A company has publicly hosted web applications and an internal Intranet protected by a firewall. Which technique will help protect against enumeration?
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
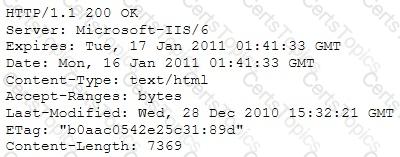
Which of the following is an example of what the engineer performed?
John the Ripper is a technical assessment tool used to test the weakness of which of the following?