Refer to the exhibit.

The wireless station with MAC address 5a:29:94:87:f7:b8 has made multiple attempts to connect to the CORP.DATA SSID Despite client-association-failure event logs the wireless station connects on the final attempt
Why did the wireless station fail to connect initially?
Refer to the exhibit.
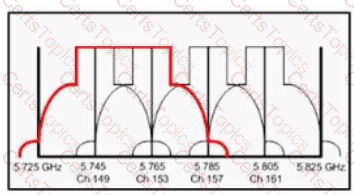
What does the red line represent?
Which action does a wireless client or the access point take when the wireless client moves away from an associated AP until the signal drops?
Which two management services support connecting FortiAPs to the FortiPresence cloud? (Choose two.
Refer to the exhibit.
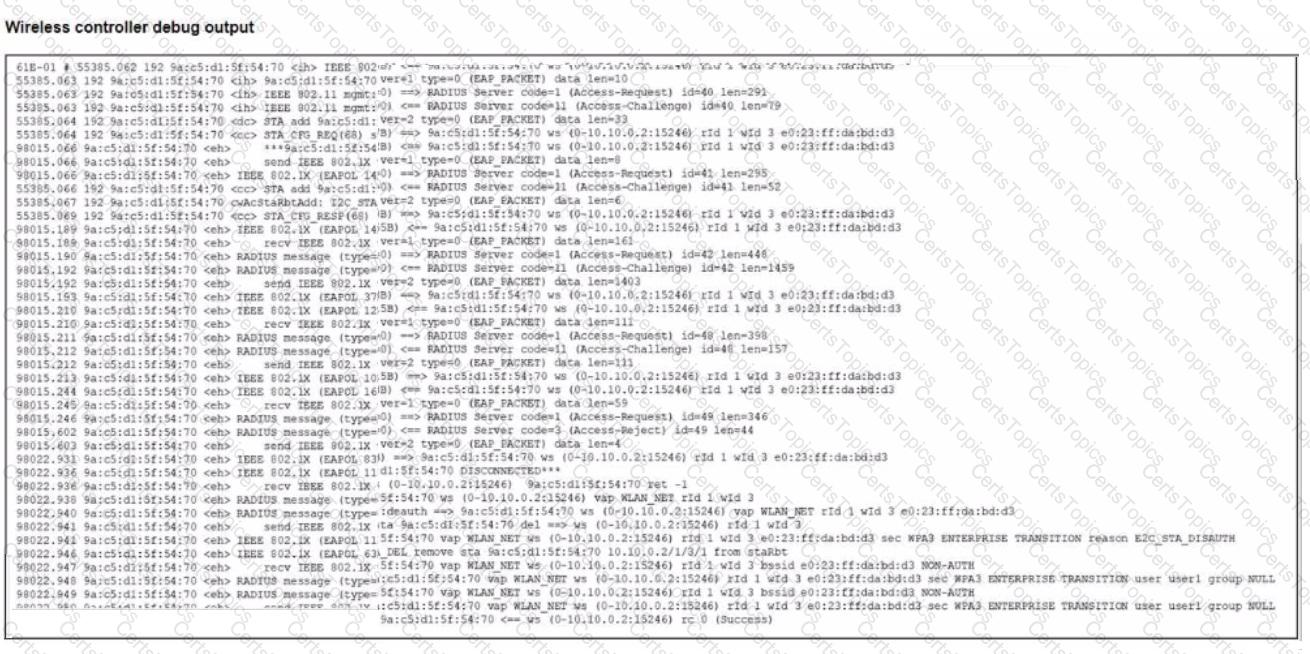
The wireless client connects to the wireless network on WLAN_NET tunnel mode interface The exhibit stows the client exchange communication with the wireless controller and the RADIUS server
Which two issues can you observe in the wireless station debug outputs (Choose two.)
Refer to the exhibit.
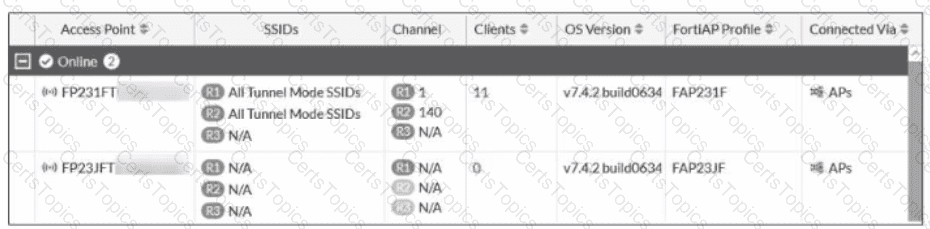
An administrator authorizes two FortiAP devices connected to this wireless controller However, one FortiAP is not able to broadcast the SSIDs. What must the administrator do to fix the issue?
Refer to the exhibit.
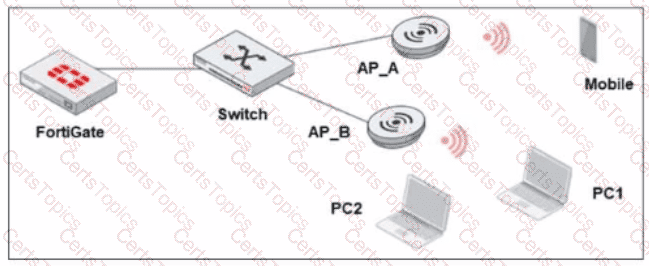
A new security policy is made by the IT department to prevent direct communication between wireless stations There is one SSID configured in bridge mode Which statement is correct as a plan of action to update the wireless network configuration?
An IT department must provide wireless security to employees connected over remote hortiAP devices who must access corporate resources at the mam office Which action must the IT department take to enforce security policies for all wireless stations accessing corporate resources across all remote locations?
Which benefit does 802.1X authentication offer when securing a wireless network?