Which two Azure resources can a network security group (NSG) be associated with? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
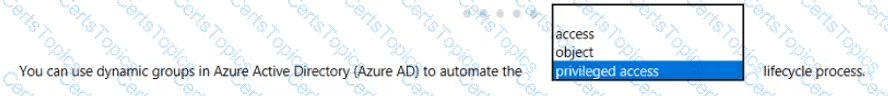
Select the answer that correctly completes the sentence.
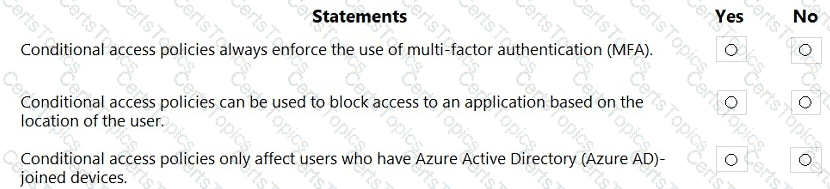
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
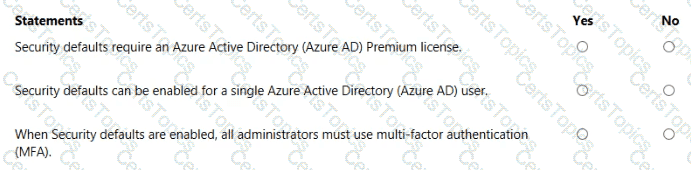
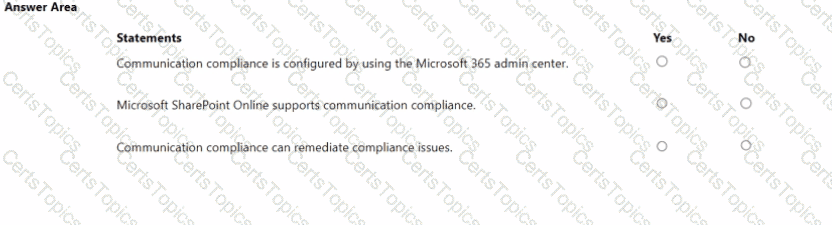
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

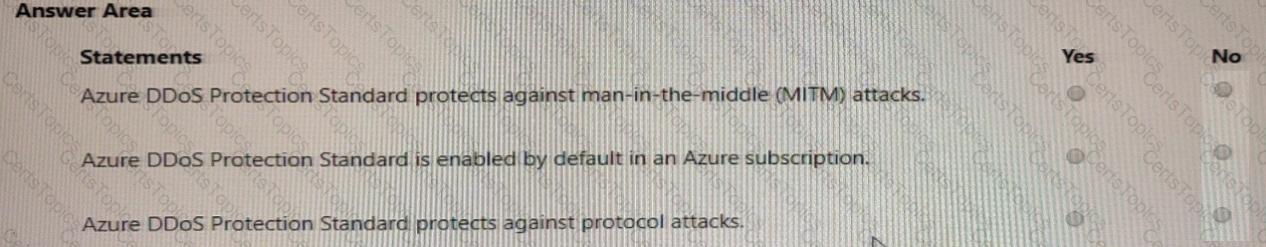
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.
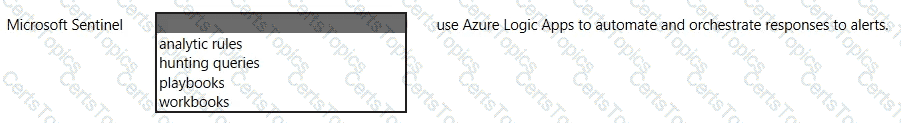
Which two actions can you perform by using Azure Key Vault? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you use to view the Microsoft Secure Score for Devices?
Select the answer that correctly completes the sentence.

Which solution performs security assessments and automatically generates alerts when a vulnerability is found?
Select the answer that correctly completes the sentence.

What can you specify in Microsoft 365 sensitivity labels?
What can you use to protect against malicious links sent in email messages, chat messages, and channels?
Select the answer that correctly completes the sentence.

You have an Azure subscription that contains multiple resources.
You need to assess compliance and enforce standards for the existing resources.
What should you use?
What is a function of Conditional Access session controls?
When security defaults are enabled for an Azure Active Directory (Azure AD) tenant, which two requirements are enforced? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.

Which service should you use to view your Azure secure score? To answer, select the appropriate service in the answer area.
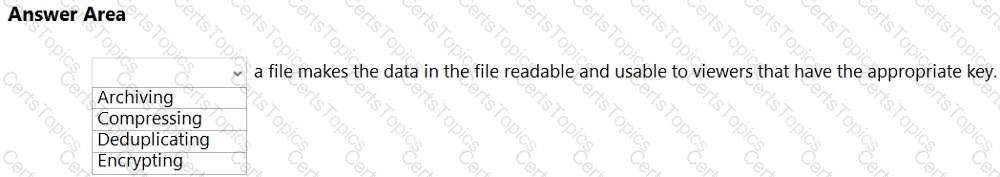
Select the answer that correctly completes the sentence.

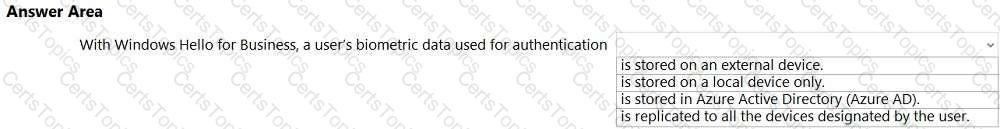
Select the answer that correctly completes the sentence.
What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution.
NOTE: Each correct selection is worth one point.
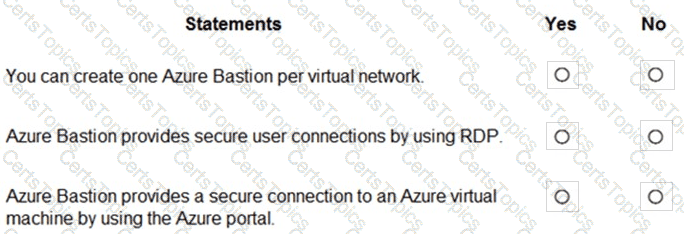
To which type of resource can Azure Bastion provide secure access?
Select the answer that correctly completes the sentence.
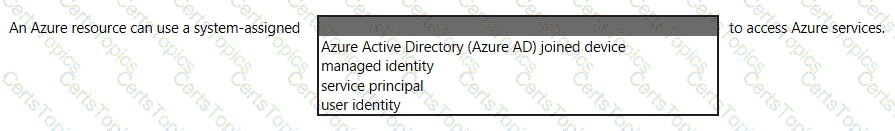
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.
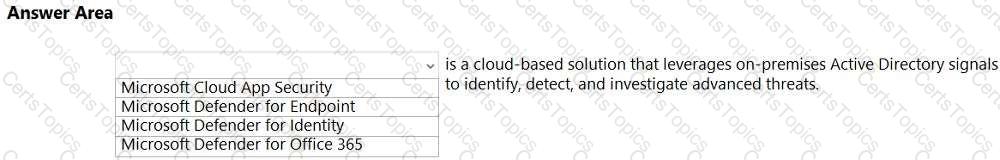
Select the answer that correctly completes the sentence.

Which statement represents a Microsoft privacy principle?
What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface?
Select the answer that correctly completes the sentence.
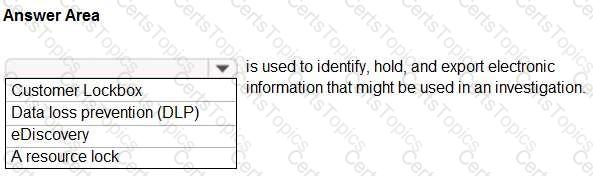
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What is a use case for implementing information barrier policies in Microsoft 365?
Select the answer that correctly completes the sentence.
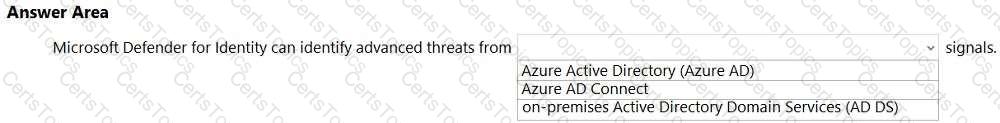
What are customers responsible for when evaluating security in a software as a service (SaaS) cloud services model?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
When you enable Azure AD Multi-Factor Authentication (MFA), how many factors are required for authentication?
Select the answer that correctly completes the sentence.

You have an Azure subscription.
You need to implement approval-based, tiProme-bound role activation.
What should you use?
Select the answer that correctly completes the sentence.
Which two types of devices can be managed by using Endpoint data loss prevention (Endpoint DLP)? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
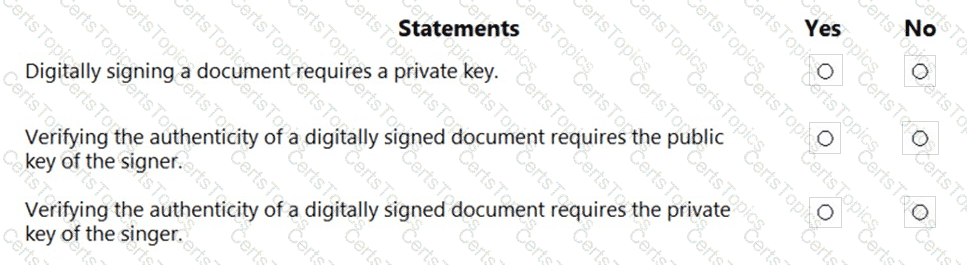
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems?
For each of the following statement, select Yes if the statement is true Otherwise, select No.
NOTE: Each connect selection a worth one point.
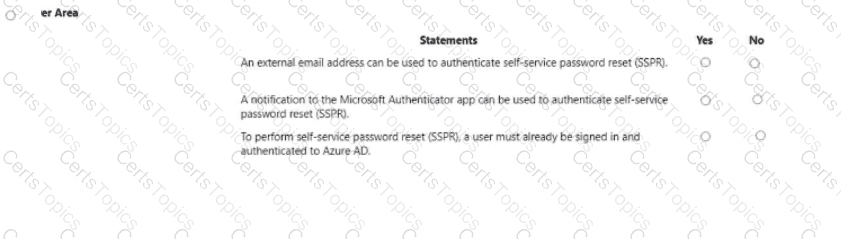
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
In a Core eDiscovery workflow, what should you do before you can search for content?
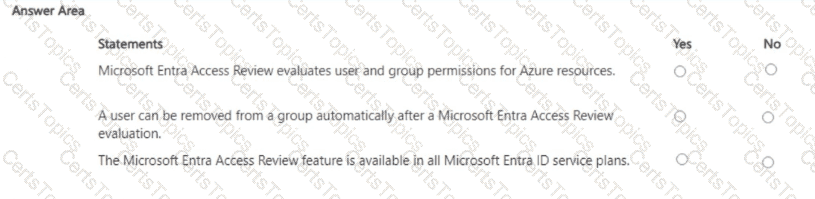
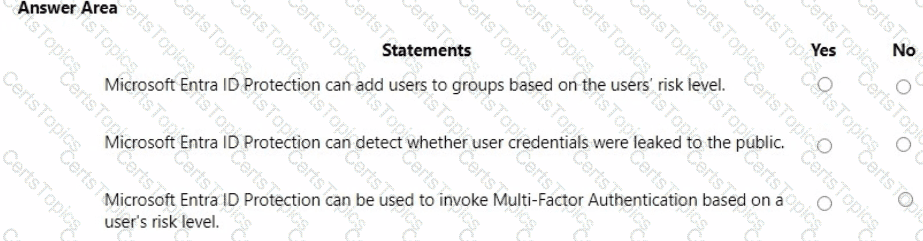
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Select the answer that correctly completes the sentence.

You plan to move resources to the cloud.
You are evaluating the use of Infrastructure as a service (laaS),
Platform as a service (PaaS), and Software as a service (SaaS) cloud models.
You plan to manage only the data, user accounts, and user devices for a cloud-based app.
Which cloud model will you use?
Select the answer that correctly completes the sentence.

Select the answer that correctly completes the sentence.

What can you use to provide a user with a two-hour window to complete an administrative task in Azure?
What Microsoft Purview feature can use machine learning algorithms to detect and automatically protect sensitive items?
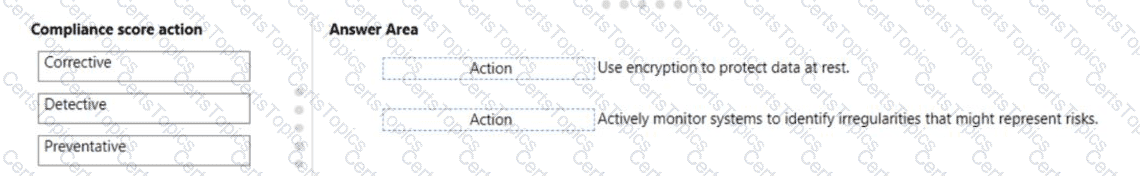
Match the types of compliance score actions to the appropriate tasks.
To answer. drag the appropriate action type from the column on the left to its task on the right. Each type may be used once. more than once, or not at all.
NOTE: Each correct match is worth one point.
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?