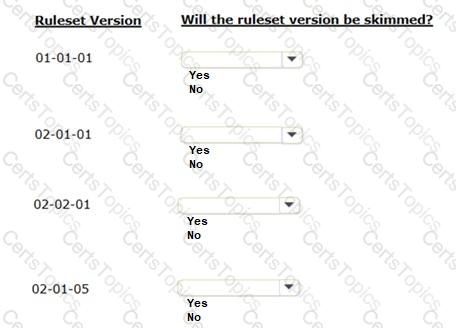
The current version of an application lists ABC:02-02 as an application ruleset. The ruleset versions listed in the Answer Area are also present on the system.
In the Answer Area, identify the ruleset versions that the skim operation considers when you perform a major version ruleset skim on ruleset ABC.
A hospital uses a case type to manage the treatment of patients visiting the Emergency Room (ER). Cases are created when the patient checks in at the registration desk, and are resolved when the patient is released from the hospital. Stakeholders identify the following security requirements for the case type.
♦Patients access cases on a read-only basis.
♦Patients can only access their own cases.
♦Doctors and nurses can modify cases throughout the case life cycle.
♦Only doctors are allowed to write prescriptions.
Which configuration allows doctors and nurses to modify cases while complying with all identified security requirements?
In a hiring case type, only HR Managers should have read access to a candidate's reference letter attachment. Which two tasks are used to fulfill this requirement? (Choose Two)
Your application is deployed to the cloud. A data source outside your application populates a data page by using your data access pattern configuration. You receive complaints that the system takes a long time to fetch data each time the case worker accesses information for a different customer.
Which approach solves this performance issue?
Drag each security solution on the left to its appropriate use case.

In the Answer Area, drag each mobile application solution on the left to the correct scenario.
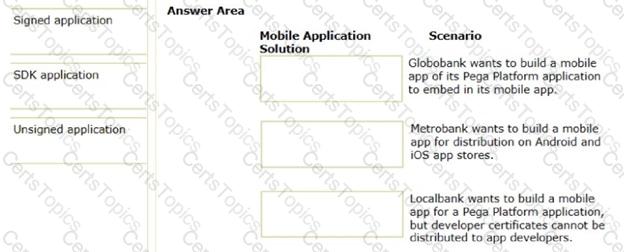
Which two tasks are required to build a mobile app from a Pega Platform application? (Choose Two)
A view has a part number field that requires the first two characters are letters, and the last four are digits (for example, AB1234).
How do you ensure that the correct pattern is entered when the user exits the field?
A travel reservation servicing case includes a service level for responding to requests. The service level intervals vary according to passenger status, class of service, and fare type.
Which implementation satisfies this requirement?
A global application with infrastructure nodes located throughout the world requires certain operations to start executing at midnight GMT.
Select two possible designs for this use case. (Choose Two)
Which two use cases correctly describe controlling access to an attachment category? (Choose Two)
Which statement regarding managing encrypted data in Pega Platform is true?