You are designing a Netskope deployment for a company with a mixture of endpoints, devices, and services.
In this scenario, what would be two considerations for using IPsec as part of the design? (Choose two.)
What is a Fast Scan component of Netskope Threat Detection?
You are asked to create a Real-time Protection policy to inspect outbound e-mail for DLP violations. You must prevent sensitive e-mail from leaving the corporate mail relay.
In this scenario, which Real-time Protection policy action must be specified?
You want to verify that Google Drive is being tunneled to Netskope by looking in the nsdebuglog file. You are using Chrome and the Netskope Client to steer traffic. In this scenario, what would you expect to see in the log file?
A)

B)

C)
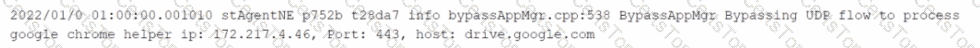
D)
