Which NSX feature can be leveraged to achieve consistent policy configuration and simplicity across sites?
Which two logical router components span across all transport nodes? (Choose two.)
How is the RouterLink port created between a Tier-1 Gateway and Tier-O Gateway?
Which three NSX Edge components are used for North-South Malware Prevention? (Choose three.)
Which two choices are use cases for Distributed Intrusion Detection? (Choose two.)
Which CLI command on NSX Manager and NSX Edge is used to change NTP settings?
In which VPN type are the Virtual Tunnel interfaces (VTI) used?
Match the NSX Intelligence recommendations with their correct purpose.

What should an NSX administrator check to verify that VMware Identity Manager Integration Is successful?
An architect receives a request to apply distributed firewall in a customer environment without making changes to the network and vSphere environment. The architect decides to use Distributed Firewall on VDS.
Which two of the following requirements must be met in the environment? (Choose two.)
An administrator needs to download the support bundle for NSX Manager. Where does the administrator download the log bundle from?
An NSX administrator has deployed a single NSX Manager node and will be adding two additional nodes to form a 3-node NSX Management Cluster for a production environment. The administrator will deploy these two additional nodes and Cluster VIP using the NSX UI.
What two are the prerequisites for this configuration? (Choose two.)
Which two are supported by L2 VPN clients? (Choose two.)
What needs to be configured on a Tler-0 Gateway lo make NSX Edge Services available to a VM on a VLAN-backed logical switch?
Which two statements are correct about East-West Malware Prevention? (Choose two.)
Which three security features are dependent on the NSX Application Platform? (Choose three.)
Which two steps must an NSX administrator take to integrate VMware Identity Manager in NSX to support role-based access control? (Choose two.)
What are three NSX Manager roles? (Choose three.)
When a stateful service is enabled for the first lime on a Tier-0 Gateway, what happens on the NSX Edge node'
What are two supported host switch modes? (Choose two.)
When collecting support bundles through NSX Manager, which files should be excluded for potentially containing sensitive information?
Where does an administrator configure the VLANs used In VRF Lite? (Choose two.)
An administrator wants to validate the BGP connection status between the Tier-O Gateway and the upstream physical router.
What sequence of commands could be used to check this status on NSX Edge node?
Which field in a Tier-1 Gateway Firewall would be used to allow access for a collection of trustworthy web sites?
Which two of the following are used to configure Distributed Firewall on VDS? (Choose two.)
Which two statements are true about IDS Signatures? (Choose two.)
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
Which VPN type must be configured before enabling a L2VPN?
Which of the following exist only on Tler-1 Gateway firewall configurations and not on Tier-0?
An NSX administrator is troubleshooting a connectivity issue with virtual machines running on an FSXi transport node. Which feature in the NSX Ul shows the mapping between the virtual NIC and the host's physical adapter?
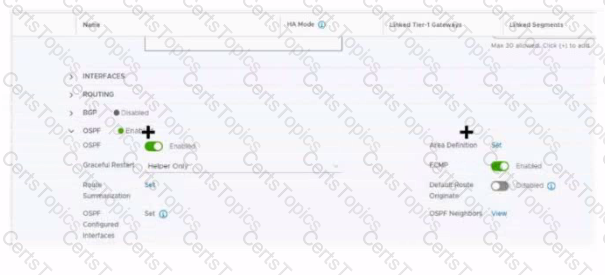
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
Which VMware GUI tool is used to identify problems in a physical network?