CyberArk Related Exams
CPC-SEN Exam







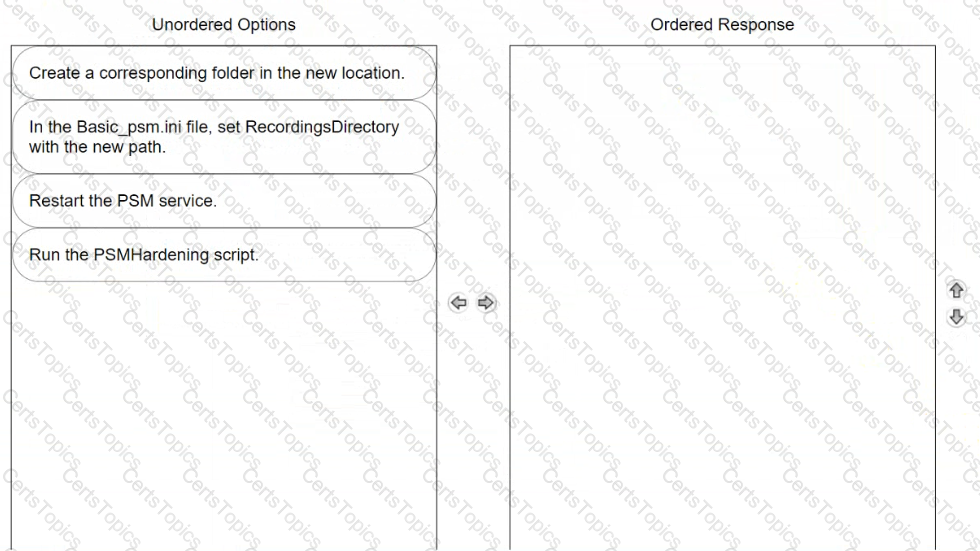
You want to change the default PSM recordings folder path on the Privilege Cloud Connector Arrange the steps to accomplish this in the correct sequence.
During CPM hardening, which locally created users are granted Logon as a Service rights in the local group policy? (Choose 2.)
Which browser is supported for PSM Web Connectors developed using the CyberArk Plugin Generator Utility (PGU)?