A FortiMail administrator is concerned about cyber criminals attempting to get sensitive information from employees using whaling phishing attacks. What option can the administrator configure to prevent these types of attacks?
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
Refer to the exhibit which displays a topology diagram.
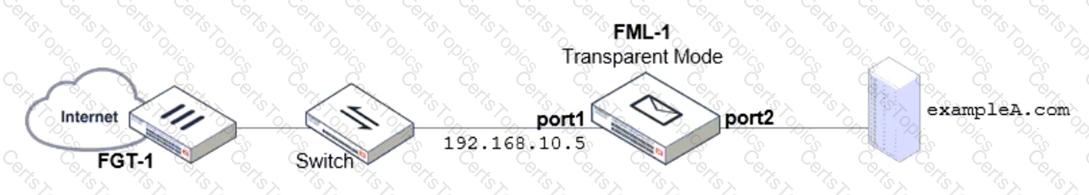
Which two statements describe the built-in bridge functionality on a transparent mode FortiMail? (Choose two.)
Refer to the exhibit, which shows an inbound recipient policy.
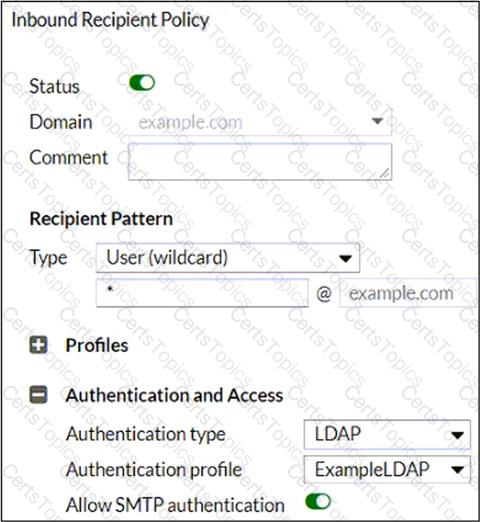
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?