Which of the following scripts would set the database recovery model for sys.database?
A)
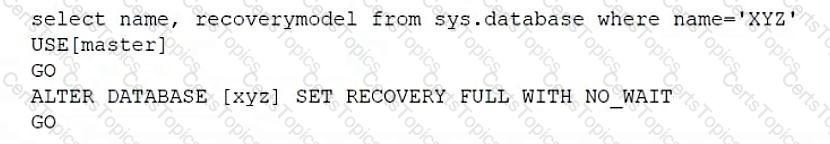
B)
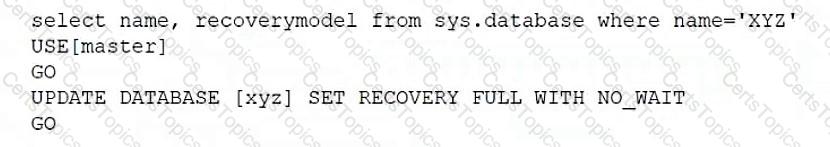
C)

D)
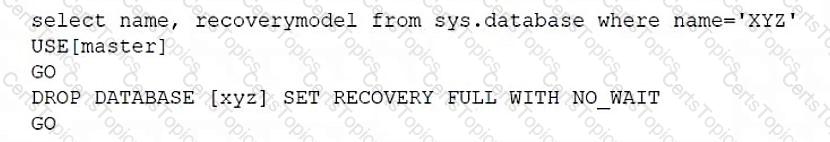
Which of the following describes the purpose of a snapshot?
Which of the following is the correct order of the steps in the database deployment process?
A)
1. Connect
2. Install
3. Configure
4. Confirm prerequisites
5. Validate
6. Test
7. Release
B)
1. Configure
2. Install
3. Connect
4. Test
5. Confirm prerequisites
6. Validate
7. Release
C)
1. Confirm prerequisites
2. Install
3. Configure
4. Connect
5. Test
6. Validate
7. Release
D)
1. Install
2. Configure
3. Confirm prerequisites
4. Connect
5. Test
6. Validate
7. Release
An automated script is using common passwords to gain access to a remote system. Which of the following attacks is being performed?
Which of the following is thebestway to migrate a large data load from one table to another, considering total time and blocking?
Which of the following constraints is used to enforce referential integrity?
A database administrator would like to create a table named XYZ. Which of the following queries should the database administrator use to create the table?
A)
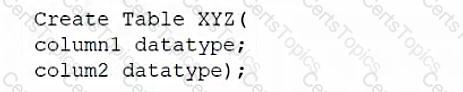
B)
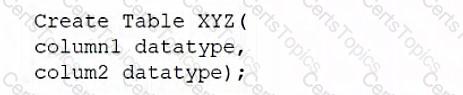
C)
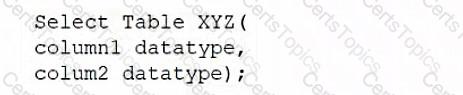
D)
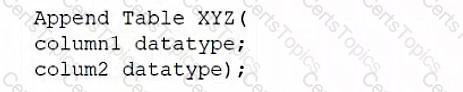
Following a security breach, a database administrator needs to ensure users cannot change data unless a request is approved by the management team. Which of the following principles addresses this issue?
A database professional is considering denormalizing a database. Which of the following documents should be used to analyze the database's structure?
Which of the following describes a scenario in which a database administrator would use a relational database rather than a non-relational database?
A database administrator is migrating the information in a legacy table to a newer table. Both tables contain the same columns, and some of the data may overlap.
Which of the following SQL commands should the administrator use to ensure that records from the two tables are not duplicated?
A database administrator needs to ensure database backups are occurring on a daily basis and at scheduled times. Which of the following actions should the administrator take?
Which of the followingbestdescribes a collection of data that shares the same properties or attributes?
A DBA left the company, and the DBA's account was removed from the system. Soon after, scheduled jobs began failing.
Which of the following would have most likely prevented this issue?
Which of the following is a typical instruction that is found on a Linux command-line script and represents a system shell?
Which of the following firewall types allows an administrator to control traffic and make decisions based on factors such as connection information and data flow communications?
A database administrator is conducting a stress test and providing feedback to a team that is developing an application that uses the Entity Framework. Which of the following explains the approach the administrator should use when conducting the stress test?
Which of the following tools is used for natively running a Linux system in Windows?
A business analyst is using a client table and an invoice table to create a database view that shows clients who have not made purchases yet. Which of the following joins ismostappropriate for the analyst to use to create this database view?
Which of the following is used to hide data in a database so the data can only be read by a user who has a key?
Which of the following database structures is a type of NoSQL database?
Which of the following ismostlikely to prevent tampering with server hardware that houses data?
A group of developers needs access to a database in a development environment, but the database contains sensitive data. Which of the following should the database administrator do before giving the developers access to the environment?