Which IEEE standard is commonly used at the data link layer for an access network, in an IoT environment?
Company ABC is using an Ethernet virtual circuit as its provider’s DCI solution. A goal is to reduce the time to detect the link failure. Which protocol accomplishes this goal?
How must queue sizes be designed to ensure that an application functions correctly?
You are presented with requirements to design a development, testing and production environments. These environment should communicate with each other, yet they should be kept as separate failure domains. Which routing protocol should be configured on the links between the networks to support the design requirements?
In a VPLS design solution, which situation indicates that BGP must be used instead of LDP in the control plane?
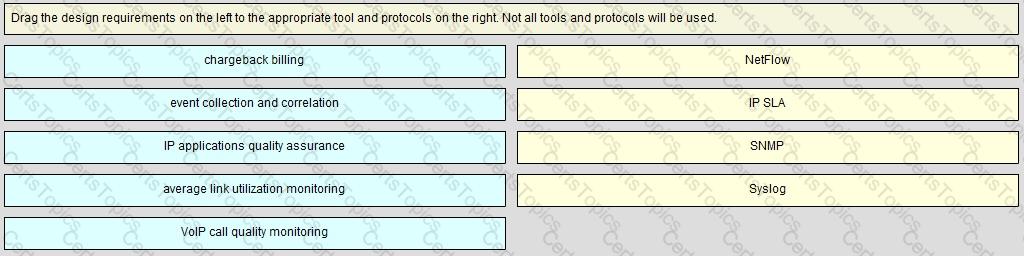
Refer to the exhibit.
 As part of a redesign project, you must predict multicast behavior. What is the resultant multicast traffic receiving on the shared tree( , G), if it is received on the LHR interface indicated?
As part of a redesign project, you must predict multicast behavior. What is the resultant multicast traffic receiving on the shared tree( , G), if it is received on the LHR interface indicated?
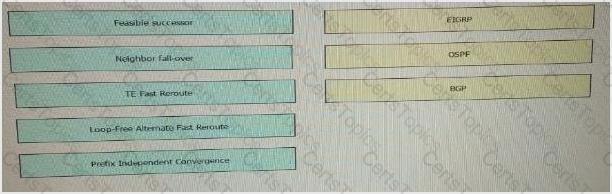
Drag the fast Reroute mechanism on the left and drop it onto the corresponding routing protocol on the right
Which markup language is used to format Ansible's playbook?
A network designer wants to improve a company network design due to multiple network crashes. Which technology would allow for the restore of a network connection without informing the Layer 3 protocol?
Which two SAN designs appropriate to support large-scale SAN environments? (Choose two)
What is an advantage of placing the IS-IS flooding domain boundary at the core Layer in a three-layer hierarchical network?
Which two are IoT sensor-specific constraints? (Choose two)
What is an effect of using ingress filtering to prevent spoofed addresses on a network design?
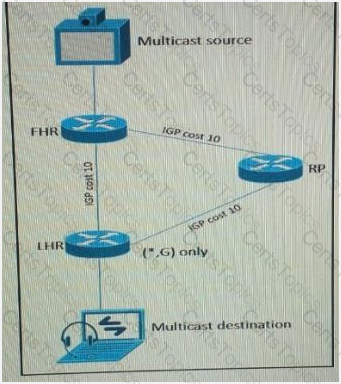
Refer to the exhibit.
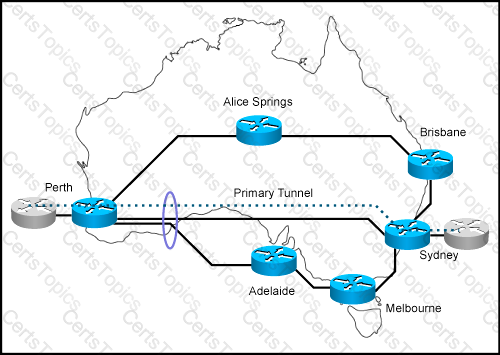
You are designing MPLS-TE for this network. The links form Perth to Sydney and from Perth to Adelaide share the same optical fiber in one given segment. Which feature should you implement to eliminate the risk that a backup tunnel is installed over the same optical fiber as the primary one?
Which open source message broker is in the Cisco Cloud Center?
Refer to the exhibit.
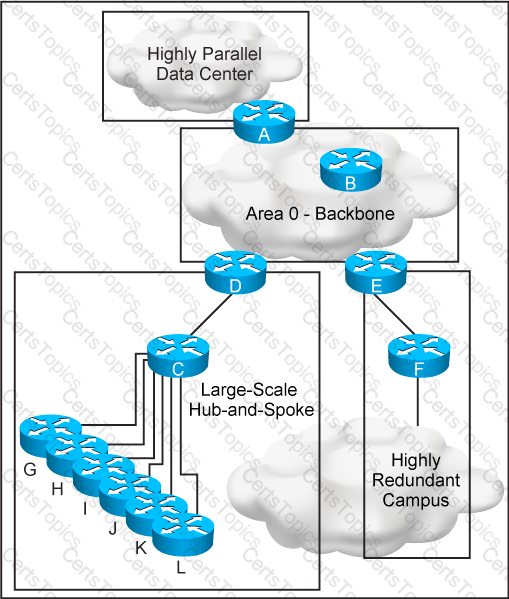
This new OSPF network has four areas, but the hub-and-spoke area experiences frequent flapping. In order to fix this design failure, which two mechanisms can you use to isolate the data center area from the hub-and-spoke area without losing Ip connectivity? (Choose two)
Which two components are the responsibility of the customers in a platform as a Service offering? (Choose two)
What are three common objectives of customers using multiple cloud providers? (Choose three )
Which two functions are performed at the distribution layer of the three-layer hierarchical network design model? (Choose two).
Which two design aspects should a metro service provider consider when planning to deploy REP for his backbone? (Choose two.)
Which three options are IS-IS design considerations when connecting two Layer 3 switches directly using a 10 GBASE-T cabling and formatting an IS-IS neighbor adjacency?
A new video multicast application is deployed in the network. The application team wants to use the 239.0.0.1 multicast group to stream the video to users. They want to know if this choice will impact the existing multicast design. What impact will their choice have on the existing multicast design?
Refer to the exhibit.
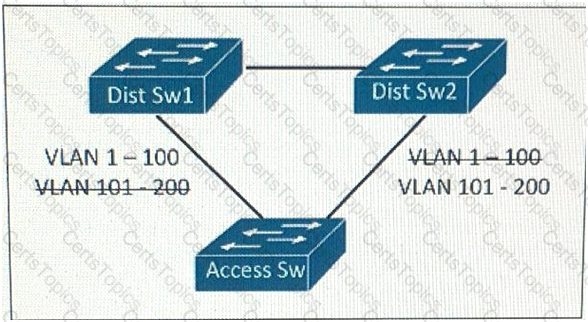
This layer 2 network is expected to add 150 VLANS over the next year, In addition to the existing 50 VLANs within the network which STP types will support this design requirement the least amount of CPU resource and achieving load balancing?
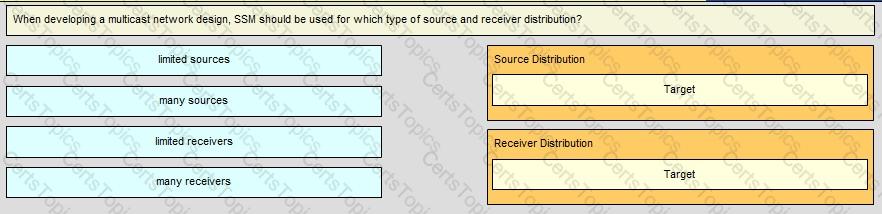
Across a large WAN network, there will be new video traffic being distributed from a single source at any given time however, the video source might originate from different parts of the multicast domain at different times . Which multicast technology provides for this multicast traffic to be distributed with optimal path selection to the source?
A data center provider has designed a network using these requirements
Two data center sites are connected to the public internet
Both data centers are connected to different Internet providers
Both data centers are also directly connected with a private connection for the internal traffic can also be at this direct connection The data center provider has only /19 public IP address block
Under normal conditions, Internet traffic should be routed directly to the data center where the services are located. When one Internet connections fails to complete traffic for both data centers should be routed by using the remaining Internet connection in which two ways can this routing be achieved? (Choose two)
Which two options are potential problems with route aggregation? (Choose two)
Your client is considering acquiring a new IPv6 address block so that all Ethernet interfaces on the network receive addresses based on their burned-in hardware addresses, with support for 600 VLANs. Which action do you recommend?
You are consultant network designer for a large GET VPN deployment for a large bank with International coverage. Between 1800 and 2000 remote locations connect to the central location through four hubs using an MPLS backbone and using two keys servers. The bank is concerned with security and replay attacks. Which two actions should you use to tune the GET VPN to meet the bank requirements? (Choose two)
Which aspect is a significant disadvantage of containers?
Which reason prevents a designer from using a GDOI-based VPN to secure traffic that traverses the Internet?
When is it required to leak routes into an IS-IS level 1 area?
Which option describes a design benefit of root guard?
The service provider that you work for wants to offer IPv6 internet service to its customers without upgrading all of its access equipment to support IPv6, which transition technology do you recommend?
.which two options are benefits of using Topology Independent Loop-Free Alternate in WAN design? (Choose two)