Verified By IT Certified Experts
CertsTopics.com Certified Safe Files
Up-To-Date Exam Study Material
99.5% High Success Pass Rate
100% Accurate Answers
Instant Downloads
Exam Questions And Answers PDF
Try Demo Before You Buy






An outside organization has reported to the Chief Information Officer (CIO) of a company that it has received attack from a Linux system in the company’s DMZ. Which of the following commands should an incident responder use to review a list of currently running programs on the potentially compromised system?
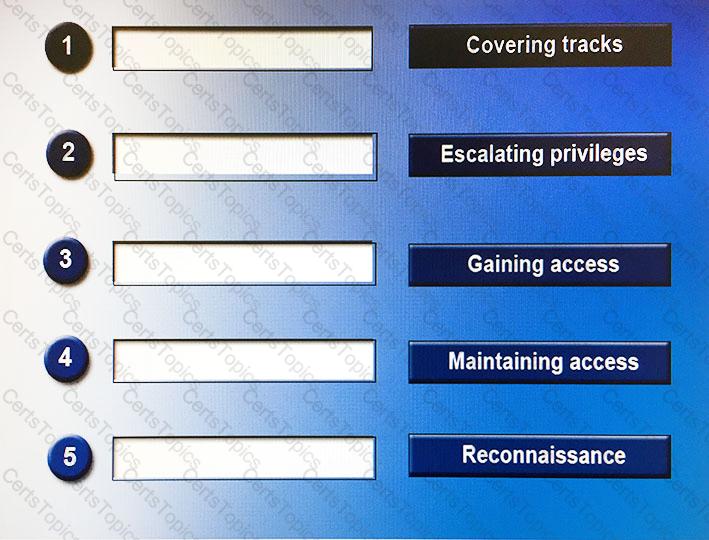
When perpetrating an attack, there are often a number of phases attackers will undertake, sometimes taking place over a long period of time. Place the following phases in the correct chronological order from first (1) to last (5).