Jim’s company regularly performs backups of their critical servers. But the company can’t afford to send backup tapes to an off-site vendor for long term storage and archiving. Instead Jim’s company keeps the backup tapes in a safe in the office. Jim’s company is audited each year, and the results from this year’s audit show a risk because backup tapes aren’t stored off-site. The Manager of Information Technology has a plan to take the backup tapes home with him and wants to know what two things he can do to secure the backup tapes while in transit?
What do you call the process in which an attacker uses magnetic field over the digital media device to delete any previously stored data?
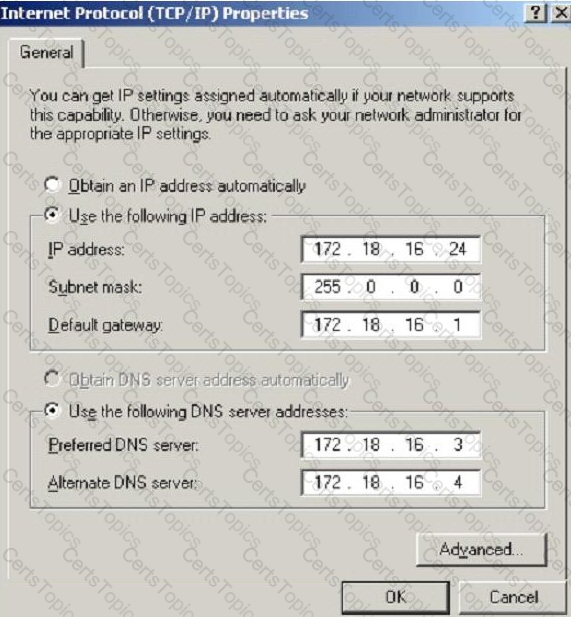
What is the CIDR from the following screenshot?
To check for POP3 traffic using Ethereal, what port should an investigator search by?