Huawei Related Exams
H12-831_V1.0 Exam







In the figure, an administrator needs to enable MPLS LDP on R1 to R4. Which of the following configurations of R1 is correct?

A network engineer checks LLDP neighbor information on R1. The output is shown below.
Which of the following statements are true?
LLDP Output:
yaml
CopyEdit
------------------------------------------------
GE0/0/0 has 1 neighbor(s):
Neighbor index: 1
Chassis type: MAC Address
Chassis ID: faed-ad04-0010
Port ID subtype: Interface Name
Port ID: GE0/0/0
System name: R2
System description: Huawei YunShan OS
Version 1.22.01 (AR8000 V100R002C200)
Copyright (C) 2021-2022 Huawei Technologies Co., Ltd.
HUAWEI AR8140-12G10XG
System capabilities supported: bridge router
System capabilities enabled: bridge router
Management address type: IPv4
Management address: 192.168.1.1
Expired time: 107s
As shown in the figure, an administrator enables port isolation on the switch’s interfaces connected to terminals.
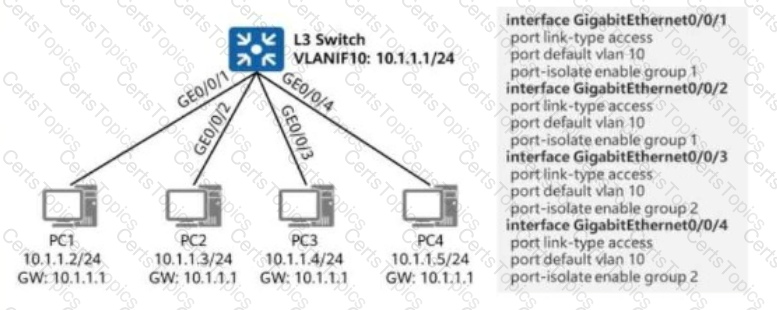
In this scenario, which of the following IP addresses cannot be pinged from PC1?