A security manager has been working with the executive team en long-range security goals. A primary goal for the team Is to Improve managing user risk in the organization. Which of the following ES features can help identify users accessing inappropriate web sites?
What does the Security Posture dashboard display?
Which component normalizes events?
Which of the following actions can improve overall search performance?
What is the maximum recommended volume of indexing per day, per indexer, for a non-cloud (on-prem) ES deployment?
How should an administrator add a new look up through the ES app?
Where is the Add-On Builder available from?
How is it possible to specify an alternate location for accelerated storage?
Following the Installation of ES, an admin configured Leers with the ©ss_uso r role the ability to close notable events. How would the admin restrict these users from being able to change the status of Resolved notable events to closed?
After managing source types and extracting fields, which key step comes next In the Add-On Builder?
Glass tables can display static images and text, the results of ad-hoc searches, and which of the following objects?
Which of the following is a risk of using the Auto Deployment feature of Distributed Configuration Management to distribute indexes.conf?
Following the installation of ES, an admin configured users with the ess_user role the ability to close notable events.
How would the admin restrict these users from being able to change the status of Resolved notable events to Closed?
Where is detailed information about identities stored?
Which of the following would allow an add-on to be automatically imported into Splunk Enterprise Security?
Which of the following is a key feature of a glass table?
An administrator wants to ensure that none of the ES indexed data could be compromised through tampering. What feature would satisfy this requirement?
In order to include an event type in a data model node, what is the next step after extracting the correct fields?
What should be used to map a non-standard field name to a CIM field name?
Which of the following are examples of sources for events in the endpoint security domain dashboards?
What kind of value is in the red box in this picture?
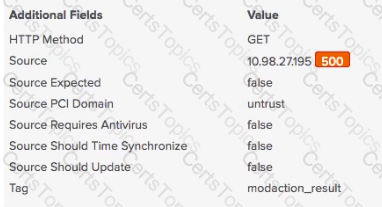
The Remote Access panel within the User Activity dashboard is not populating with the most recent hour of data. What data model should be checked for potential errors such as skipped searches?
Which setting is used in indexes.conf to specify alternate locations for accelerated storage?
Which of the following features can the Add-on Builder configure in a new add-on?
What is the bar across the bottom of any ES window?
The Add-On Builder creates Splunk Apps that start with what?
ES needs to be installed on a search head with which of the following options?
Which lookup table does the Default Account Activity Detected correlation search use to flag known default accounts?
Which data model populated the panels on the Risk Analysis dashboard?