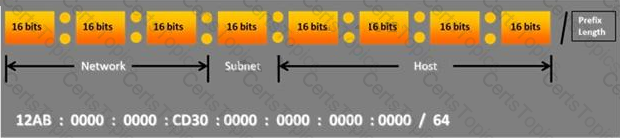
Choose the correct option to define the Prefix Length.
In the process of hacking a web application, attackers manipulate the HTTP requests to subvert the application authorization schemes by modifying input fields that relate to the user ID, username, access group, cost, file names, file identifiers, etc.
They first access the web application using a low privileged account and then escalate privileges to access protected resources. What attack has been carried out?
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, statefull firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet.
Why is that?
Which of the following statements is true about Multi-Layer Intrusion Detection Systems (mIDSs)?