A network engineer must integrate VMware vCenter cluster with Cisco ACI. The requirement is for the management traffic of the hypervisors and VM controllers to use the virtual switch associated with the Cisco Application Policy. The EPG called "Vmware-MGMT" with VLAN 300 has been created for this purpose. Which set of steps must be taken to complete the configuration?
An engineer wants to filter the System Faults page and view only the active faults that are present in the Cisco
ACI fabric. Which two lifecycle stages must be selected for filtering? (Choose two.)
An engineer must configure a service graph for the policy-based redirect to redirect traffic to a transparent firewall. The policy must be vendor-agnostic to support any firewall appliance, Which two actions accomplish these goals? (Choose two.)
Refer to the exhibit.
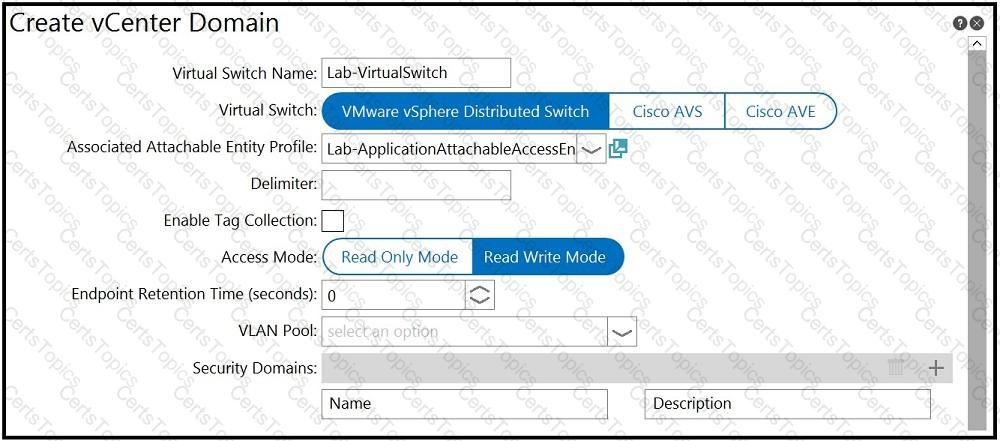
An engineer is integrating a VMware vCenter with Cisco ACI VMM domain configuration. ACI creates port-group names with the format of “Tenant | Application | EPG”. Which configuration option is used to generate port groups with names formatted as “Tenant=Application=EPG”?
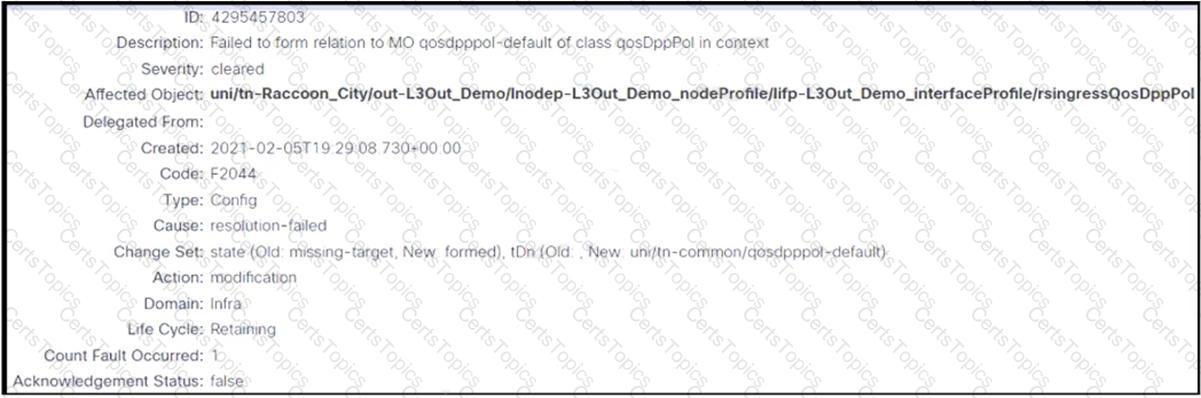
Refer to the exhibit. An engineer configures an L3Out but receives the error presented. Which action clears the fault?
Refer to the exhibit.
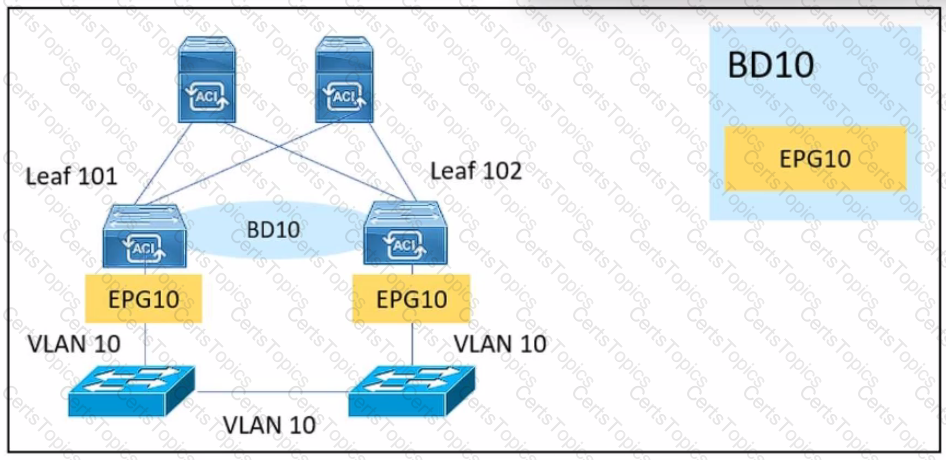
An engineer is implementing a BPDU filter on external switch interfaces That face the Cisco ACI fabric to prevent excessive TCNs from impacting the fabric. Which Configuration must be applied on Cisco ACI to avoid a Layer 2 loop?
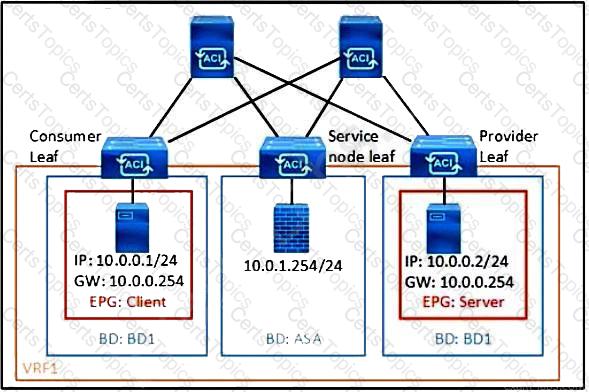
Refer to the exhibit. What must be configured in the service graph to redirect HTTP traffic between the EPG client and EPG server to go through the Cisco ASA firewall?
Engineer must configure SNMP inside a Cisco ACI fabric. The engineer has created an SNMP Policy, called SNMP-policy and an SNMP Monitoring Group called SNMP-group1 that Contains five trap receivers. Which configuration set completes the configuration?
Refer to the exhibit.
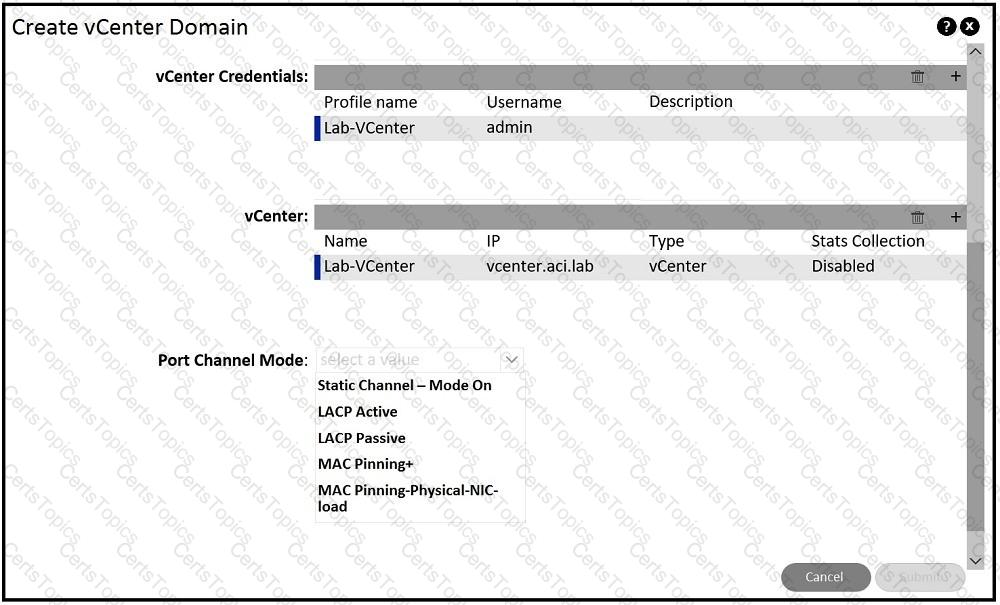
An engineer is implementing Cisco ACI – VMware vCenter integration for a blade server that lacks support of bonding. Which port channel mode results in “route based on originating virtual port” on the VMware VDS?
An engineer deploys a two-pod Cisco ACI Multi-Pod environment. Why should no more than two Cisco APIC controllers be deployed in the same pod?
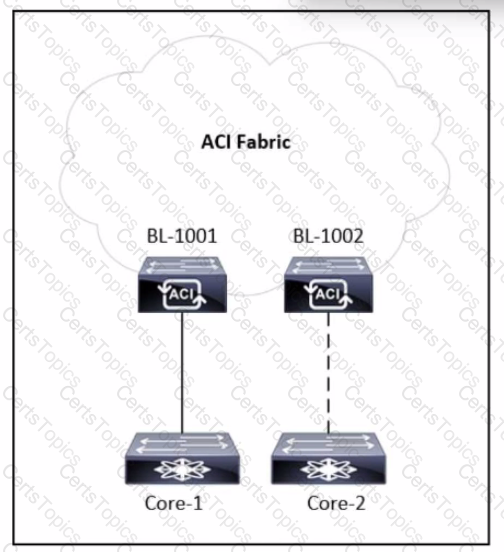
Refer to the exhibit. A tenant is configured with a single L30ut and a single-homed link to the core router called Core-1. An engineer must add a second link to the L30ut that connects to Core-2 router. Which action allows the traffic from Core-2 to BL-1002 to have the same connectivity as the traffic from Core-1 to BL-1001?
Which endpoint learning operation is completed on the ingress leaf switch when traffic is received from a Layer 3 Out?
An organization has encountered many STP-related issues in the past due to failed hardware components. They are in the process of long-term migration to a newly deployed ACI fabric. Senior engineers are worried that spanning-tree loops in the existing network may be extended to the ACI fabric. Which feature must be enabled on the ACI leaf ports to protect the fabric from spanning-tree loops?
An engineer must allow multiple external networks to communicate with internal ACI subnets. Which action should the engineer take to assign the prefix to the class ID of the external Endpoint Group?
The engineer notices frequent MAC and IP address moves between different leaf switch ports. Which action prevents this problem from occurring?
A Cisco ACI fabric is integrated with a Cisco ASA firewall using a service graph under the tenant called Operations. The fabric must permit the firewall used on tenant Operations to be referenced by the tenant called Management. Which export action must be used to accomplish this goal?
An engineer must add a group of 70 bare-metal ESXi servers to the Cisco ACI fabric, which is integrated with vCenter. These configuration steps are complete:
The configured pool of ESXi hosts is configured with an Attachable Access Entity Profile (AAEP) called AEP_VMM.
The new group uses the AAEP called AEP_BAREMETAL.
Which action extends functional VMM integration to the new nodes?
What do Pods use to allow Pod-to-Pod communication in a Cisco ACI Multi-Pod environment?
What is a characteristic of a Cisco ACI Multi-Pod?
A Cisco ACI bridge domain and VRF are configured with a default data-plane learning configuration. Which two endpoint attributes are programmed in the leaf switch when receiving traffic? (Choose two.)
In a Cisco ACI Multi-Site fabric, the Inter-Site BUM Traffic Allow option is enabled in a specific stretched bridge domain. What is used to forward BUM traffic to all endpoints in the same broadcast domain?
A data center administrator is upgrading an ACI fabric. There are 3 APIC controllers in the fabric and all the servers are dual-homed to pairs of leaf switches configured in VPC mode. How should the fabric be upgraded to minimize possible traffic impact during the upgrade?

What is MP-BGP used for in Cisco ACl fabric?
Cisco ACI fabric must detect all silent endpoints for the Layer 3 bridge domain. Which actions accomplish this goal?
A network engineer must configure a Cisco ACI system to detect network loops for untagged and tagged traffic The loop must be detected and slopped by disabling an interface within 4 seconds Which configuration must be used?

A customer migrates a legacy environment to Cisco ACI. A Layer 2 trunk is configured to interconnect the two
environments. The customer also builds ACI fabric in an application-centric mode. Which feature should be
enabled in the bridge domain to reduce instability during the migration?
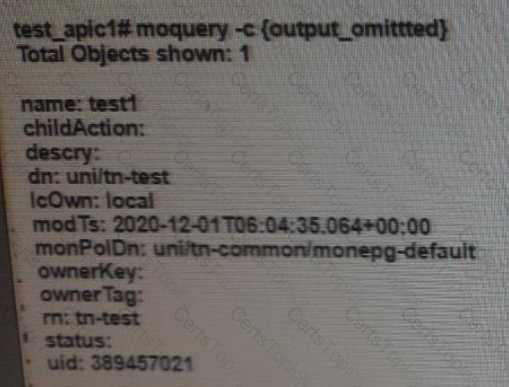
Which class of ACI object is presented in this output?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
Refer to the exhibit.
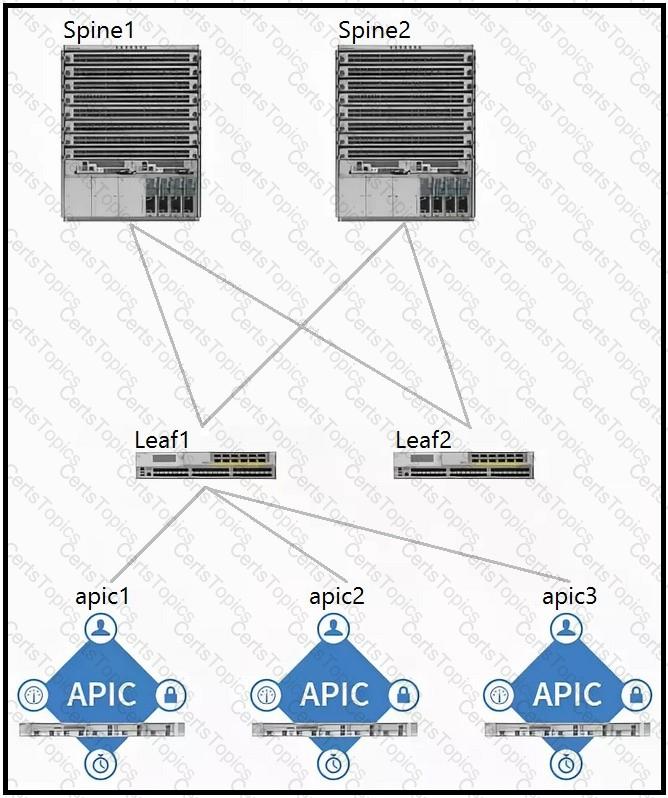
Which two components should be configured as route reflectors in the ACI fabric? (Choose two.)
Which two statements regarding ACI Multi-Site are true? (Choose two.)
Cisco ACI fabric is integrated with a VMware environment. The engineer must back up the current configuration of the fabric and restore the vCenter password when the configuration is ... Which action accomplishes this goal?
Which tenant is used when configuring in-band management IP addresses for Cisco APICs, leaf nodes, and spine nodes?
A customer creates Layer 3 connectivity to the outside network. However, only border leaf switches start receiving destination updates to other networks from the newly created L3Out. The updates must also be propagated to other Cisco ACI leaf switches. The L3Out is linked with the EPGs via a contract. Which action must be taken in the pod policy group to accomplish this goal?
Which type of port is used for in-band management within ACI fabric?
Which components must be configured for the BGP Route Reflector policy to take effect?
An engineer must advertise a bridge domain subnet out of the ACI fabric to an OSPF neighbor. Which two configuration steps are required? (Choose two.)
Refer to the exhibit.
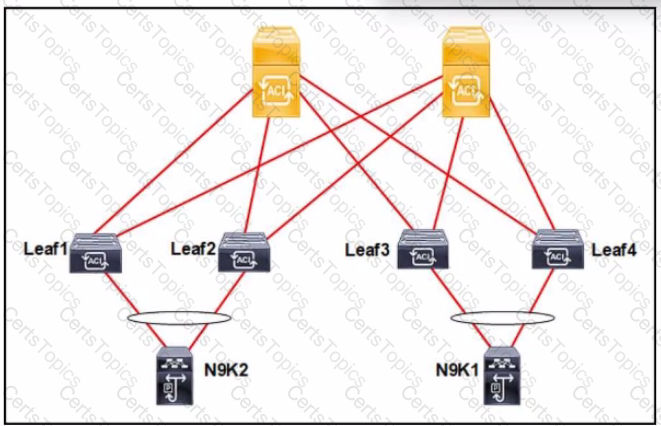
The Cisco ACI fabric is built with L20ut to the N9K1 and N9K2 switches. The switches run the RSTP protocol. The requirement is for the Cisco ACI fabric to detect 5 from the N9K and for the fabric to be protected against loops. Which set of actions must be taken to meet the requirements?
What are two descriptions of ACI multi-site? (Choose two.)
Cisco ACI fabric contains a tenant called Prod. User_1 must have write access to tenant Prod and full access to the fabric access policy. Which set of actions must be taken to meet these requirements?

Refer to the exhibit. An engineer created a local user named User on Cisco ACI. The engineer must configure the fabric so that the User can access only common and PROD tenants, ch set of actions accomplishes the goal?
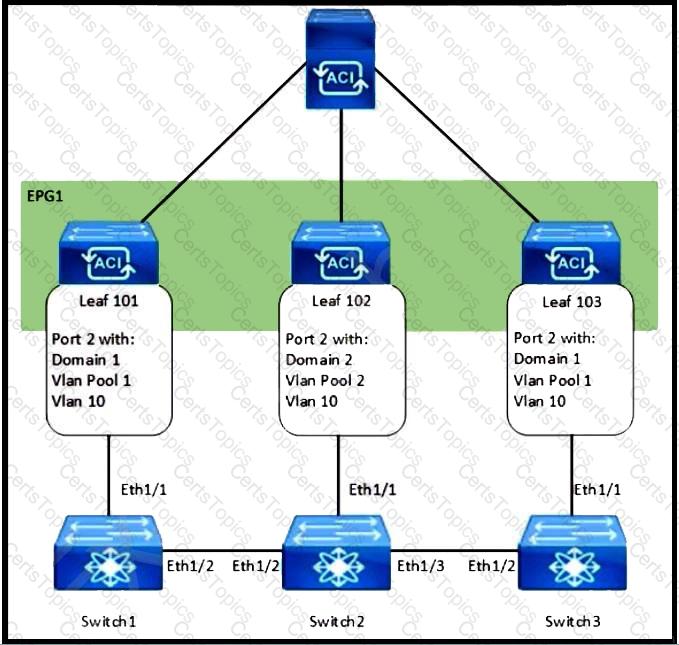
Refer to the exhibit. How are the STP BPDUs forwarded over Cisco ACI fabric?
An engineer wants to monitor all configuration changes, threshold crossing, and link-state transitions in a Cisco ACI fabric. Which action must be taken to receive the required messages?
An engineer must deploy Cisco ACI across 10 geographically separated data centers. Which ACI site deployment feature enables the engineer to control which bridge domains contain Layer 2 flooding?
Cisco ACI fabric must send a packet between two pods in a Cisco AC1 Multi-Pod topology where ARP flooding is disabled within the bridge domain. How does a Cisco ACI spine switch .. ARP messages from a leaf switch in POD1 to POD2?
A company is implementing a new security policy to track system access, configuration, and changes. The network engineer must enable the log collection to track user login and logout attempts. In addition, any configuration changes such as a fabric node failure must be collected in the logs. The syslog policy is configured to send logs to the company SEIM appliance.
Which two log types must be enabled to meet the security requirements? (Choose two.)
Refer to the exhibit.
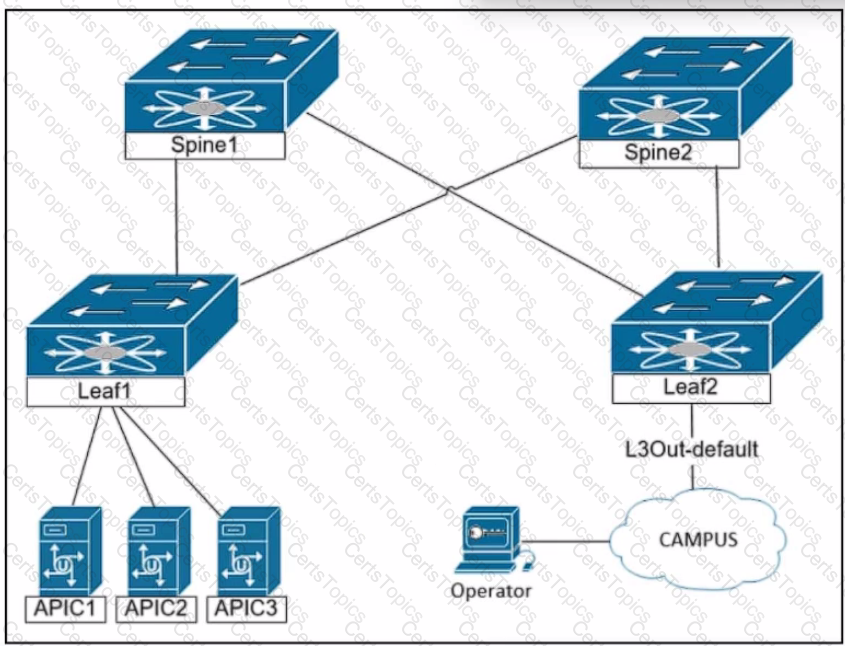
The engineer is planning to configure in-band management for the Cisco ACI fabric. The goal is to allow the network operators to reach the Cisco APIC servers and fabric switches from the in-band network. Which configuration must be applied on the bridge domain to accomplish these goals?
A network engineer must configure a new SNMP configuration and syslog servers. The requirement is for all faults and events related to endpoint groups, bridge domains, and VRFs to be sent to it. Which action must be taken to meet the requirements?
Refer to the exhibit.
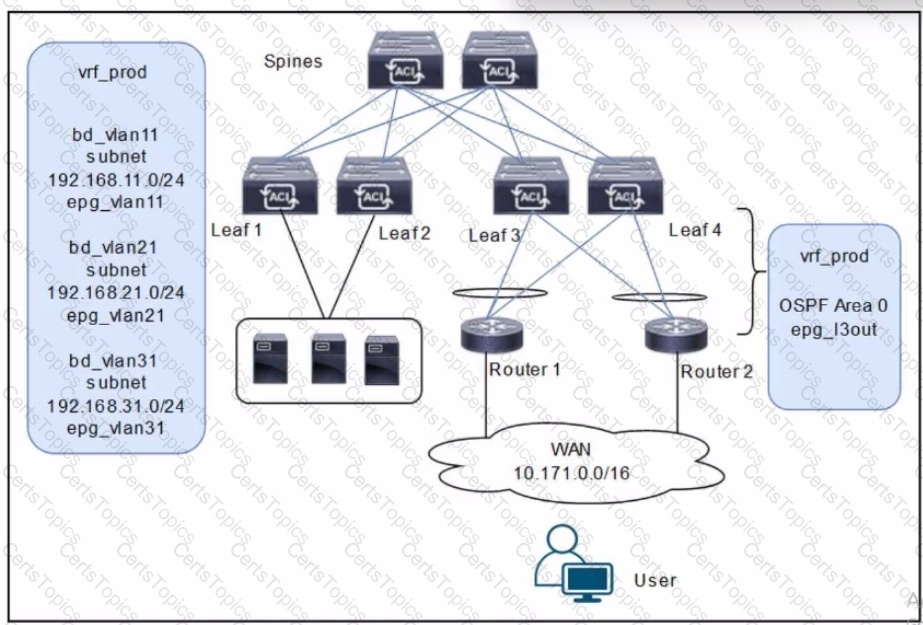
A customer is deploying a WAN with these requirements: •Routers 1 and 2 must receive only routes 192.168.11.0/24 and 192.168.21.0724 from the Cisco ACI fabric •Reachability to the WAN users must be permitted only for the servers that are located in vrf_prod.
Which settings must be configured to meet these objectives?
An engineer configured a bridge domain with the hardware-proxy option for Layer 2 unknown unicast traffic. Which statement is true about this configuration?
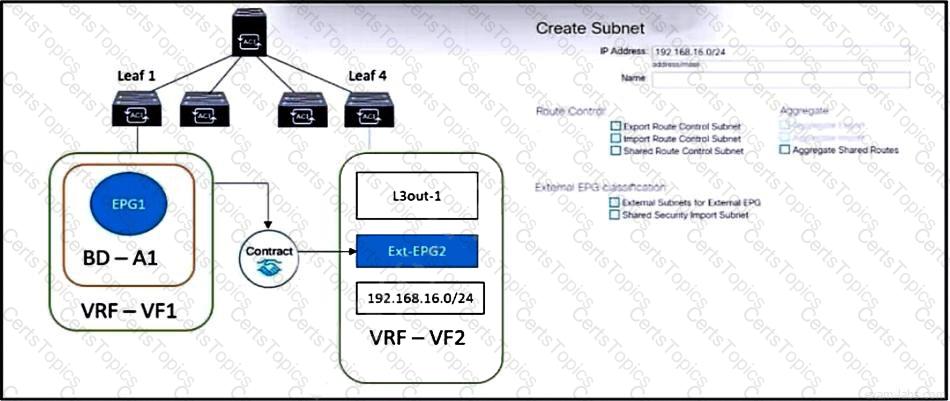
Refer to the exhibit. The external subnet and internal EPG1 must communicate with each other, and the L3Out traffic must leak into the VRF named "VF1". Which configuration set accomplishes these goals?
An engineer must configure VMM domain integration on a Cisco UCS B-Series server that is connected to a Cisco ACI fabric. Drag and drop the products used to create VMM domain from the bottom into the sequence in which they should be implemented at the top. Products are used more than once.
An engineer created a monitoring policy called Test in a Cisco ACI fabric and had to change the severity level of the monitored object Call home source. Which set of actions prevent the event from appearing in event reports?
A network administrator configures AAA inside the Cisco ACI fabric. The authentication goes through the local users if the TACACS+ server is not reachable. If the Cisco APIC is out of the cluster, the access must be granted through the fallback domain. Which configuration set meets these requirements?
Network engineer configured a Cisco ACI fabric as follows:
• An EPG called EPG-A is created and associated with a VMM domain called North. •The EPG-A is associated with BD-A and is in an application profile called Apps-A.
• The BD-A is associated with VRF-1 in the Prod tenant.
Which port group must be selected to place VMs in EPG-A?
Which action sets Layer 2 loop migration in an ACI Fabric with a Layer 2 Out configured?
When does the Cisco ACI leaf learn a source IP or MAC as a remote endpoint?
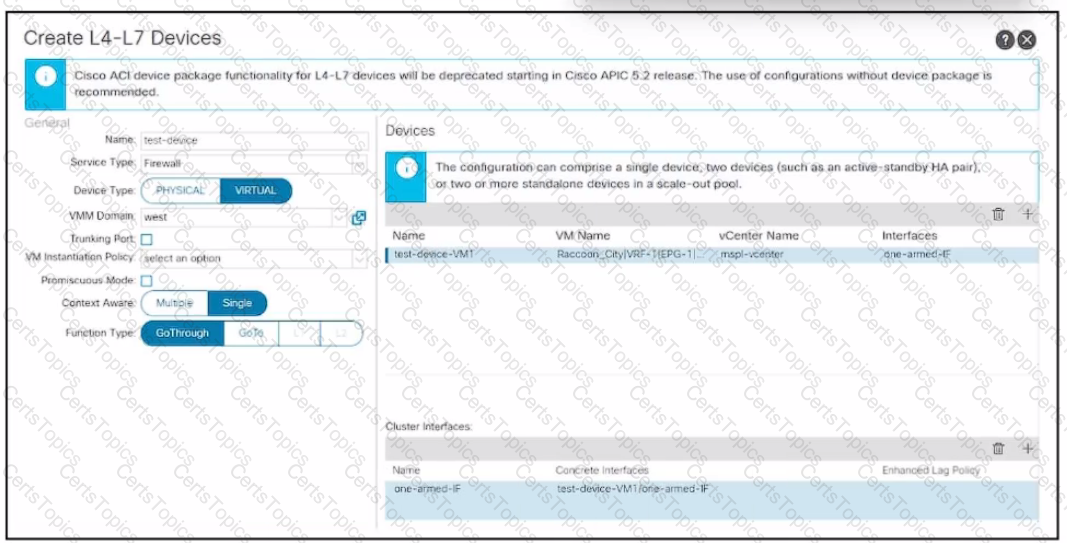
Refer to the exhibit. An engineer configures a Layer 4 to Layer 7 device object. The device is a virtual firewall with a single network adapter and it must be deployed in routed mode. Which .. completes the configuration of the device object?
A network engineer demonstrates Cisco ACI to a customer. One of the test cases is to validate a disaster
recovery event by resetting the ACI fabric to factory and then restoring the fabric to the state it was in before
the event. Which setting must be enabled on ACI to export all configuration parameters that are necessary to
meet these requirements?
When configuring Cisco ACI VMM domain integration with VMware vCenter, which object is created in vCenter?
Refer to the exhibit.
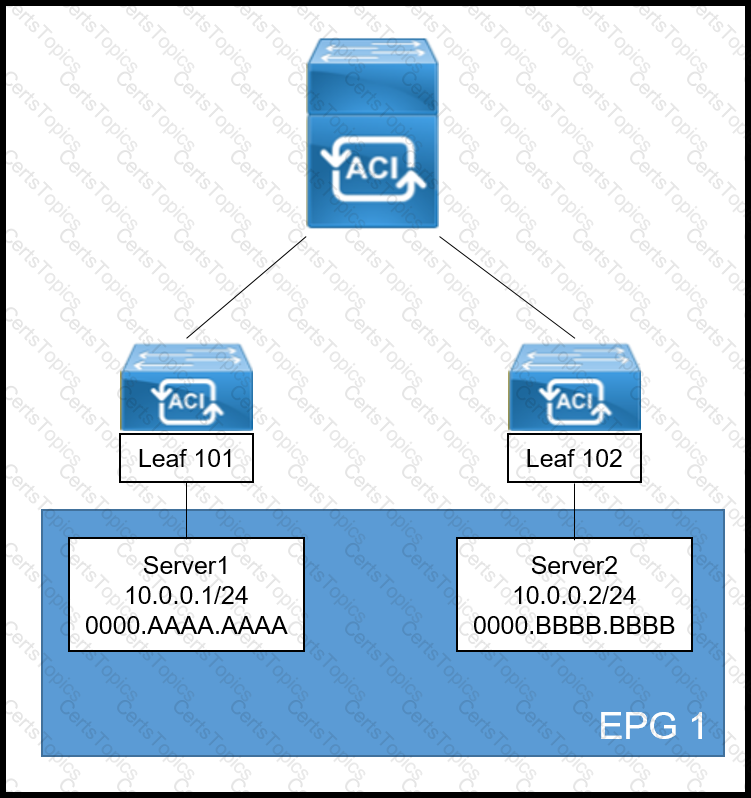
A systems engineer is implementing the Cisco ACI fabric. However, the Server2 information is missing from the Leaf 101 endpoint table and the COOP database of the spine. The requirement is for the bridge domain configuration to enforce the ACI fabric to forward the unicast packets generated by Server1 destined to Server2. Which action must be taken to meet these requirements?
What must be enabled in the bridge domain to have the endpoint table learn the IP addresses of endpoints?
What two actions should be taken to deploy a new Cisco ACI Multi-Pod setup? (Choose two.)
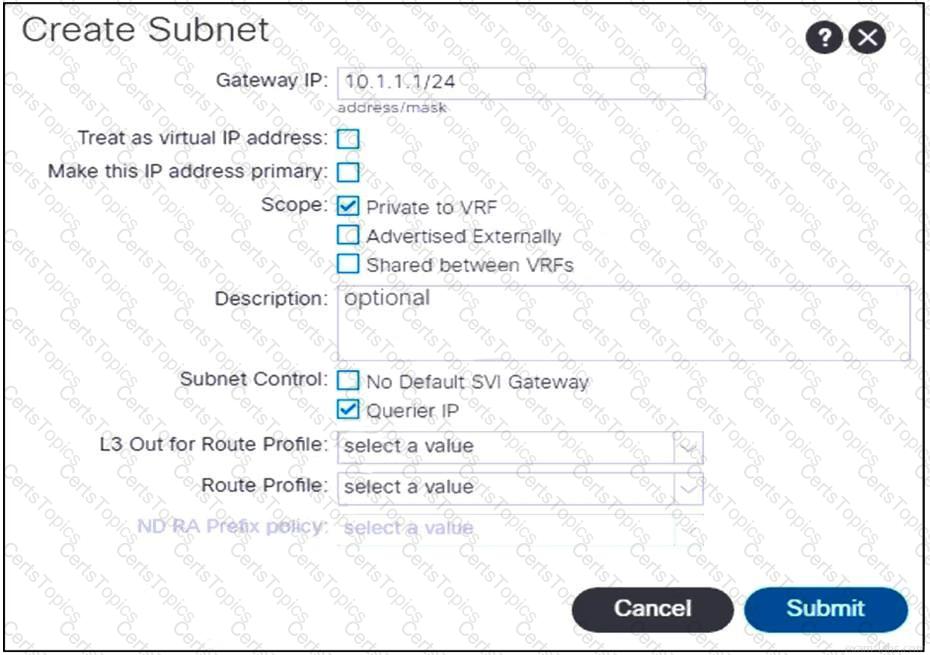
Refer to the exhibit. An engineer configures communication between the EPGs in different tenants. Which action should be taken to create the subnet?
The existing network and ACI fabric have been connected to support workload migration. Servers will physically terminate at the Cisco ACI, but their gateway must stay in the existing network. The solution needs to adhere to Cisco’s best practices. The engineer started configuring the relevant Bridge Domain and needs to complete the configuration. Which group of settings are required to meet these requirements?
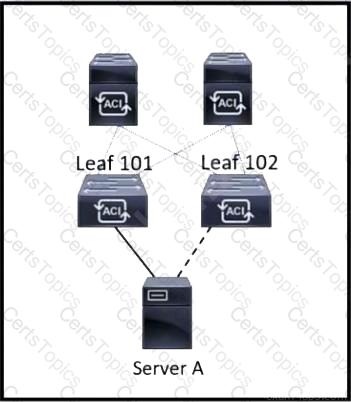
Refer to the exhibit. Server A is connected to the Cisco ACI fabric using two teamed interfaces. One interface in a team is configured as active and the other remains in standby mode. When a failover occurs and the standby interface becomes active, it uses its built-in MAC address to send traffic. Which bridge domain configuration must be applied to resolve the issue?
Which method does the Cisco ACI fabric use to load-balance multidestination traffic?
Which new construct must a user create when configuring in-band management?
Refer to the exhibit.
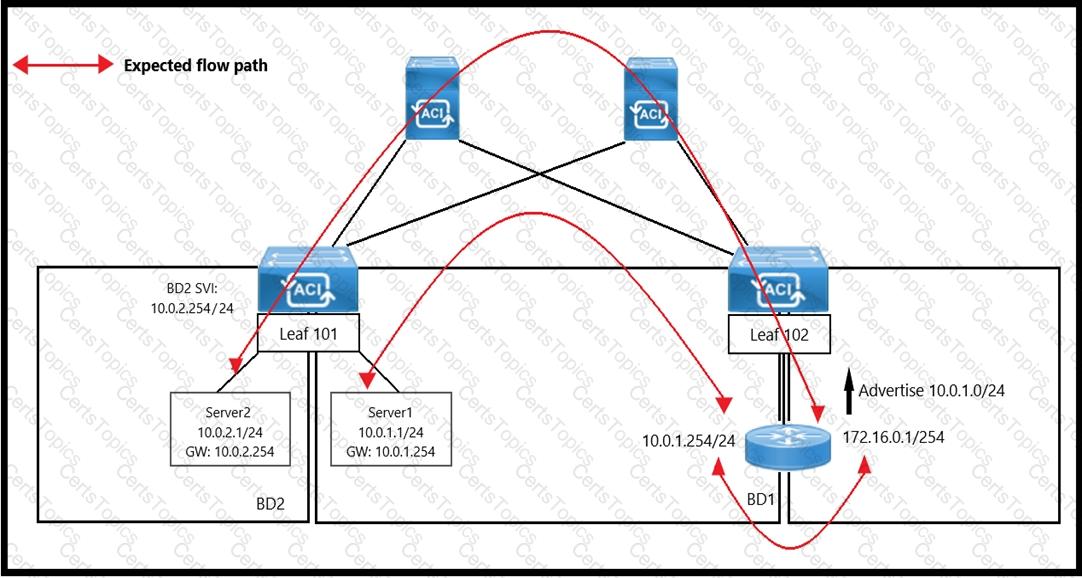
An engineer wants to initiate an ICMP ping from Server1 to Server2. The requirement is for the BD1 to enforce ICMP replies that follow the expected path. The packets must be prevented from taking the direct path from Leaf1 to Server1. Which action must be taken on BD1 to meet these requirements?
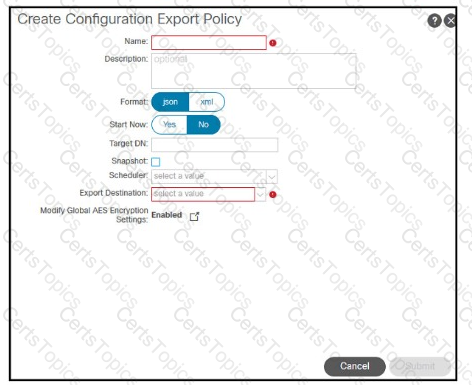
Refer to the exhibit A customer must back up the current Cisco ACl configuration securely to the remote location using encryption and authentication. The backup job must run once per day The customer s security policy mandates that any sensitive information including passwords, must not be exported from the device Which set of steps meets these requirements?

What must be configured to redistribute externally learned OSPF routes within the ACI fabric?
A customer is deploying a new application across two ACI pods that is sensitive to latency and jitter. The application sets the DSCP values of packets to AF31 and CS6, respectively. Which configuration changes must be made on the APIC to support the new application and prevent packets from being delayed or dropped between pods?
What is the effect of enabling the disable Remote EP learn feature?
What are two requirements for the IPN network when implementing a Multi-Pod ACI fabric? (Choose two.)
Refer to the exhibit.
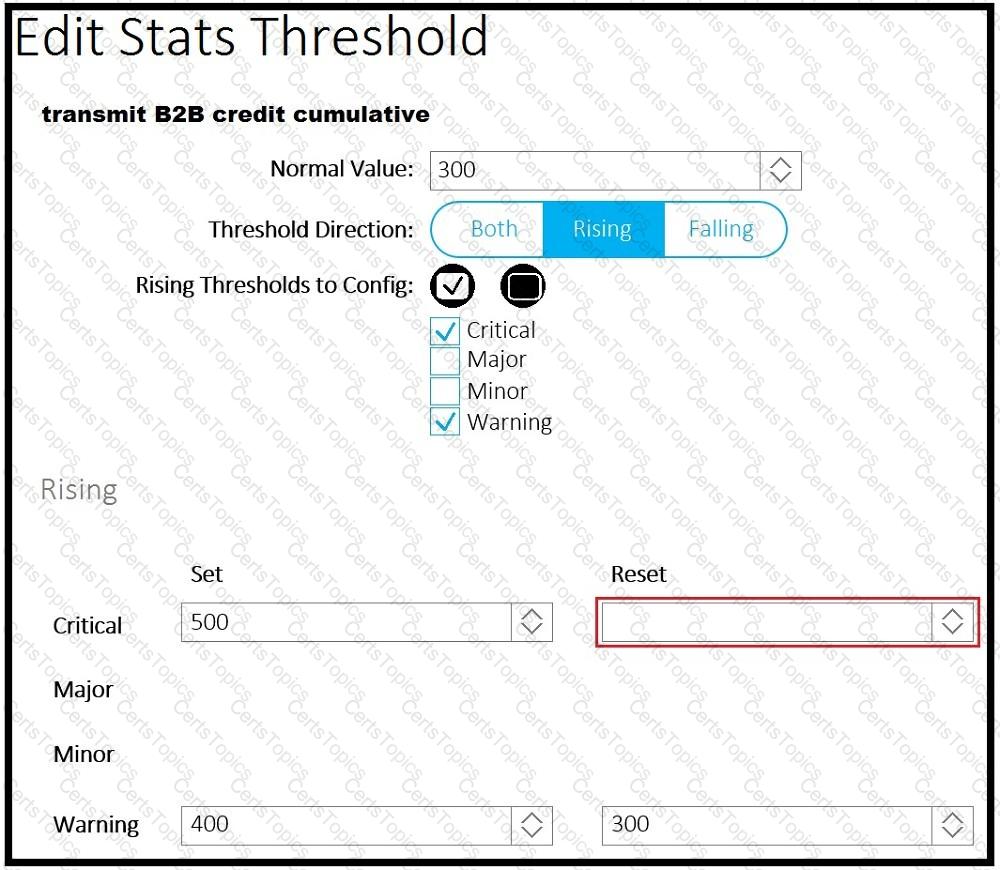
A client reports that the ACI domain connectivity to the fiber channel storage is experiencing a B2B credit oversubscription. The environment has a SYSLOG server for state collection messages. Which value should be chosen to clear the critical fault?