A new FC switch has been installed into the data center. You want to disable any unsecure protocols used to access the management ports.
Which two protocols should be disabled? (Choose two.)
A SAN environment with zones containing a large number of members is experiencing hosts randomly, losing connectivity to SAN-attached storage resources. You have been asked by the customer to address this situation.
Which action should you implement to resolve this issue?
A colleague asks you if the added cost of using encrypting tape drives and sending the tapes off-site is warranted, since your IT organization already has large security investments such as firewalls and database table encryption.
What is your response?
You have a new storage array with the following drive types:
1. SAS (6 Gbps)
2. SSD
3. SATA (6 Gbps)
4. FC(4Gbps)
You need to decide which drive type to use based on speed, cost, and drive availability for your Tier 1 storage.
Which type of drive would you choose?
You have completed installing your FC SAN. When everything is powered on, numerous devices are not available. You need to verify that the devices appear within the FC fabric by accessing the appropriate FC service that provides a list of devices and their respective function.
Which server within the Fibre Channel fabric would be used to do this?
Click the Exhibit button.
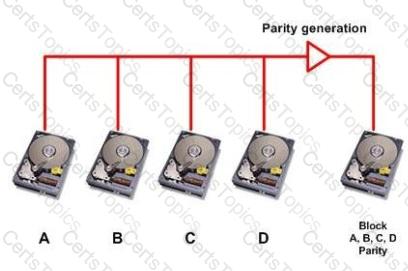
Referring to the exhibit, which RAID level is shown?
Your company uses a cryptographic key system to encrypt tapes. After several years of use and thousands of tapes shipped to off-site locations, an IT audit reveals that encryption keys have been inadvertently stored as ciphertext on file shares to which everyone in the company has read permissions.
Which response reflects industry best practice?
Click the Exhibit button.
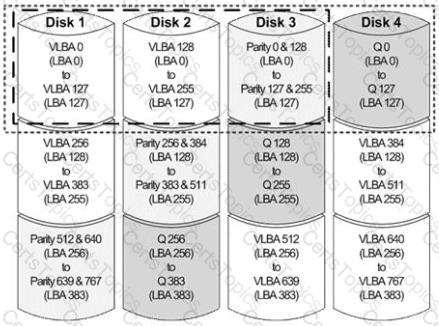
Which RAID level is shown in the exhibit?
Click the Exhibit button.
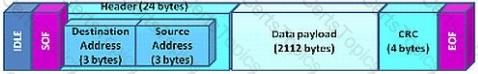
Which protocol is represented by the frame shown in the exhibit?
You need to add an iSCSI host and storage array to your environment. Your manager wants at least two options that allow all iSCSI initiators to query a central management server to locate the address of all iSCSI resources (e.g., iSCSI initiators, targets, switches, and management stations).
Which two protocol methods would be used? (Choose two.)
A storage subsystems Web browser management interface reports that the subsystem has become degraded and remotely opens a service request with the vendor. Your vendors level three storage support engineer wants to remotely access your storage subsystem for troubleshooting.
What is a SNIA Storage Security Best Current Practices solution?
A company wants to implement a database which requires a storage subsystem with no more than 2 ms write latency and 1 ms read latency.
Which type of drive would you use?
You have a file system which allows data and metadata segregation.
How should you accelerate read I/O on the file system while keeping costs low?
What is a common protocol used in cloud communications?