Comprehensive Detailed Step by Step Explanation from all your Knowledge and Guides availableExhibit Analysis:
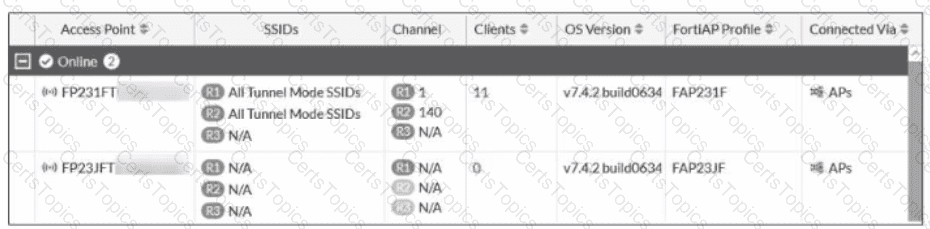
The screenshot displays two FortiAPs (FP231FT and FP23JFT) in the wireless controller’s managed APs list.
Both APs are online and connected via APs.
FP231FT shows active SSIDs (“All Tunnel Mode SSIDs”) and has 11 clients connected.
FP23JFT shows “N/A” for all SSIDs and “0” clients.
Diagnosis:
“N/A” for SSIDs on FP23JFT clearly indicates it is not broadcasting any SSID.
Both APs are running the same OS version and have their respective FortiAP profiles assigned.
Evaluating the Options:
A. Enable the radios on the FAP23JF FortiAP profile.
Correct: If the radios (2.4GHz/5GHz) are disabled in the FortiAP profile, the AP will not broadcast any SSID, resulting in “N/A” and “0 clients”. This is a common issue seen in FortiOS Wireless LAN management.
This matches the symptom, as the AP is online (communicating with the controller), but has no active radio (hence, no SSID is broadcasted).
B. Replace the FortiAP device model to match the other device.
Incorrect. FortiOS supports different models in the same deployment, as long as the correct profile is applied.
C. Disable the override setting on the FortiAP that is preventing it from broadcasting SSIDs.
Misleading. Unless an override has specifically disabled SSID broadcasting, this is not directly indicated by the screenshot. Usually, radio disabled at profile is the root cause.
D. Assign the FAP231F FortiAP profile to the problematic FortiAP device.
Incorrect. The correct profile (FAP23JF) is already assigned to FP23JFT; assigning a mismatched profile can cause more issues and is not best practice.
Guide Reference & Reasoning:
FortiOS Administration Guide – Wireless Section:
When an AP is online but SSIDs are not broadcasted and “N/A” appears for radio slots, it strongly points to the radios being disabled in the FortiAP profile (see Wireless Controller > Managed FortiAPs).
The guide explains that “If the radios are disabled in the profile, the AP will not broadcast any SSID. To resolve, enable the radios (2.4GHz, 5GHz) in the FortiAP profile and reapply or reboot the AP”.
FortiAP Profile Settings:
Go to WiFi & Switch Controller > FortiAP Profiles.
Edit the FAP23JF profile.
Check both “Radio 1” and “Radio 2” (enable if disabled).
Save the changes and ensure the profile is pushed to the AP.
Typical Steps to Fix:
Log into the FortiGate.
Navigate to WiFi & Switch Controller > FortiAP Profiles.
Edit the FAP23JF profile.
Under the radio settings, ensure both radios are set to “Enable”.
Apply the changes.
The AP will now broadcast the SSIDs as configured.
Summary:
The problem is caused by disabled radios in the FAP23JF FortiAP profile. Enabling the radios in the profile will allow the AP to start broadcasting SSIDs.
Final Answer: A. Enable the radios on the FAP23JF FortiAP profile.