Refer to the exhibit.
Which two options describe how the Update Asset and Identity Database playbook is configured? (Choose two.)
Which FortiAnalyzer feature uses the SIEM database for advance log analytics and monitoring?
Refer to the exhibits.
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Refer to the exhibit.
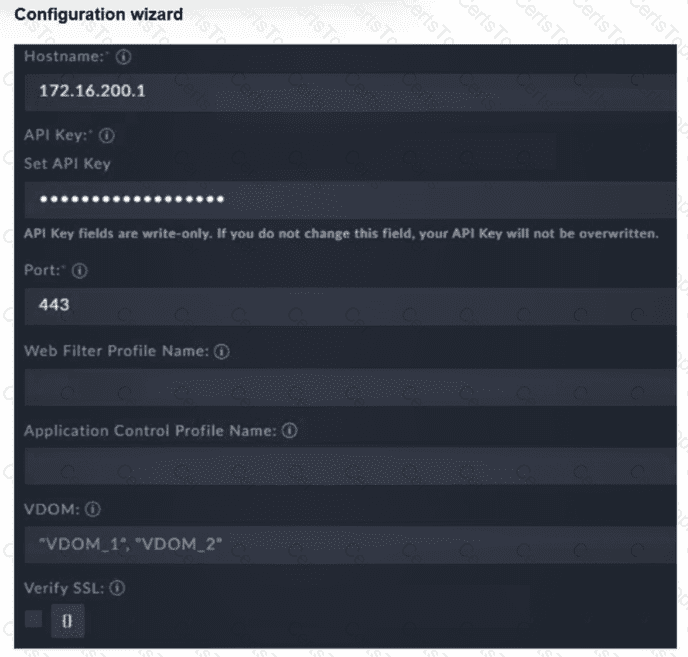
You must configure the FortiGate connector to allow FortiSOAR to perform actions on a firewall. However, the connection fails. Which two configurations are required? (Choose two answers)