1 VPN IPsec configuration of the ADVPN tunnels?
Refer to the exhibit, which contains a partial command output.
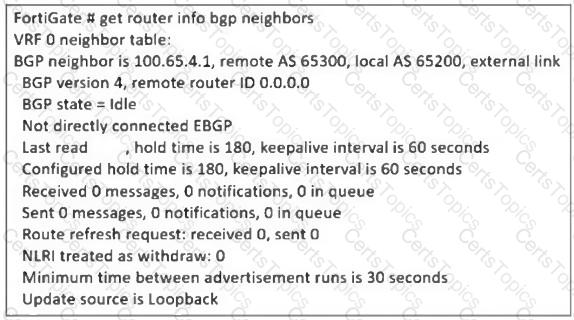
The administrator has configured BGP on FortiGate. The status of this new BGP configuration is shown in the exhibit.
What configuration must the administrator consider next?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
Refer to the exhibit, which contains the partial output of an OSPF command.
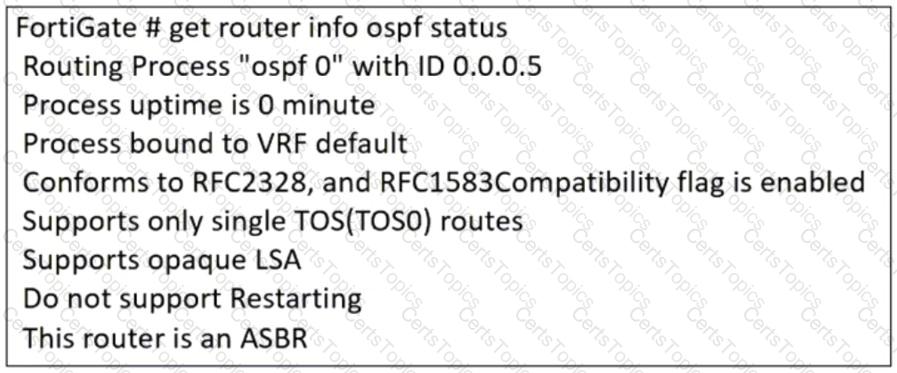
An administrator is checking the OSPF status of a FortiGate device and receives the output shown in the exhibit.
Which statement on this FortiGate device is correct?
Refer to the exhibit, which shows the ADVPN network topology and partial BGP configuration.


Which two parameters must an administrator configure in the config neighbor range for spokes shown in the exhibit? (Choose two.)
An administrator is checking an enterprise network and sees a suspicious packet with the MAC address e0:23:ff:fc:00:86.
What two conclusions can the administrator draw? (Choose two.)