According to Microsoft’s official Defender for Identity deployment documentation, setting up Microsoft Defender for Identity (MDI) on an on-premises domain controller (DC) such as DC1 requires a specific sequence of steps. MDI monitors and protects Active Directory from advanced threats by using sensors installed directly on domain controllers.
The correct sequence is as follows:
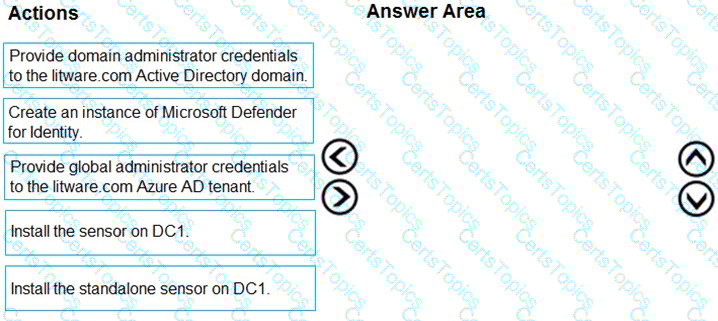
1️⃣ Provide global administrator credentials to the Azure AD tenant.
Microsoft Defender for Identity is created and managed in the Microsoft 365 Defender portal or Microsoft Security portal, which requires global administrator permissions to provision the MDI instance and connect it to the Azure AD tenant.
2️⃣ Create an instance of Microsoft Defender for Identity.
You must create an MDI instance in the portal before deploying any sensors. This instance defines your Defender for Identity workspace and generates the configuration package that sensors will later use to connect to the cloud service.
3️⃣ Provide domain administrator credentials to the on-premises Active Directory domain.
Domain admin credentials are required for the sensor installation because the sensor must access the domain controller’s security logs, event logs, and directory services to monitor authentication traffic and suspicious activities.
4️⃣ Install the sensor on DC1.
Since DC1 is a domain controller connected directly to the internet, the standard sensor (not the standalone sensor) is installed directly on it. The standalone sensor is used only when you do not want to install the sensor directly on a DC. The sensor automatically connects to the created MDI instance and begins collecting telemetry for detection.
This sequence aligns with Microsoft Defender for Identity deployment guidance, ensuring secure onboarding of DC1 while maintaining the principle of least privilege and meeting the business requirement to protect all domain controllers.
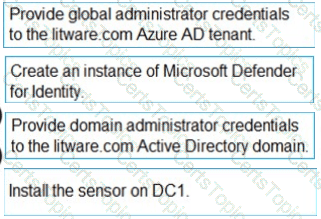
✅ Final Order:
Create instance of Microsoft Defender for Identity →
Provide domain administrator credentials →
Install the sensor on DC1.