An application is creating hashes of each file on an attached storage device. Which of the following will typically occur during this process?
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
A distributed denial-of-service (DDOS) attack has occurred where both ICMP and TCP packets have crashed the company's Web server. Which of the following techniques will best help reduce the severity of this attack?
Consider the following diagram:
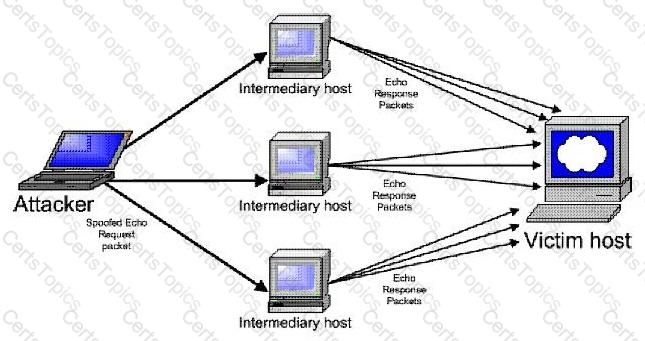
Which type of attack is occurring?
Requests for Web-based resources have become unacceptably slow. You have been assigned to implement a solution that helps solve this problem. Which of the following would you recommend?
Which of the following standards is used for digital certificates?
You have been assigned to provide security measures for your office's reception area. Although the company needs to provide security measures, costs must be kept to a minimum. Which of the following tools is the most appropriate choice?
Consider the following diagram:
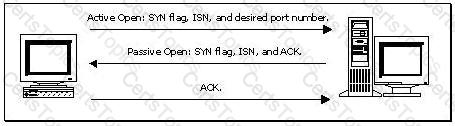
Which of the following best describes the protocol activity shown in the diagram, along with the most likely potential threat that accompanies this protocol?
Which of the following is most likely to address a problem with an operating system's ability to withstand an attack that attempts to exploit a buffer overflow?