A systems administrator is having issues with a third-party API endpoint. The administrator receives the following output:
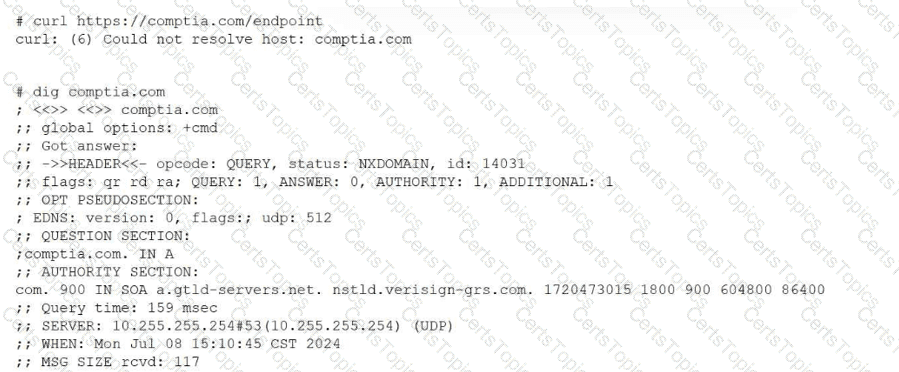
Which of the following actions should the administrator take to resolve the issue?
A systems administrator receives reports from users who are having issues while trying to modify newly created files in a shared directory. The administrator sees the following outputs:
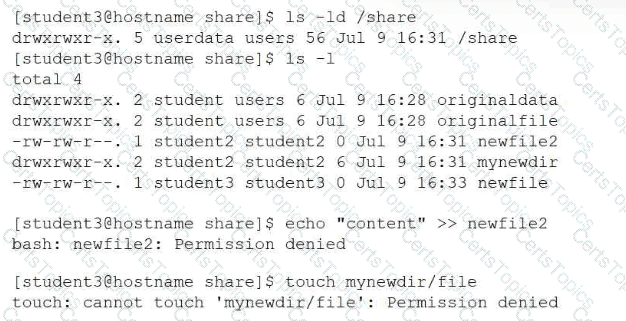
Which of the following provides the best resolution to this issue?
A systems administrator receives reports about connection issues to a secure web server. Given the following firewall and web server outputs:
Firewall output:
Status: active
To Action From
443/tcp DENY Anywhere
443/tcp (v6) DENY Anywhere (v6)
Web server output:
tcp LISTEN 0 4096 *:443 :
Which of the following commands best resolves this issue?
Which of the following commands should a Linux administrator use to determine the version of a kernel module?
An administrator receives the following output while attempting to unmount a filesystem:
umount /data1: target is busy.
Which of the following commands should the administrator run next to determine why the filesystem is busy?
Which of the following is a characteristic of Python 3?
Which of the following best describes journald?
Which of the following can reduce the attack surface area in relation to Linux hardening?
Which of the following is the main reason for setting up password expiry policies?
A technician wants to temporarily use a Linux virtual machine as a router for the network segment 10.10.204.0/24. Which of the following commands should the technician issue? (Select three).
A Linux administrator wants to make the enable_auth variable set to 1 and available to the environment of subsequently executed commands. Which of the following should the administrator use for this task?
Which of the following Ansible components contains a list of hosts and host groups?
Which of the following is a reason multiple password changes on the same day are not allowed?
A Linux user frequently tests shell scripts located in the /home/user/scripts directory. Which of the following commands allows the user to run the program by invoking only the script name?
A systems administrator is writing a script to analyze the number of files in the directory /opt/application/home/. Which of the following commands should the administrator use in conjunction with ls -l | to count the files?
A systems administrator needs to integrate a new storage array into the company's existing storage pool. The administrator wants to ensure that the server is able to detect the new storage array. Which of the following commands should the administrator use to ensure that the new storage array is presented to the systems?
Users cannot access a server after it has been restarted. At the server console, the administrator runs the following commands;
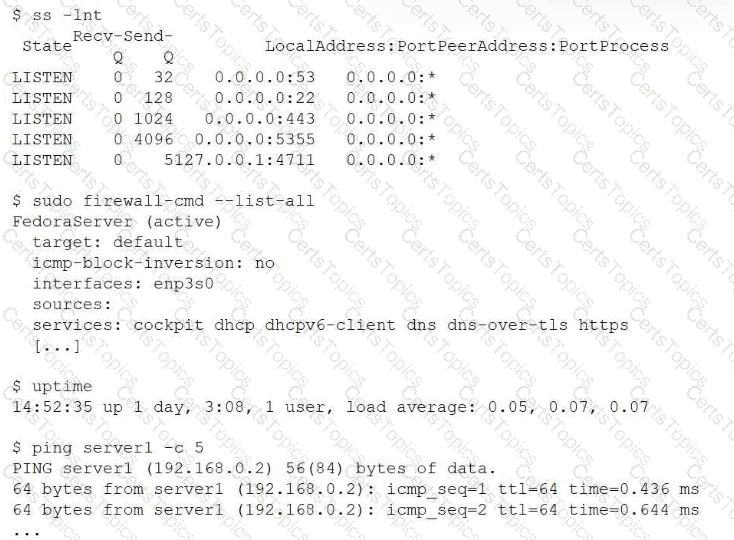
Which of the following is the cause of the issue?
Which of the following utilities supports the automation of security compliance and vulnerability management?
An administrator needs to verify the user ID, home directory, and assigned shell for the user named "accounting." Which of the following commands should the administrator use to retrieve this information?
To perform a live migration, which of the following must match on both host servers? (Choose two)
An administrator wants to search a file named myFile and look for all occurrences of strings containing at least five characters, where characters two and five are i, but character three is not b. Which of the following commands should the administrator execute to get the intended result?
A Linux administrator attempts to log in to a server over SSH as root and receives the following error message: Permission denied, please try again. The administrator is able to log in to the console of the server directly with root and confirms the password is correct. The administrator reviews the configuration of the SSH service and gets the following output:
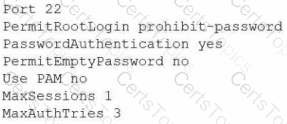
Based on the above output, which of the following will most likely allow the administrator to log in over SSH to the server?
A systems administrator wants to review the amount of time the NetworkManager service took to start. Which of the following commands accomplishes this goal?
A Linux administrator needs to securely erase the contents of a hard disk. Which of the following commands is the best for this task?
A Linux administrator is testing a web application on a laboratory service and needs to temporarily allow DNS and HTTP/HTTPS traffic from the internal network. Which of the following commands will accomplish this task?
Which of the following describes how a user's public key is used during SSH authentication?