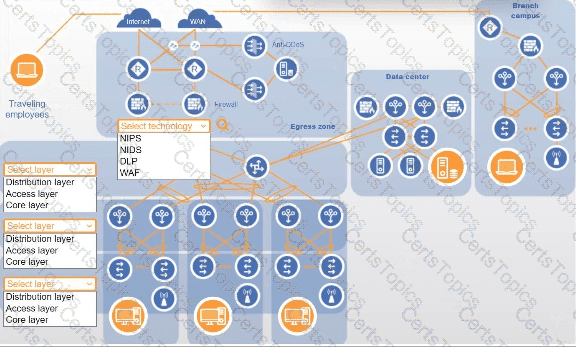
You are designing a campus network with a three-tier hierarchy and need to ensure secure connectivity between locations and traveling employees.
INSTRUCTIONS
Review the command output by clicking on the server, laptops, and workstations on the network.
Use the drop-down menus to determine the appropriate technology and label for each layer on the diagram. Options may only be used once.
Click on the magnifying glass to make additional configuration changes.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A developer reports errors when trying to access a web application. The developer uses Postman to troubleshoot and receives the following error:
HTTP Status: 403 Forbidden
Headers include authentication-related variables such as access_key, signature, salt, and timestamp
The request is a GET request to a payment methods API
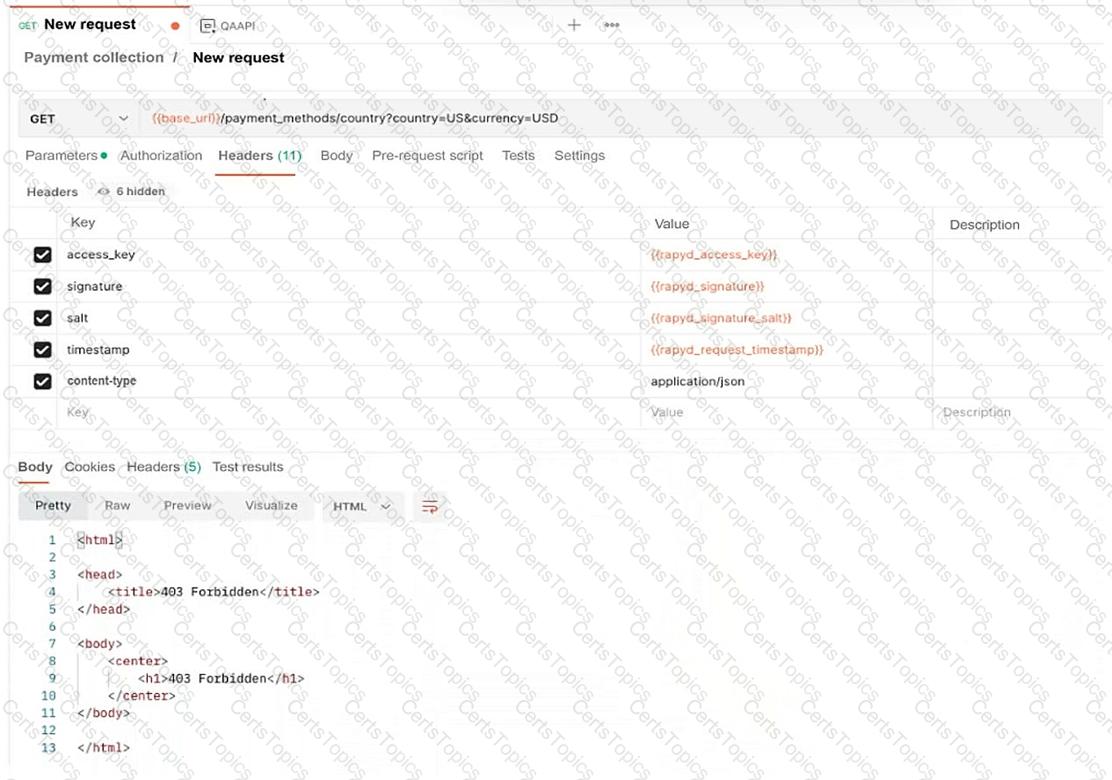
Which of the following is the cause of the issue?
A network architect must design a new branch network that meets the following requirements:
No single point of failure
Clients cannot be impacted by changes to the underlying medium
Clients must be able to communicate directly to preserve bandwidth
Which of the following network topologies should the architect use?
A network architect needs to design a new network to connect multiple private data centers. The network must:
Provide privacy for all traffic between locations
Use preexisting internet connections
Use intelligent steering of application traffic over the best path
Which of the following best meets these requirements?
An organization wants to evaluate network behavior with a network monitoring tool that is not inline. The organization will use the logs for further correlation and analysis of potential threats. Which of the following is the best solution?
Throughout the day, a sales team experiences videoconference performance issues when the accounting department runs reports. Which of the following is the best solution?
A network load balancer is not correctly validating a client TLS certificate. The network architect needs to validate the certificate installed on the load balancer before progressing. Which of the following commands should the architect use to confirm whether the private key and certificate match?
A network engineer is working on securing the environment in the screened subnet. Before penetration testing, the engineer would like to run a scan on the servers to identify the OS, application versions, and open ports. Which of the following commands should the engineer use to obtain the information?
As part of a project to modernize a sports stadium and improve the customer service experience for fans, the stadium owners want to implement a new wireless system. Currently, all tickets are electronic and managed by the stadium mobile application. The new solution is required to allow location tracking precision within 5ft (1.5m) of fans to deliver the following services:
Emergency/security assistance
Mobile food order
Event special effects
Raffle winner location displayed on the giant stadium screen
Which of the following technologies enables location tracking?
An administrator logged in to a cloud account on a shared machine but forgot to log out after the session ended. Which of the following types of security threats does this action pose?
A network administrator must connect a remote building at a manufacturing plant to the main building via a wireless connection. Which of the following should the administrator choose to get the greatest possible range from the wireless connection? (Choose two.)
A network engineer adds a large group of servers to a screened subnet and configures them to use IPv6 only. The servers need to seamlessly communicate with IPv4 servers on the internal networks. Which of the following actions is the best way to achieve this goal?
An outage occurred after a software upgrade on core switching. A network administrator thinks that the firmware installed had a bug. Which of the following should the network administrator do next?
A network security engineer must secure a web application running on virtual machines in a public cloud. The virtual machines are behind an application load balancer. Which of the following technologies should the engineer use to secure the virtual machines? (Choose two.)
A network engineer is installing new switches in the data center to replace existing infrastructure. The previous network hardware had administrative interfaces that were plugged into the existing network along with all other server hardware on the same subnet. Which of the following should the engineer do to better secure these administrative interfaces?
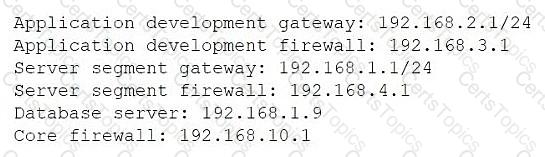
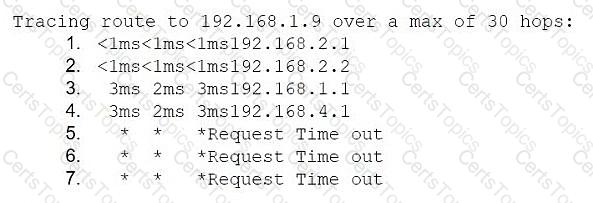
Application development team users are having issues accessing the database server within the cloud environment. All other users are able to use SSH to access this server without issues. The network architect reviews the following information to troubleshoot the issue:
Traceroute output from an application developer's machine with the assigned IP 192.168.2.7:
Application development gateway: 192.168.2.1/24
Server segment gateway: 192.168.1.1/24
Database server: 192.168.1.9
Application developer machine IP: 192.168.2.7
Traceroute ends at hop 4: 192.168.4.1 (server segment firewall), then times out
Which of the following is the most likely cause of the issue?
A network architect is working on a physical network design template for a small education institution's satellite campus that is not yet built. The new campus location will consist of two small buildings with classrooms, one screening room with audiovisual equipment, and 200 seats for students. Which of the following enterprise network designs should the architect suggest?
A cloud architect must recommend an architecture approach for a new medical application that requires the lowest downtime possible. Which of the following is the best application deployment strategy given the high-availability requirement?
A company is experiencing numerous network issues and decides to expand its support team. The new junior employees will need to be onboarded in the shortest time possible and be able to troubleshoot issues with minimal assistance. Which of the following should the company create to achieve this goal?
A network security administrator needs to set up a solution to:
Gather all data from log files in a single location.
Correlate the data to generate alerts.
Which of the following should the administrator implement?
A network architect needs to design a solution to ensure every cloud environment network is built to the same baseline. The solution must meet the following requirements:
Use automated deployment.
Easily update multiple environments.
Share code with a community of practice.
Which of the following are the best solutions? (Choose two.)
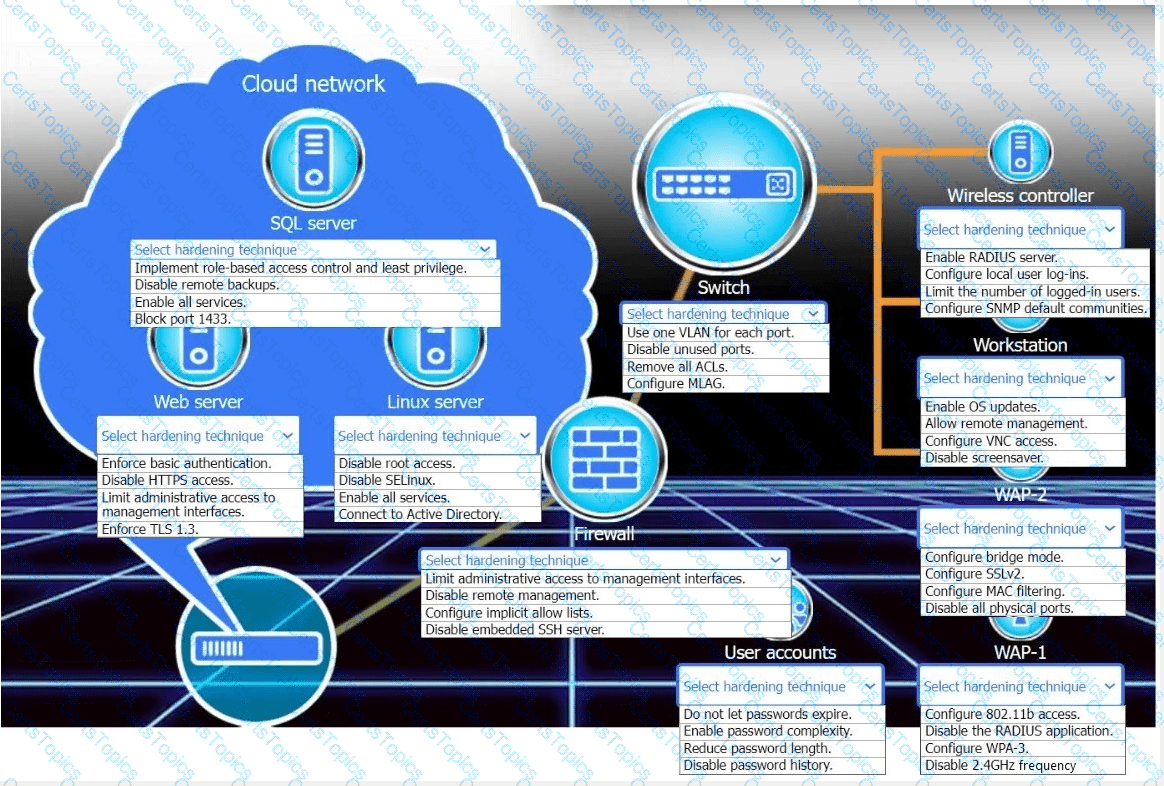
New devices were deployed on a network and need to be hardened.
INSTRUCTIONS
Use the drop-down menus to define the appliance-hardening techniques that provide themostsecure solution.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An architect needs to deploy a new payroll application on a cloud host. End users' access to the application will be based on the end users' role. In addition, the host must be deployed on the 192.168.77.32/30 subnet. Which of the following Zero Trust elements are being implemented in this design? (Choose two.)
An organization's Chief Technical Officer is concerned that changes to the network using IaC are causing unscheduled outages. Which of the following best mitigates this risk?
A security architect needs to increase the security controls around computer hardware installations. The requirements are:
Auditable access logs to computer rooms
Alerts for unauthorized access attempts
Remote visibility to the inside of computer rooms
Which of the following controls best meet these requirements? (Choose two.)