A customer managing a large network has implemented location services. Due to heavy load, it is needed to load balance the data coming through NMSP from the WLCs. Load must be spread between multiple CMX servers to help optimize the data flow for APs. Which configuration in CMX meets this requirement?
An engineer is configuring location services within Cisco Spaces (formerly Cisco DNA Spaces). The solution must track interfering devices. Which component of Cisco Spaces must be configured?
An engineer is configuring wireless guests using Cisco CWA. When a device connects, it must be redirected to the WebAuth, but this was failing. What must be configured for the device to be redirected correctly?
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
An engineer must implement rogue containment for an SSID. What is the maximum number of APs that should be used for containment?
A network engineer must segregate all IPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using Cisco
ISE?
An enterprise has recently deployed a voice and video solution available to all employees using AireOS controllers. The employees must use this service over their laptops, but users report poor service when connected to the wireless network. The programs that consume bandwidth must be identified and restricted. Which configuration on the WLAN aids in recognizing the traffic?
Refer to the exhibit.

An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
An engineer is considering an MDM integration with Cisco ISE to assist with security for lost devices.
Which two functions of MDM increase security for lost devices that access data from the network? (Choose two.)
A network engineer is configuring a Cisco AireOS WLC environment for central web authentication using Cisco ISE.
The controllers are configured using auto-anchor for the guest network.
Which three components must be implemented for the foreign WLC?(Choose three.)
Refer to the exhibit.
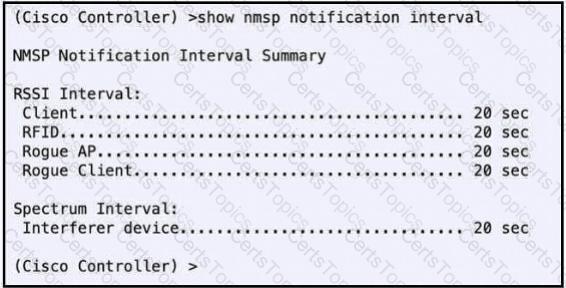
An administrator notices slower location updates from the controller to Cisco CMX. Which command must be configured to get an update every 5 seconds for rogues?
Refer to the exhibit.

An engineer implemented the CPU ACL on your Cisco 5520 Series Wireless LAN Controller, and the controller is no longer manageable via the network. What must be changes on this CPU ACL to enable it to manage the controller again?
All APs are receiving multicast traffic, instead of only the APs that need it. What is the cause of this problem?
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
What is characteristic of Multicast mode that affects the wireless network when configured on a Cisco WLC?
What is the maximum time range that can be viewed on the Cisco DNA Center issues and alarms page?
Refer to the exhibit.
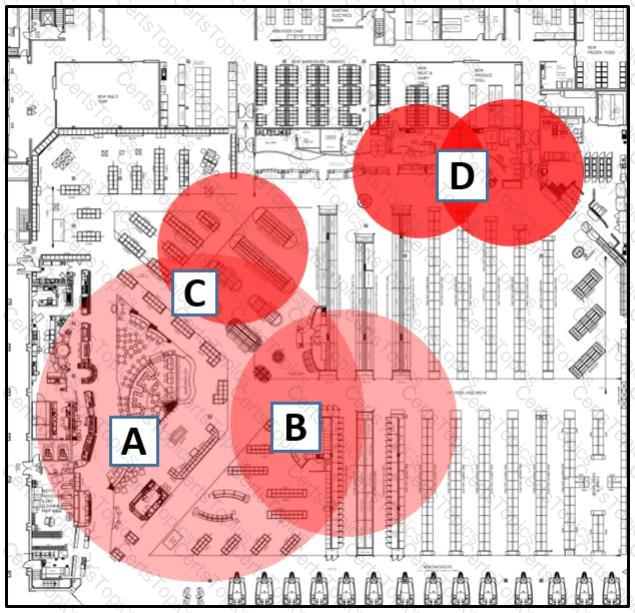
Which area indicates the greatest impact on the wireless network when viewing the Cisco CleanAir Zone of Impact map of interferers?
An engineer is configuring an autonomous AP to allow 802.1X authentication for users. The policy on the RADIUS server only allows for EAP-TLS authentication. Which authentication method must the engineer select under the Client Authentication Settings for the SSID on the AP?
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
Refer to the exhibit.
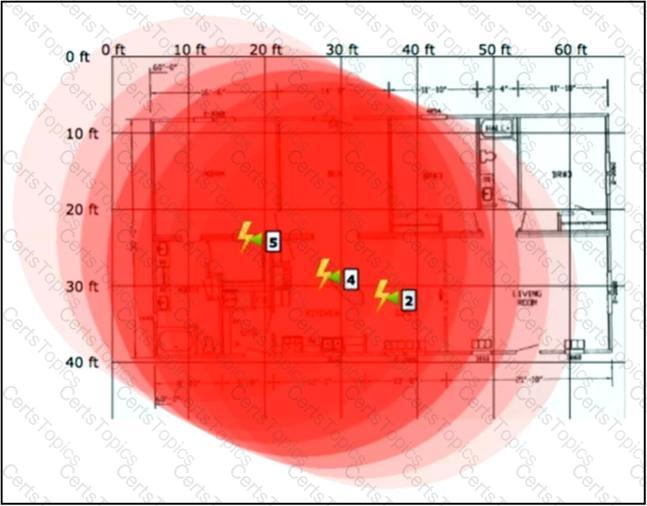
An engineer needs to manage non-802.11 interference. What is observed in the output on PI?
Refer to the exhibit. A network administrator must automate notifications for Security Advisories Data reports on the Cisco Catalyst Center v2.3.7 using the Report notification feature. Preferring a programmable approach over UI/CLI, the administrator decides to create a webhook via the Cisco DNA Center API to send real-time HTTP notifications to an external application. The webhook URL https://example.com/webhook uses HTTPS with a self-signed certificate, which requires a specific configuration in the payload to ensure the webhook functions correctly. Which code snippet must be placed onto the box in the code to complete the Python script that configures the webhook to use the self-signed certificate to extract the Security Advisories Data report?

A FlexConnect remote office deployment is using five 2702i APs indoors and two 1532i APs outdoors. When a code upgrade is performed and FlexConnect Smart AP Image Upgrade is leveraged, but no FlexConnect Master AP has been configured, how many image transfers between the WLC and APs will occur?
An engineer completes the setup of a two-node Cisco ISE deployment for a guest portal. When testing the portal, the engineer notices that sometimes there is a certificate CN mismatch. Which certificate type helps resolve this issue?
Which QoS level is recommended for guest services?
Which two restrictions are in place with regards to configuring mDNS? (Choose two.)
What is the difference between PIM sparse mode and PIM dense mode?
Refer to the exhibit.
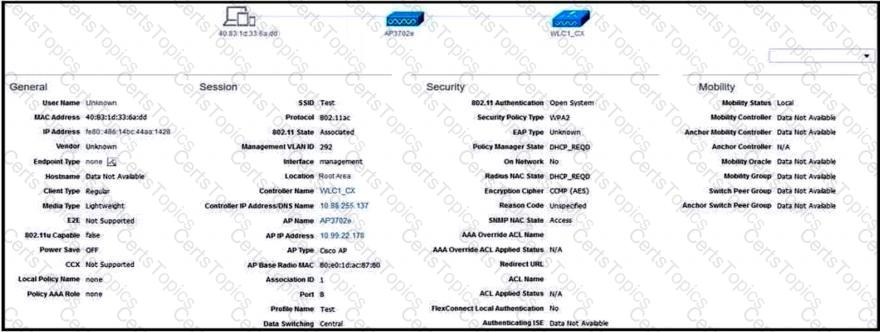
What is the reason that the wireless client cannot get the RUN state?
An engineer has configured passive fallback mode for RADIUS with default timer settings. What will occur when the primary RADIUS fails then recovers?
An engineer must use Cisco AVC on a Cisco WLC to prioritize Cisco IP cameras that use the wireless network. Which element do you configure in a rule?
Which feature on the Cisco Wireless LAN Controller must be present to support dynamic VLAN mapping?
In a Cisco WLAN deployment, it is required that all Aps from branch1 remain operational even if the control plane CAPWAP tunnel is down because of a WAN failure to headquarters. Which operational mode must be configured on the APs?
Refer to the exhibit.

An engineer implemented the CPU ACL on your Cisco 5520 Series Wireless LAN Controller, and the controller is no longer manageable via the network. What must be changes on this CPU ACL to enable it to manage the controller again?
A wireless engineer has performed a Wireshark ccapture on an 802.1x authentication process to troubleshoot a connectivity issue.
Which two types of packet does the EAP contain? (Choose two.)
An engineer set up a VoWLAN with QoS on the WLC and a class map on the switch, but the markings are not being preserved correctly in the end-to- end traffic flow. Which two configurations on the wired network ensure end-to-end QoS? (Choose two.)
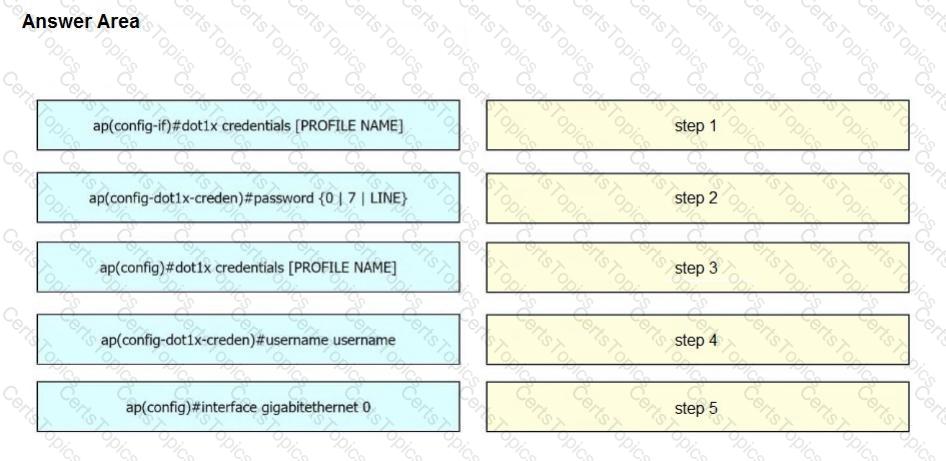
A network engineer must get an autonomous AP to authenticate to the upstream switch via IEEE 802.1 X. Drag and drop the commands from the left onto the right to complete the configuration.
After receiving an alert about a rogue AP, a network engineer logs into Cisco Prime Infrastructure and looks at the floor map where the AP that detected the rogue is located. The map is synchronized with a mobility services engine that determines that the rogue device is actually inside the campus. The engineer determines that the rogue is a security threat and decides to stop if from broadcasting inside the enterprise wireless network. What is the fastest way to disable the rogue?
The security policy mandates that only controller web management traffic is allowed from the IT subnet. In testing, an engineer is trying to connect to a WLAN with Web Authentication for guest users, but the page is timing out on the wireless client browser. What is the cause of the issue?
An engineer has configured Media Stream on the WLC and must guarantee at least 2 Mbps stream per user. Which RRC template should the engineer use?
An engineer is troubleshooting rogue access points that are showing up in Cisco Prime Infrastructure.
What is maximum number of APS the engineer can use to contain an identified rogue access point in the WLC?
On a branch office deployment, it has been noted that if the FlexConnect AP is in standalone mode and loses connection to the WLC, all clients are disconnected, and the SSID is no longer advertised. Considering that FlexConnect local switching is enabled, which setting is causing this behavior?
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
Branch wireless users report that they can no longer access services from head office but can access services locally at the site. New wireless users can associate to the wireless while the WAN is down. Which three elements (Cisco FlexConnect state, operation mode, and authentication method) are seen in this scenario? (Choose three.)
A network engineer is deploying 8865 IP phones with wireless clients connected to them. In order to apply the appropriate QoS, the IP voice traffic needs to be distinguished from client data traffic. Which switch configuration feature must be enabled?
An engineer has successfully implemented 10 active RFID tags in an office environment. The tags are not visible when the location accuracy is tested on the Cisco CMX Detect and Locate window. Which setting on Cisco CMX allows the engineer to view the tags?
A wireless engineer deployed all remote sites as FlexConnect. The client VLAN assignment on these sites is configured manually mapped by WLAN and using local switching. Dynamic VLAN assignment is provided by the newly deployed Cisco ISE. Which IETF attribute must be configured on the AAA server to send that VLAN ID?
An engineer configures a deployment to support:
Cisco CMX
licenses for at least 3000 APs
6000 wIPS licenses
The Cisco vMSE appliance must be sized for this deployment. Which Cisco vMSE Release 8 option must the engineer deploy?
A customer wants the APs in the CEO’s office to have different usernames and passwords for administrative support than the other APs deployed throughout the facility. Which feature must be enabled on the WLC and APs to achieve this goal?
A wireless network has been implemented to enable multicast video to be streamed reliably over the wireless link to the wireless users. After a client reports that the video is unable to stream, the administrator determines that the client is connecting at a data rate of 12 Mbps and is trying to stream to a valid multicast address on the network. Which two actions must be applied? (Choose two.)
A shopping center uses AireOS controllers with Cisco Wave 2 APs. A separate WLAN named Guest-012345678-WLAN is used for guest wireless clients. Management needs location analytics to determine popular areas. CMX must track only associated clients. What must be selected on the CMX server settings?
Which EAP method can an AP use to authenticate to the wired network?
What must be configured on ISE version 2.1 BYOD when using Single SSID?
A WLC must be configured to allow multiple mDNS profiles based on a user authentication profile configured in Cisco ISE. Which WLAN setting must be configured?
Which devices can be tracked with the Cisco Context Aware Services?
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
An engineer must configure Cisco OEAPs for three executives. As soon as the NAT address is configured on the management interface, it is noticed that the WLC is not responding for APs that are trying to associate to the internal IP management address. Which command should be used to reconcile this?
Refer to the exhibit.
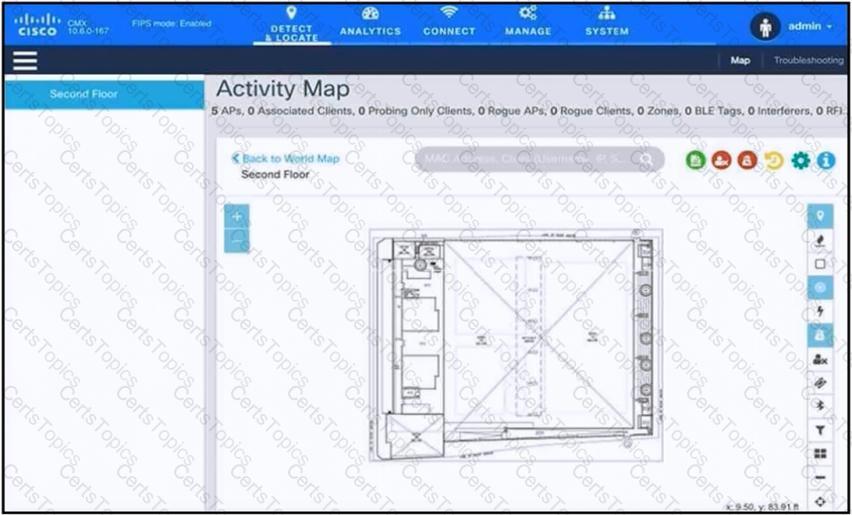
An engineer has deployed the Cisco CMX solution to track and detect the number of users who visit the office each day. The CMX dashboard is not showing any data. Which action resolves this issue?
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
Refer to the exhibit.
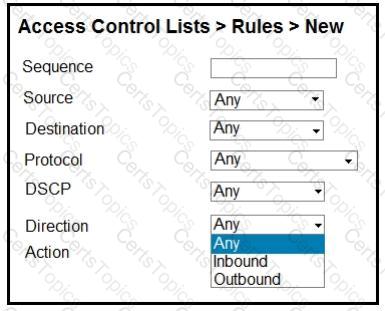
An engineer is creating an ACL to restrict some traffic to the WLC CPU. Which selection must be made from the direction drop- down list?
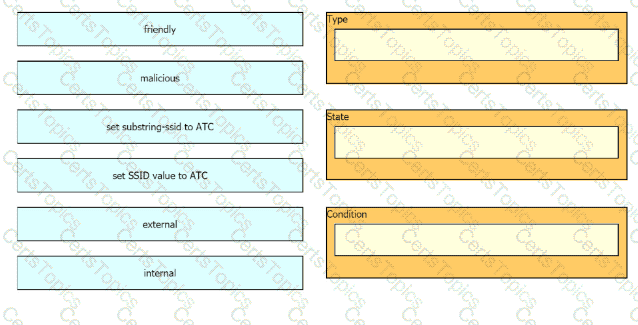
The network management team in a large shopping center has detected numerous rogue APs from local coffee shops that are broadcasting SSIDs. All of these SSIDs have names starting with ATC (for example, ATC302, ATC011, and ATC566). A wireless network engineer must appropriately classify these SSIDs using the Rogue Rules feature. Drag and drop the options from the left onto the categories in which they must be used on the right. Not all options are used.
Refer to the exhibit.
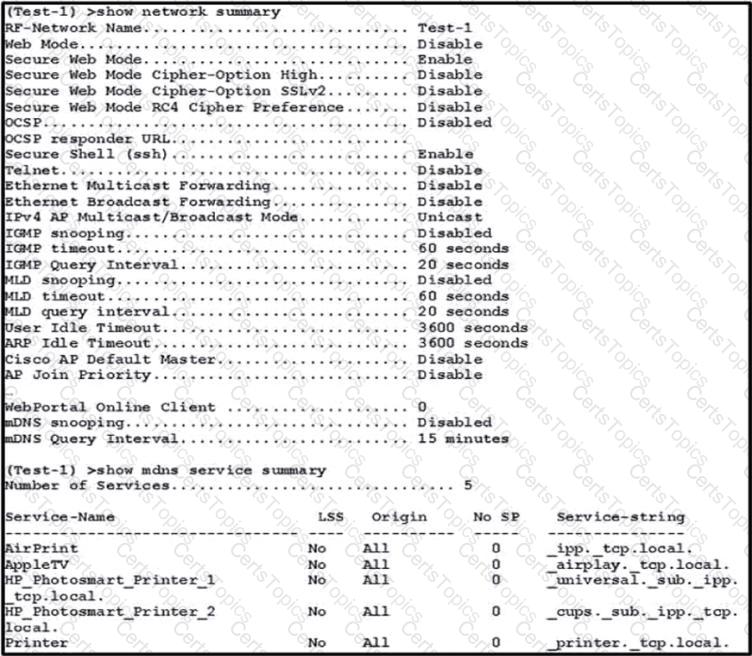
An engineer configured a BYOD policy that allows for printing on the WLAN using Bonjour services. However, the engineer cannot get printing to work. The WLC firmware is 8.x. What must be implemented on the controller?
Refer to the exhibit.

An engineer is troubleshooting a client connectivity issue. The client is in the RUN state, and no traffic is passed after authenticating by using Cisco ISE. Which action resolves the problem?
A Cisco CMX 3375 appliance on the 10.6.1 version code counts duplicate client entries, which creates wrong location analytics. The issue is primarily from iOS clients with the private MAC address feature enabled. Enabling this feature requires an upgrade of the Cisco CMX 3375 appliance in a high availability pair to version 10.6.3. SCP transfers the Cisco CMX image, but the upgrade script run fails. Which configuration change resolves this issue?
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
Which component must be integrated with Cisco DNA Center to display the location of a client that is experiencing connectivity issues?
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
Refer to the exhibit.
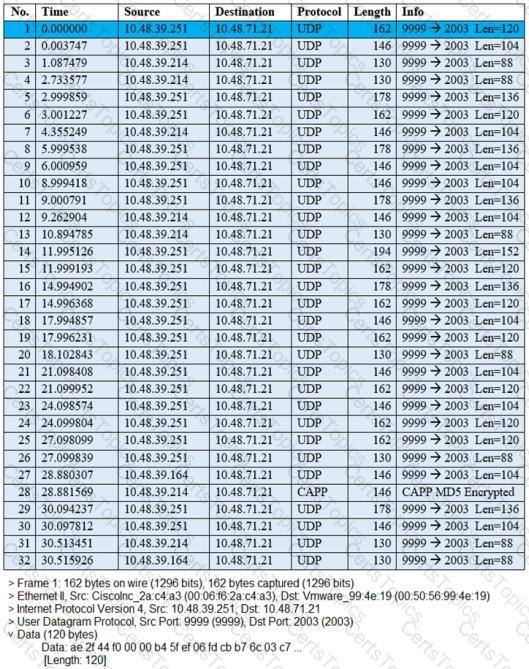
The image shows a packet capture that was taken at the CLI of the Cisco CMX server. It shows UDP traffic from the WLC coming into the server. What does the capture prove?
A corporation has a wireless network where all access points are configured in FlexConnect. The WLC has a Data WLAN and a VoWiFi WLAN implemented where centrally-switched SSID is configured for the APs. Which QoS configuration must be implemented for the wireless packets to maintain the marking across the wired and wireless network?
An engineer wants the wireless voice traffic class of service to be used to determine the queue order for packets received, and then have the differentiated services code point set to match when it is resent to another port on the switch. Which configuration is required in the network?
Where is Cisco Hyperlocation enabled on a Cisco Catalyst 9800 Series Wireless Controller web interface?
Refer to the exhibit.

The security team has implemented ISE as an AAA solution for the wireless network. The wireless engineer notices that though clients are able to authenticate successfully, the ISE policies that are designed to place them on different interfaces are not working. Which configuration must be applied in the RADIUS Authentication Settings section from the ISE Network Device page?
During the EAP process and specifically related to the client authentication session, which encrypted key is sent from the RADIUS server to the access point?
You are configuring the social login for a guest network. Which three options are configurable social connectors in Cisco CMX Visitor Connect? (Chose three)
Which two protocols are used to communicate between the Cisco MSE and the Cisco Prime Infrastructure network management software? (Choose two.)
Refer to the exhibit.
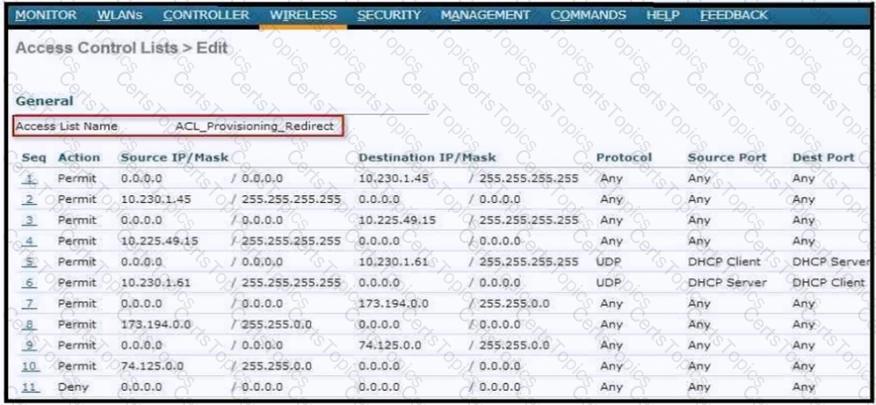
An ACL is configured to restrict access for BYOD clients. The ACL must redirect devices to the guest portal. To which two devices on the local network must the ACL allow access other than the DHCP server? (Choose two.)
Which AP model of the Cisco Aironet Active Sensor is used with Cisco DNA Center?
A hospital wants to offer indoor directions to patient rooms utilizing its existing wireless infrastructure. The wireless network has been using location services specifications. Which two components must be installed to support this requirement? (Choose two.)
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
An engineer is setting up a new unique NAD on a Cisco ISE.
Which two parameters must be configured? (Choose two.)
An SSID is set up with central web authentication using Cisco ISE The new SSID uses guest tunneling from the foreign controller to the anchor controller. Which device must be configured ISE as the one performing the RADIUS authentication requests for the web authentication method?
An engineer set up identity-based networking with ISE and configured AAA override on the WLAN. Which two attributes must be used to change the client behavior from the default settings? (Choose two.)
An engineer is configuring a new wireless network for guest access. The Facebook page of the company must be viewed by the guest users before they get access to the network. A Cisco MSE is used as a wireless component. Which URL must be used in the configuration as the external redirection URL?
What two actions must be taken by an engineer configuring wireless Identity-Based Networking for a WLAN to enable VLAN tagging? (Choose two.)
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port?
