Before starting a Dell NetWorker recovery, the administrator needs to verify that the DDBoost user is correctly configured in both the production and Dell PowerProtect Cyber Recovery environments.
What must be confirmed about the DDBoost user to ensure a successful Dell NetWorker recovery?
What does Dell Technologies recommend before defining Dell PowerProtect Cyber Recovery policies?
To protect the production data with Dell PowerProtect Cyber Recovery, which statement describes a correct requirement when planning a vault environment?
Which describes the best use of Dell PowerProtect Data Domain in an isolated clean room?
Which is the best practice when securing PowerProtect Data Domain in Dell PowerProtect Cyber Recovery vault?
What should be the consideration for scratch storage when sizing a CyberSense server?
What is used to confirm the CyberSense Server is ready for software install?
DRAG DROP
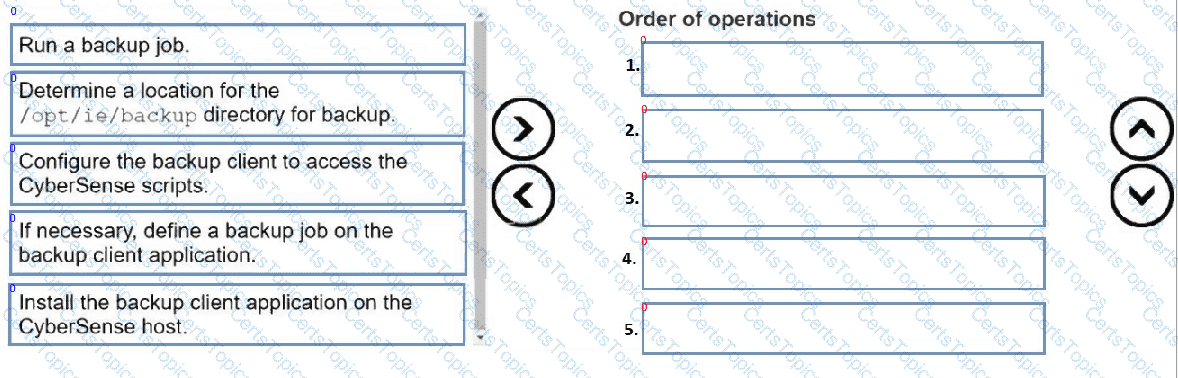
Put the following steps in the correct order to back up the Index Engines CyberSense configuration files:
What component orchestrates synchronization, locking, and recovery operations in the vault environment?
What are the two types of alerts in the CyberSense Alerts dashboard? (Choose two.)
Which two options correctly describe how you can connect from the vault to another environment? (Choose two.)